【09】ServiceEntry使用案例
2023-12-19 07:16:17
案例背景
- 为了便于测试,我们用非网格化的名称空间中运行的应用来模拟运行于VM/萝服务上的外部服务,假设:
- 在网格外部运行nginx服务,有2个实例
- Nginx2001:监听地址为172.29.1.201:8091,nginx版本为1.20
- nginx2002:监听地址为172.29.1.202:8091,nginx版本为1.20、
- 网格内部default名称空间中的pods/client作为客户端访问该服务
- 在网格外部运行nginx服务,有2个实例
- 请求测试
- 未启用serviceEntry,客户端的请求目标在网格中不存匹配的listener等,因此将由sidercar Envoy通过tcp proxy透传到指定的外部服务
- 这种透传机制,依赖于Sidercar Envoy的默认策略为ALLOW_ANY
案例环境设置
-
环境设置
k8s-master 192.168.170.134 node01 192.168.170.136 node02 192.168.170.133 nginx 192.168.170.137 -
nginx采用docker-compose部署,必须在nginx机器的ens33网卡上绑定几个ip
192.168.170.100 192.168.170.101 192.168.170.102
环境部署
首先将nginx部署在nginx机器,部署方式为docker-compose
version: '3.3'
services:
nginx2001:
image: nginx:1.20-alpine
volumes:
- ./html/nginx2001:/usr/share/nginx/html/
networks:
envoymesh:
ipv4_address: 172.31.201.11
aliases:
- nginx
expose:
- "80"
ports:
- "192.168.170.100:8091:80"
nginx2002:
image: nginx:1.20-alpine
volumes:
- ./html/nginx2002:/usr/share/nginx/html/
networks:
envoymesh:
ipv4_address: 172.31.201.12
aliases:
- nginx
expose:
- "80"
ports:
- "192.168.170.101:8091:80"
nginx2101:
image: nginx:1.21-alpine
volumes:
- ./html/nginx2101:/usr/share/nginx/html/
networks:
envoymesh:
ipv4_address: 172.31.201.13
aliases:
- nginx
- canary
expose:
- "80"
ports:
- "192.168.170.102:8091:80"
networks:
envoymesh:
driver: bridge
ipam:
config:
- subnet: 172.31.201.0/24
启动
docker-compose up

-
创建VirtualService和DestinationRule,为ServiceEntry的流量配置高级路由规则
apiVersion: networking.istio.io/v1beta1 kind: VirtualService metadata: name: nginx-external spec: hosts: - nginx.icloud2native.com http: - name: falut-injection match: - headers: X-Testing: exact: "true" route: - destination: host: nginx.icloud2native.com fault: delay: percentage: value: 5 fixedDelay: 2s abort: percentage: value: 5 httpStatus: 555 - name: nginx-external route: - destination: host: nginx.icloud2native.comapiVersion: networking.istio.io/v1beta1 kind: DestinationRule metadata: name: nginx-external spec: host: nginx.icloud2native.com trafficPolicy: loadBalancer: consistentHash: httpHeaderName: X-User connectionPool: tcp: maxConnections: 10000 connectTimeout: 10ms tcpKeepalive: time: 7200s interval: 75s http: http2MaxRequests: 1000 maxRequestsPerConnection: 10 outlierDetection: maxEjectionPercent: 50 consecutive5xxErrors: 5 interval: 2m baseEjectionTime: 1m minHealthPercent: 40
测试
进入到sleep这个容器进行访问
while true; do curl -H 'host: nginx.icloud2native.com' 192.168.170.100:8091;sleep 0.$RANDOM; done
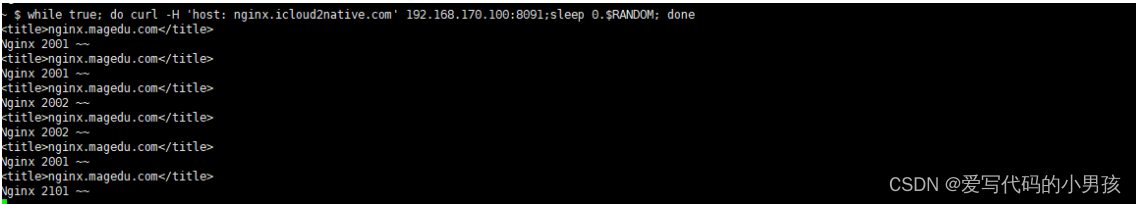
while true; do curl -H 'host: nginx.icloud2native.com' -H "X-Testing: true" 192.168.170.100:8091;sleep 0.$RANDOM; done
会发现定义的vs规则生效,有一部分已经注入故障,在kiali上查看:

文章来源:https://blog.csdn.net/weixin_38753143/article/details/135067896
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!