python小工具之弱密码检测工具
一、引用的python模块
Crypto:
Python中一个强大的加密模块,提供了许多常见的加密算法和工具。它建立在pyc.ypodome或pyc.ypto等底层加密库之上,为Python程序员提供了简单易用的API,使其可以轻松地实现各种加密功能。
commands:
commands 模块是 Python 的内置模块,它主要有三个函数:
FUNCTIONS
getoutput(cmd)
Return output (stdout or stderr) of executing cmd in a shell.getstatus(file)
Return output of "ls -ld <file>" in a string.getstatusoutput(cmd)
Return (status, 'output) of executing cmd in a shell.
SYS: 基础系统模块
sys模块是与python解释器交互的一个接口。sys 模块提供了许多函数和变量来处理 Python 运行时环境的不同部分。
二、实现过程
python脚本如下:
import crypt
import commands
import sysdef testPass(user,cryptPass,ipaddr):
?? ?#dictfile=open('dictionary.txt','r')
?? ?start_index=cryptPass.find("$")
?? ?finish_index=cryptPass.rfind("$")
?? ?salt=cryptPass[start_index:finish_index+1]
?? ?dictfile=open('/root/dict.txt','r')
?? ?pwd_suffix = ['','.','..','!','!@#','1','123','1234','12345','123456','888','666','999','2006','2007','2008','2009','2010','2011','2012','2013','2014','2015','2016','2017','2018','2019']
?? ?for sfx in pwd_suffix:
?? ??? ?#print user+sfx
?? ??? ?for separator in ['','@','#','&']:
?? ??? ??? ?cryptWord=crypt.crypt('%s%s%s'%(user,separator,sfx),salt)
?? ??? ??? ?if cryptWord==cryptPass:
?? ??? ??? ??? ?#print ipaddr + " [+] Found Password: " +user+'/'+user+sfx+ " \n"
?? ??? ??? ??? ?print '%s [+] Found Passwd: %s/%s%s%s \n'%(ipaddr,user,user,separator,sfx)
?? ??? ??? ??? ?break
?? ??? ??? ?cryptWord=crypt.crypt('%s%s%s'%(user,sfx,separator),salt)
?? ??? ??? ?if cryptWord==cryptPass:
?? ??? ??? ??? ?#print ipaddr + " [+] Found Password: " +user+'/'+user+sfx+ " \n"
?? ??? ??? ??? ?print '%s [+] Found Passwd: %s/%s%s%s \n'%(ipaddr,user,user,sfx,separator)
?? ??? ??? ??? ?break
?? ?for word in dictfile.readlines():
?? ??? ?#print word
?? ??? ?word=word.strip()
?? ??? ?cryptWord=crypt.crypt(word,salt)
?? ??? ?if cryptWord==cryptPass:
?? ??? ??? ?print ipaddr + " [+] Found Password: " +user+'/'+word+ " \n"
?? ??? ??? ?break
?? ?print('[-] Password not found!')def main():
?? ?cmd = "ifconfig|grep \"inet addr\"|grep -v 127.0.0.1|awk '{print $2}'"
?? ?ipaddr = commands.getoutput(cmd).replace('addr:','').replace('\n','|')
?? ?shadowfile=open('/etc/shadow')
?? ?for line in shadowfile.readlines():
?? ??? ?user=line.split(':')[0]
?? ??? ?cryptPass=line.split(':')[1].strip('\n')
?? ??? ?if not (cryptPass.startswith('*') or cryptPass.startswith('!')):?
?? ??? ??? ?print "[*] Cracking Password For: " +user
?? ??? ??? ?testPass(user,cryptPass,ipaddr)if __name__=='__main__':
?? ?main()
注:破解密码有两种方式,一种是通过脚本pwd_suffix定义的后缀,另一种是调用密码字典库(/root/dict.txt)来破解。
三、演示效果
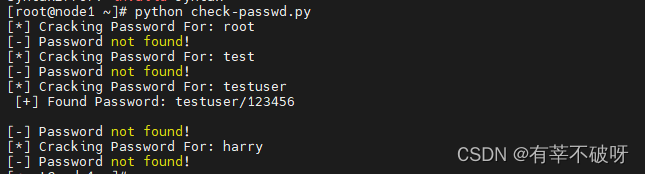
创建一个测试用户testuser,密码设置成123456,然后执行检测脚本。滴,弱密码已被发现!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!