iptables(二)
文章目录
1. 防火墙
1.1 防火墙种类及使用说明
- 硬件: 整个企业入口
- 三层路由: H3C 华为 Cisco(思科)
- 深信服
- Juniper
- 软件: 开源软件 网站内部 封ip 封ip
- iptables 写入到Linux内核中 以后服务docker
- firewalld C7
- 云防火墙
- 阿里云:安全组
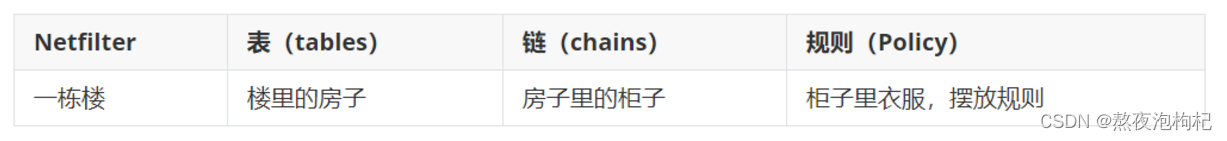
1.2 必须熟悉的名词
容器: 瓶子 罐子 存放东西
表(table): 存放链的容器
链(chain): 存放规则的容器
规则(policy): 准许或拒绝规则
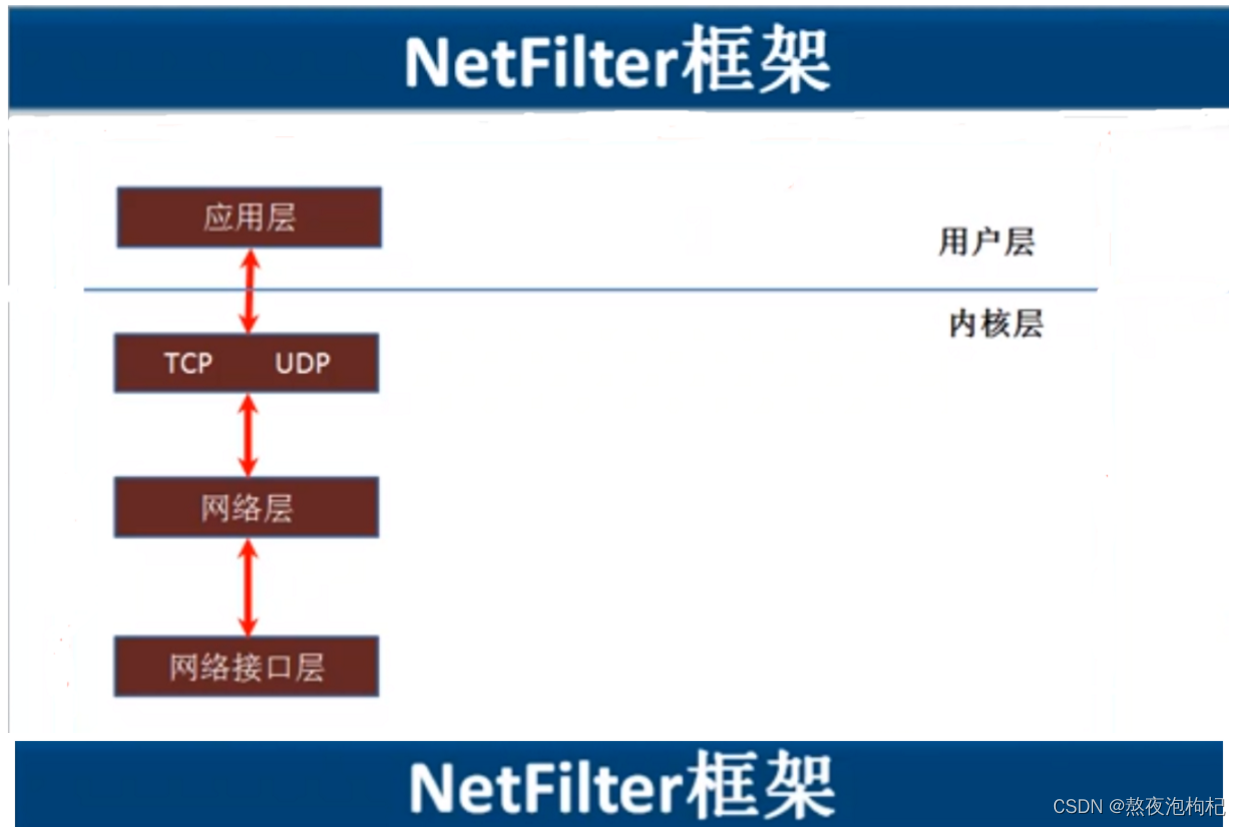
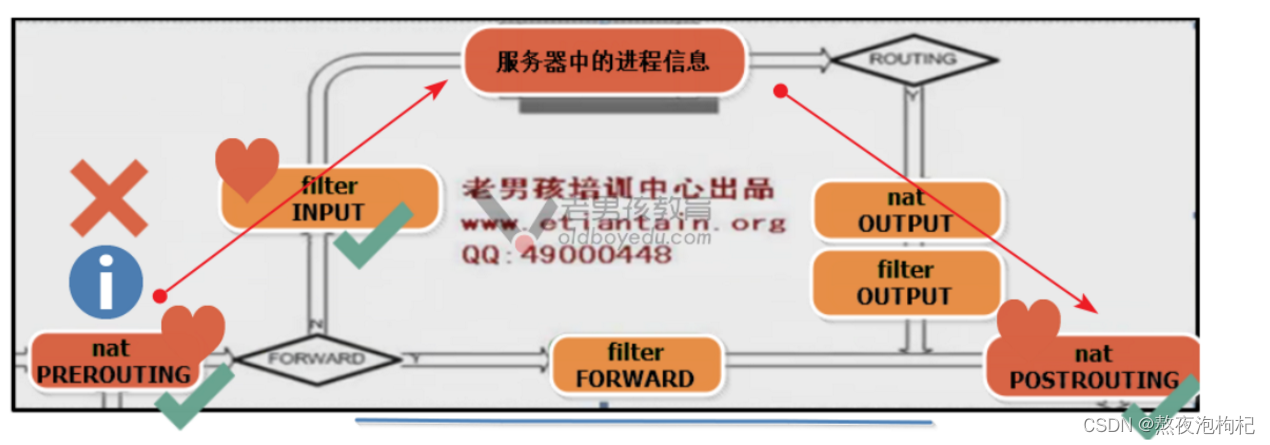
1.3 iptables 执行过程
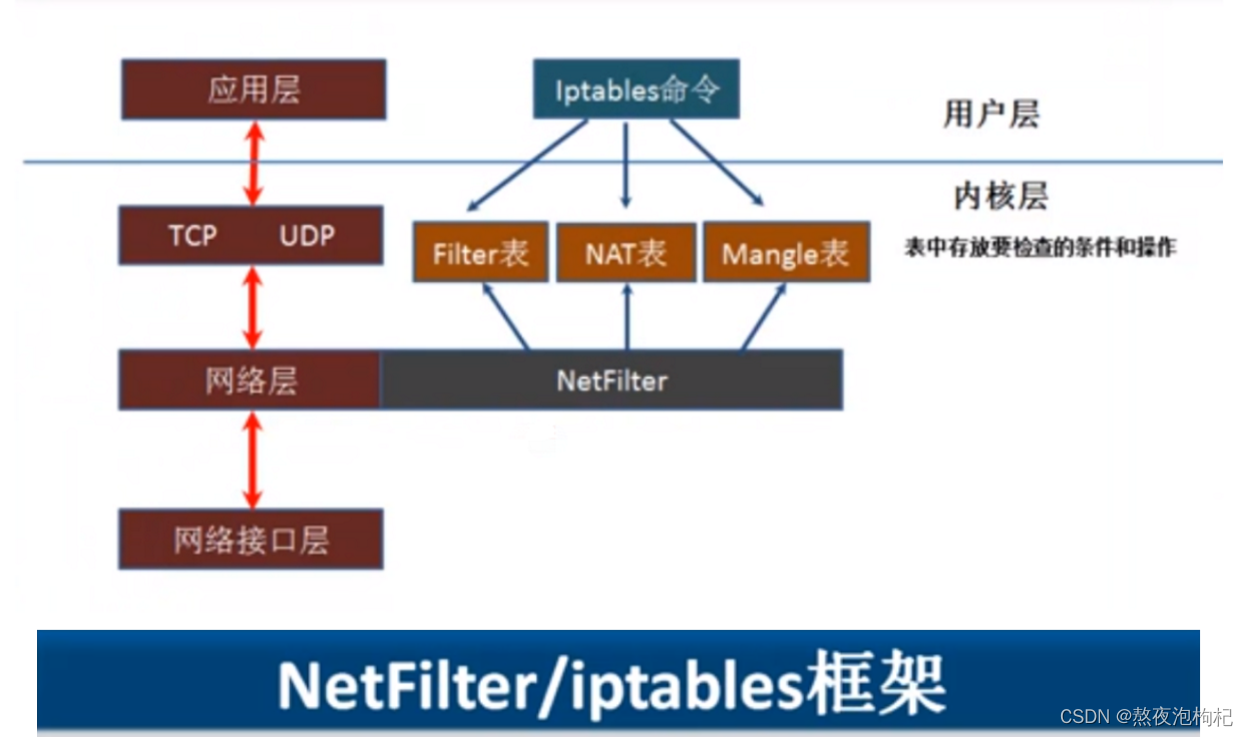
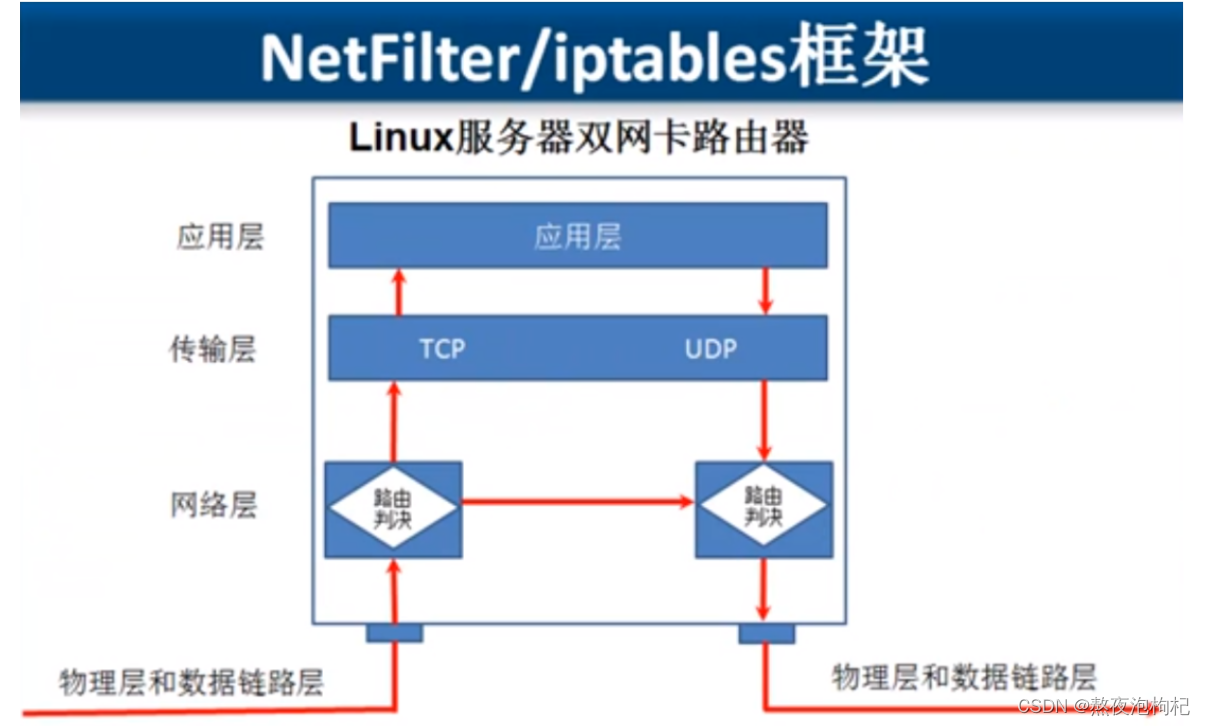
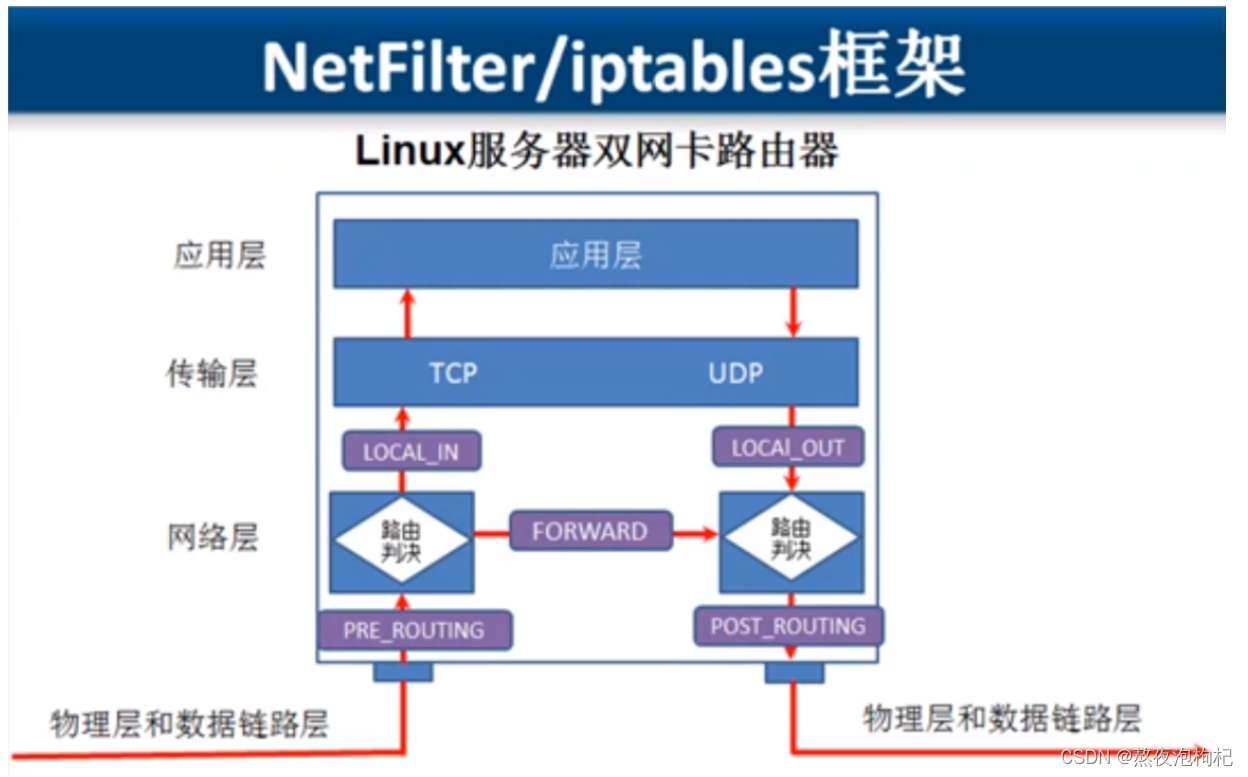
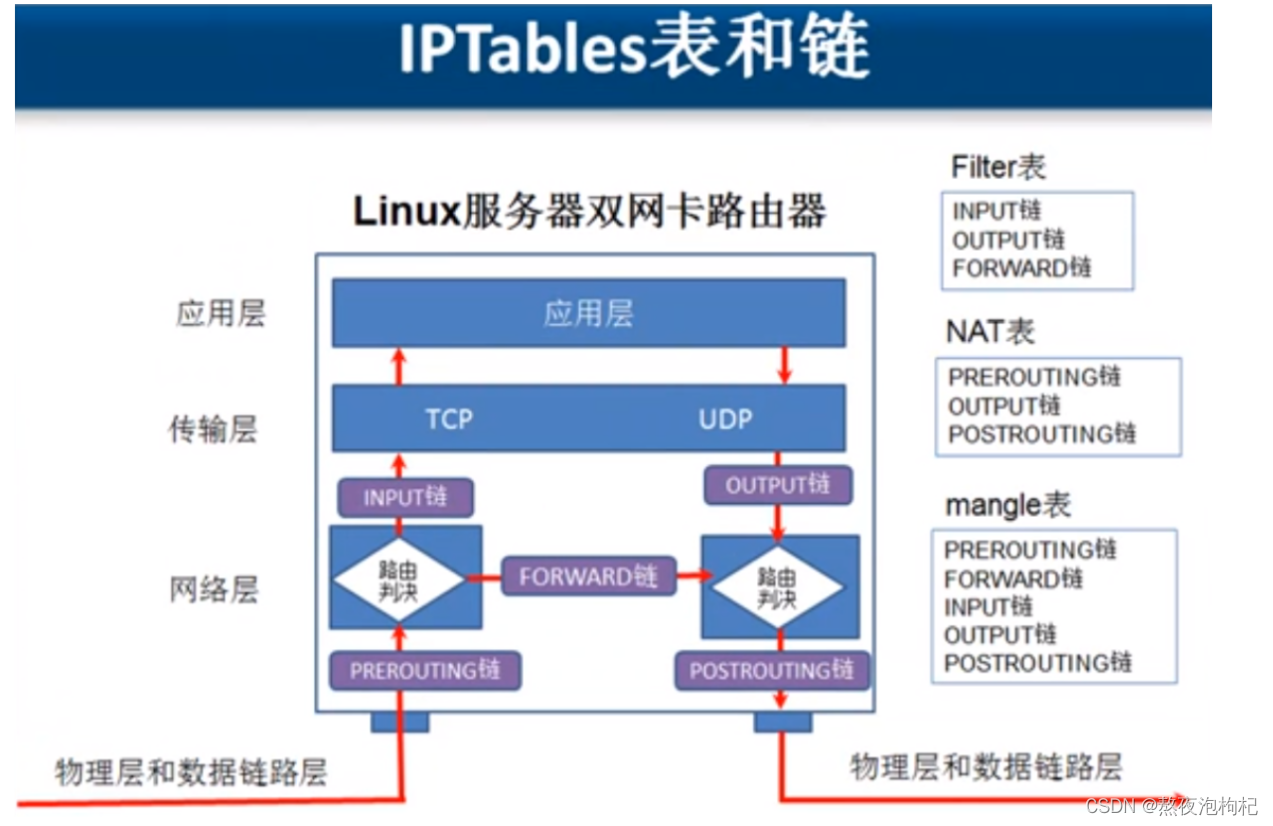
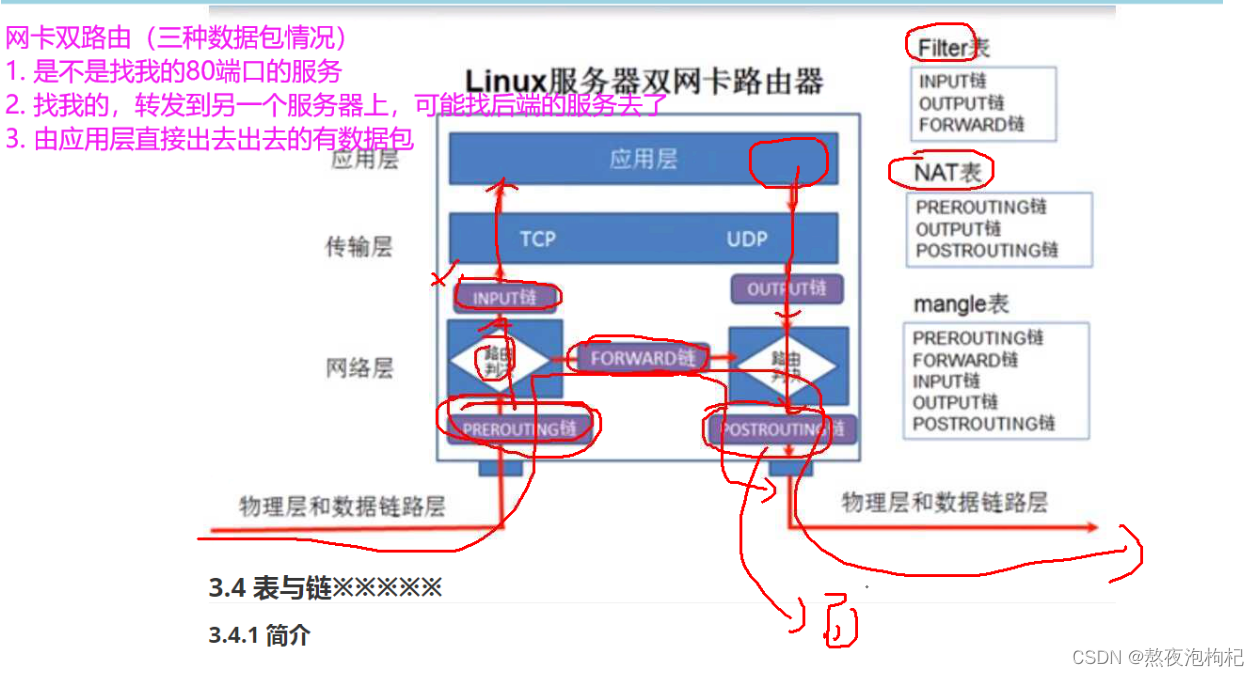
1.4 表与链
1.4.1 简介
iptables 是 4表伍链
4表: filter 表 nat表 raw表 mangle表
伍链: INPUT OUTPUT FORWARD PREROUTING POSTROUTING
1.4.2 每个表的说明
(1) filter表
防火墙: 屏蔽或准许 端口 ip
| filter表 | 强调:主要和主机自身相关,真正负责主机防火墙功能的(过滤流入流出主机的数据包) filter表示iptables默认使用的表,这个表定义了三个链(chains) 企业工作场景:主机防火墙 |
|---|---|
| INPUT | 负责过滤所有目标地址是本机地址的数据包 通俗来说:就是过滤进入主机的数据包 |
| FORWARD | 负责转发流经主机的数据包。起转发的作用,和NAT关系很大,后面会详细介绍 LVS NAT模式,net.ipv4.ip_forward=0 |
| OUTPUT | 处理所有源地址是本机地址的数据包 通俗的讲:就是处理从主机发出去的数据包 |
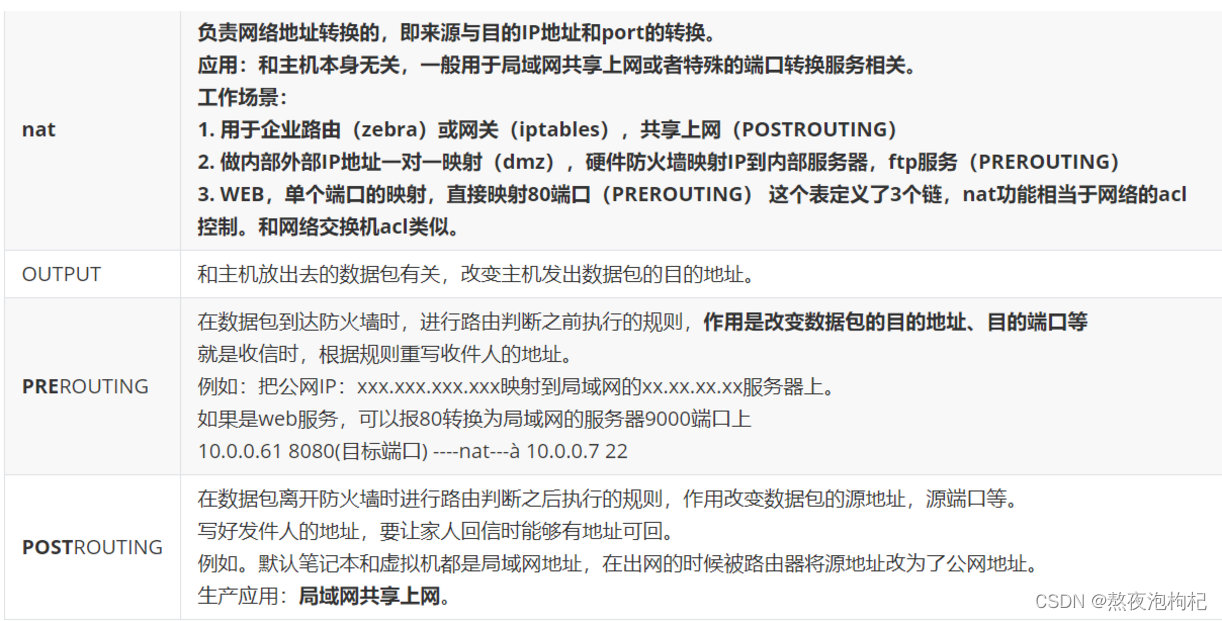
(2) nat表
- 实现nat功能
- 实现共享上网(内网服务器上外网)
- 端口映射和ip映射
1.5 环境准备及命令
iptables iptables启动或关闭的命令
m01 10.0.0.61 172.16.1.61
web01 10.0.0.7 172.16.1.7
yum install -y iptables-services
?
?
[root@oldboy-m01 ~]# uname -r
3.10.0-862.el7.x86_64
[root@oldboy-m01 ~]# yum install -y iptables-services
?
?
?
[root@m01 ~]# rpm -ql iptables-services
/etc/sysconfig/ip6tables
/etc/sysconfig/iptables #防火墙的配置文件
/usr/lib/systemd/system/ip6tables.service
/usr/lib/systemd/system/iptables.service #防火墙服务配置文件(命令)
?
#防火墙相关模块 加载到内核中
modprobe ip_tables
modprobe iptable_filter
modprobe iptable_nat
modprobe ip_conntrack
modprobe ip_conntrack_ftp
modprobe ip_nat_ftp
modprobe ipt_state
?
#永久
cat >>/etc/rc.local<<EOF
modprobe ip_tables
modprobe iptable_filter
modprobe iptable_nat
modprobe ip_conntrack
modprobe ip_conntrack_ftp
modprobe ip_nat_ftp
modprobe ipt_state
EOF
?
?
[root@m01 ~]# lsmod |egrep 'filter|nat|ipt'
nf_nat_ftp 12770 0
nf_conntrack_ftp 18638 1 nf_nat_ftp
iptable_nat 12875 0
nf_nat_ipv4 14115 1 iptable_nat
nf_nat 26787 2 nf_nat_ftp,nf_nat_ipv4
nf_conntrack 133053 6 nf_nat_ftp,nf_nat,xt_state,nf_nat_ipv4,nf_conntrack_ftp,nf_conntrack_ipv4
iptable_filter 12810 0
ip_tables 27126 2 iptable_filter,iptable_nat
libcrc32c 12644 3 xfs,nf_nat,nf_conntrack
?
[root@m01 ~]# systemctl stop firewalld
[root@m01 ~]# systemctl disable firewalld
[root@m01 ~]# systemctl start iptables.service
[root@m01 ~]# systemctl enable iptables.service
Created symlink from /etc/systemd/system/basic.target.wants/iptables.service to /usr/lib/systemd/system/iptables.service.
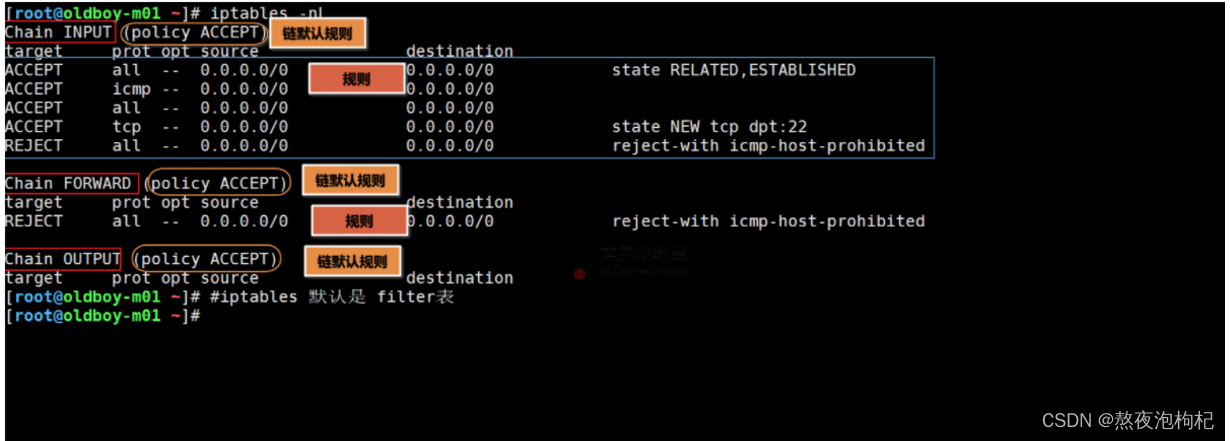
[root@m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
?
Chain FORWARD (policy ACCEPT)
target prot opt source destination
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
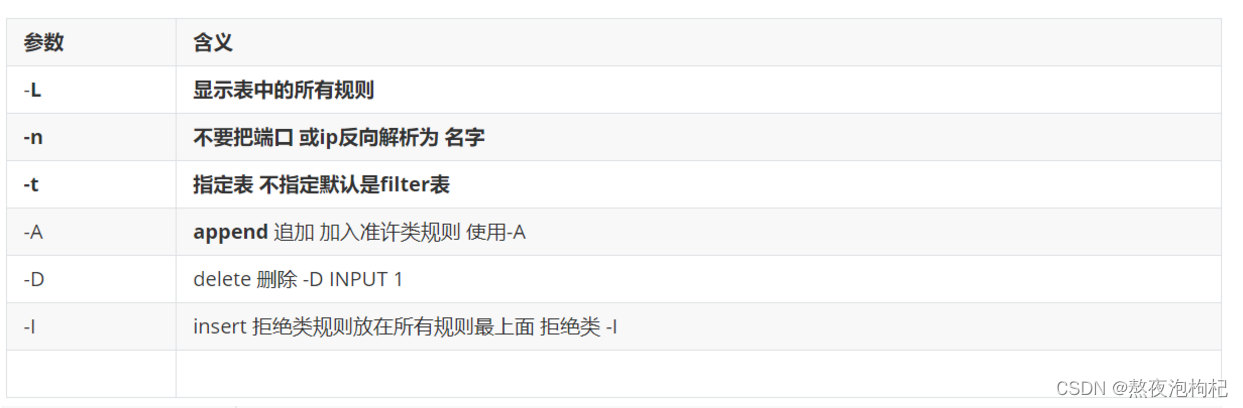
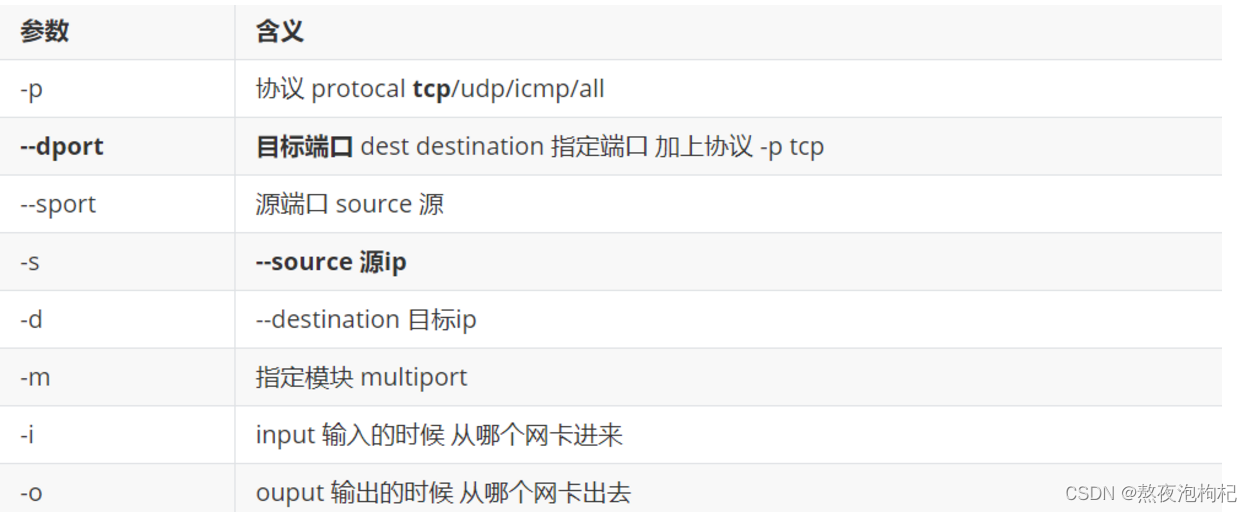
1.5.2 iptables命令参数
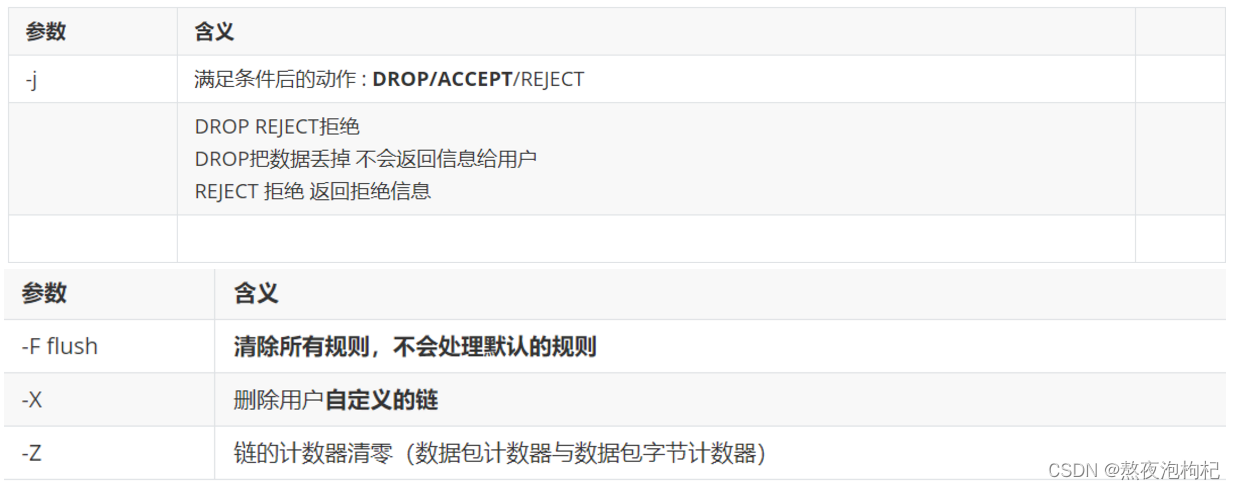
1.6 配置filter表规则
正式配置之前 先备份, 清空规则
[root@m01 ~]# iptables -F
[root@m01 ~]# iptables -X
[root@m01 ~]# iptables -Z
?
[root@m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
?
Chain FORWARD (policy ACCEPT)
target prot opt source destination
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
1.6.1 禁止访问22端口
iptables -t filter -I INPUT -p tcp --dport 22 -j DROP
删除 规则 -D
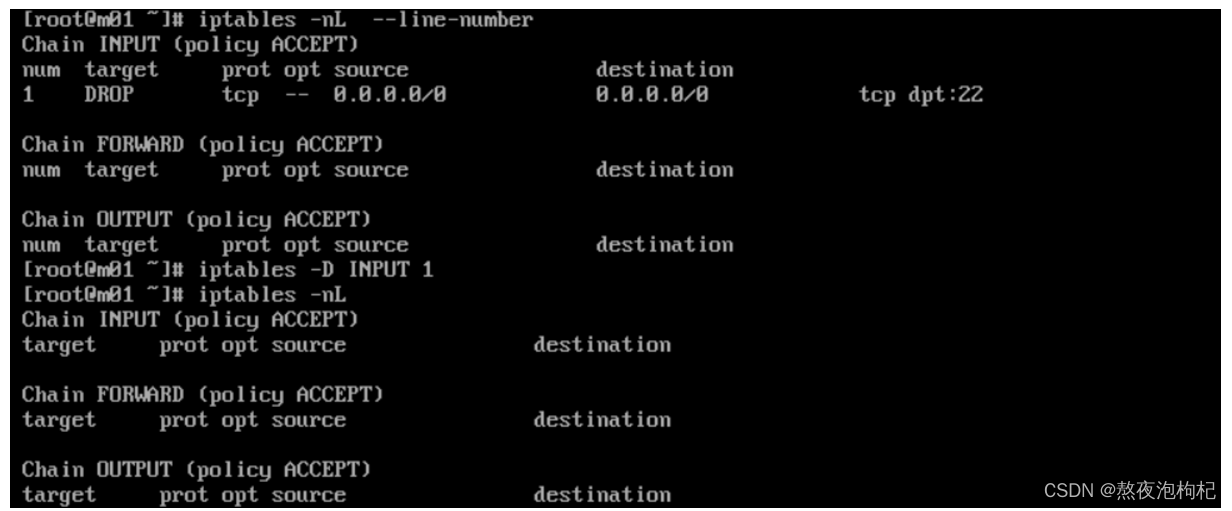
1.6.2 封ip 屏蔽某个ip
[root@oldboy-m01 ~]# iptables -I INPUT -s 10.0.0.7 -j DROP
[root@oldboy-m01 ~]# iptables -I INPUT -s 172.16.1.7 -j DROP
[root@oldboy-m01 ~]#
[root@oldboy-m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP all -- 172.16.1.7 0.0.0.0/0
DROP all -- 10.0.0.7 0.0.0.0/0
?
Chain FORWARD (policy ACCEPT)
target prot opt source destination
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
1.6.3 禁止网段连入(禁止10.0.0.0/24网段访问 8888端口)
nc ncat netcat
nc -l
telnet
iptables -I INPUT -s 10.0.0.0/24 -p tcp --dport 8 -j DROP
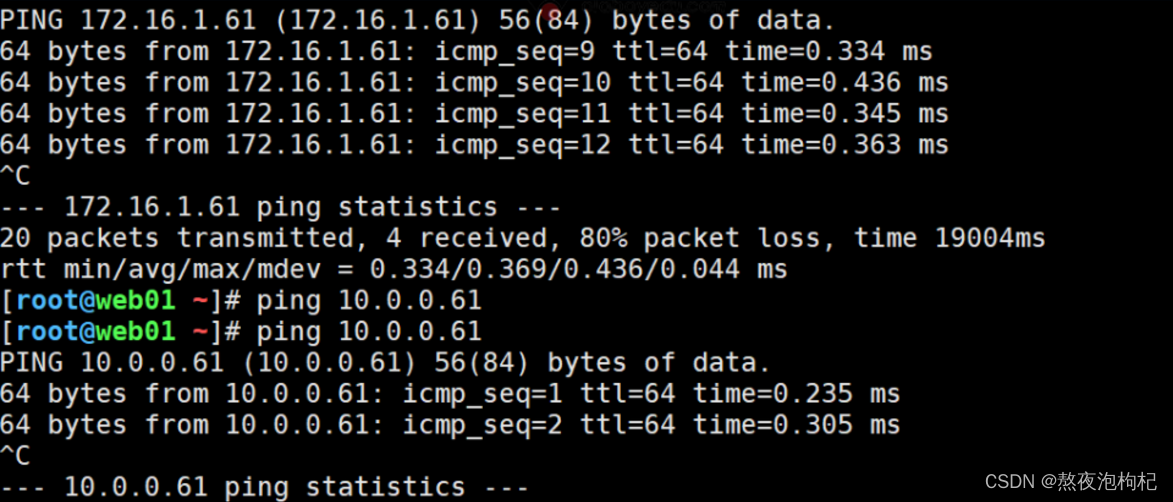
[root@web01 ~]# ssh 10.0.0.61 hostname
^C
[root@web01 ~]# ssh 172.16.1.61 hostname
root@172.16.1.61's password:
m01
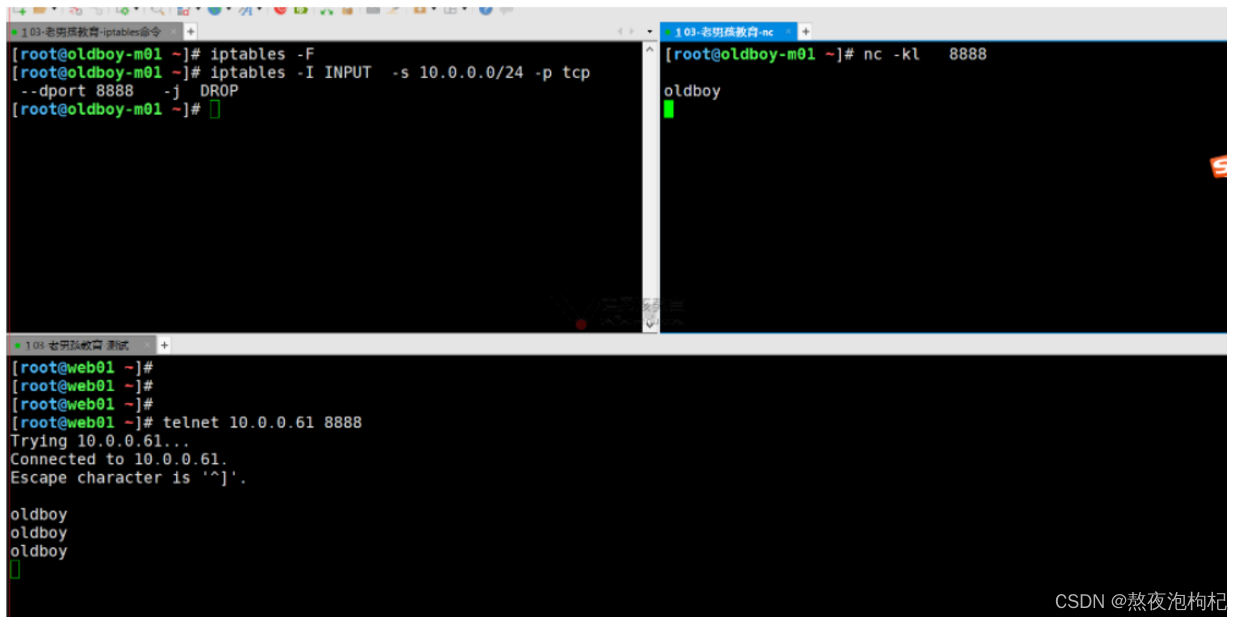
1.6.4 只允许指定网段连入(允许10.0.0.0网段)
实现阿里云白名单功能 :默认是拒绝 开放端口 网段
allow 10.0.0.0/24;
deny all;
#方法1: 利用 ! 进行排除
#只准许 10.0.0.0/24 访问 言外之意 除了 10.0.0.0/24 都拒绝
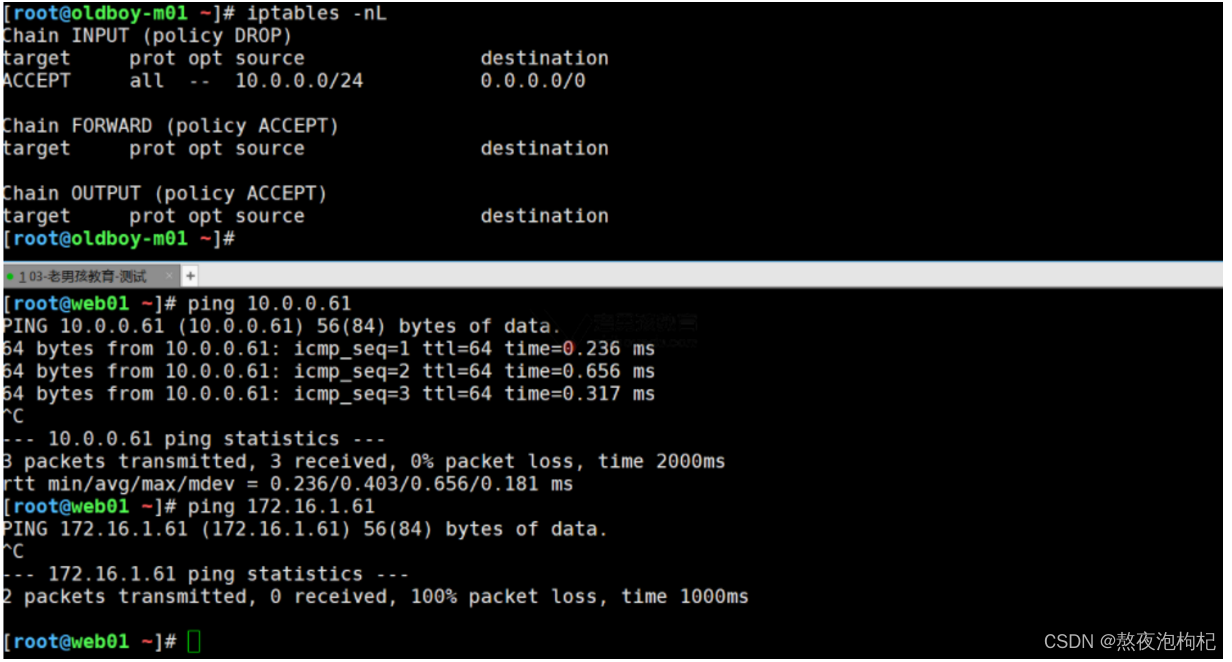
iptables -I INPUT ! -s 10.0.0.0/24 -j DROP
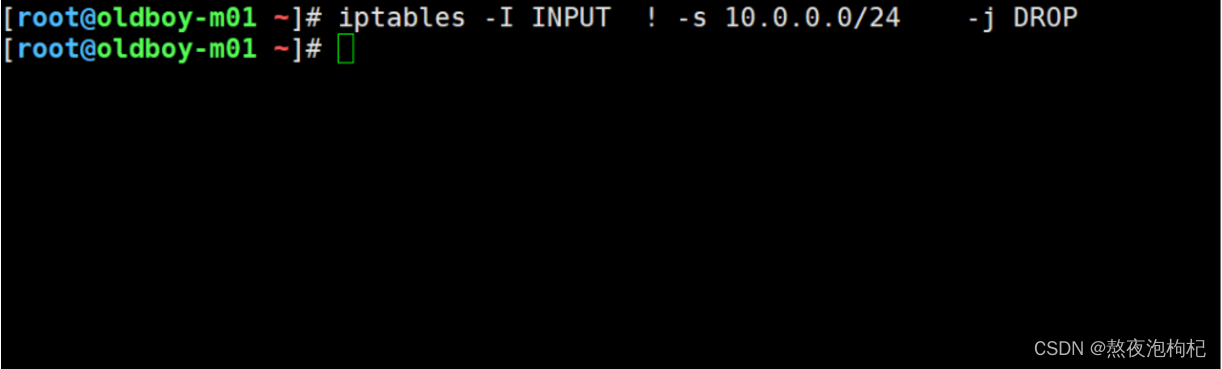
#方法2: 修改链默认规则 修改为拒绝 添加准许
先配置好规则 准许规则
修改默认规则
[root@oldboy-m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
?
Chain FORWARD (policy ACCEPT)
target prot opt source destination
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@oldboy-m01 ~]# iptables -A INPUT -s 10.0.0.0/24 -j ACCEPT
[root@oldboy-m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 10.0.0.0/24 0.0.0.0/0
?
Chain FORWARD (policy ACCEPT)
target prot opt source destination
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@oldboy-m01 ~]# iptables -P INPUT DROP
[root@oldboy-m01 ~]# iptables -nL
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT all -- 10.0.0.0/24 0.0.0.0/0
?
Chain FORWARD (policy ACCEPT)
target prot opt source destination
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
?
#测试完成后 修改回去
?
iptables -P INPUT ACCEPT
?
1.6.4 指定多个端口
[root@oldboy-m01 ~]# iptables -I INPUT -p tcp --dport 8888 -j DROP
[root@oldboy-m01 ~]# iptables -I INPUT -p tcp --dport 9999 -j DROP
[root@oldboy-m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:9999
DROP tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:8888
?
Chain FORWARD (policy ACCEPT)
target prot opt source destination
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
?
?
#补充:
#
[root@m01 ~]# iptables -I INPUT -p tcp -m multiport ! --dport 80,443 -j DROP
#如果是 连续的端口 可以不加上-m multiport 1:1024
[root@m01 ~]# iptables -I INPUT -p tcp --dport 1024:65535 -j DROP
1.6.5 匹配ICMP类型
ICMP(Internet Control Message Protocol)Internet控制报文协议 ping
整个网站核心
通过防火墙规则 控制是否可以ping
[root@m01 ~]# iptables -I INPUT -p icmp --icmp-type 8 -j DROP
[root@m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP icmp -- 0.0.0.0/0 0.0.0.0/0 icmptype 8
?
Chain FORWARD (policy ACCEPT)
target prot opt source destination
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
通过内核参数 控制 禁止被ping
[root@m01 ~]# cat /etc/sysctl.conf
#/proc/sys/net/ipv4/icmp_echo_ignore_all
?
net.ipv4.icmp_echo_ignore_all = 1
[root@m01 ~]# sysctl -p
net.ipv4.icmp_echo_ignore_all = 1
?
[root@oldboy-m01 ~]# echo 1 >/proc/sys/net/ipv4/icmp_echo_ignore_all
[root@oldboy-m01 ~]# #net.ipv4.icmp_echo_ignore_all=1 写入到 /etc/sysctl.conf[root@oldboy-m01 ~]# #sysctl -p
[root@oldboy-m01 ~]# echo 0 >/proc/sys/net/ipv4/icmp_echo_ignore_all
1.6.6 匹配网络状态(TCP/IP连接状态)
-m state --state
NEW:已经或将启动新的连接
ESTABLISHED:已建立的连接
RELATED:正在启动的新连接
INVALID:非法或无法识别的
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
?
iptables -A OUTPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
3.6.7 限制并发及速率
-m limit 限制模块
-m limit --limit 10/minute #每分钟只能有10个数据包 每6秒生成
-m limit --limit n/{second/minute/hour}:
解释:指定时间内的请求速率”n”为速率,后面为时间分别为:秒 分 时
-m limit --limit 10/minute --limit-burst 5 每6秒释放工牌 给别人使用
?
#10个数据包
前5个 1个1个工牌 从第6个开始 每6秒 才能释放1个工牌
–limit-burst [n]
解释:在同一时间内允许通过的请求”n”为数字,不指定默认为5
- 测试演示
#ping icmp 协议 进行测试
iptables -F
iptables -I INPUT -p icmp -m limit --limit 10/minute --limit-burst 5 -j ACCEPT
iptables -A INPUT -p tcp --dport 22 -j ACCEPT
iptables -P INPUT DROP
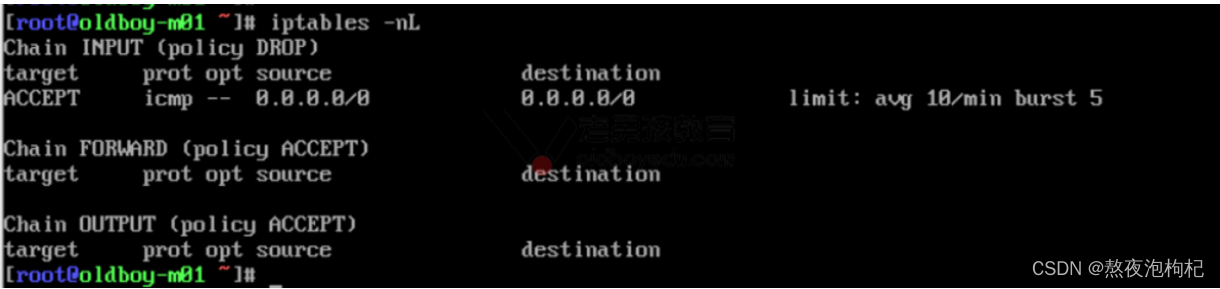
- web01 进行ping测试
ping 10.0.0.61
?
[root@web01 ~]# ping 10.0.0.61
PING 10.0.0.61 (10.0.0.61) 56(84) bytes of data.
64 bytes from 10.0.0.61: icmp_seq=1 ttl=64 time=0.240 ms
64 bytes from 10.0.0.61: icmp_seq=2 ttl=64 time=0.376 ms
64 bytes from 10.0.0.61: icmp_seq=3 ttl=64 time=0.474 ms
64 bytes from 10.0.0.61: icmp_seq=4 ttl=64 time=0.693 ms
64 bytes from 10.0.0.61: icmp_seq=5 ttl=64 time=2.43 ms
64 bytes from 10.0.0.61: icmp_seq=7 ttl=64 time=0.351 ms #7与1比 就是间隔6秒
64 bytes from 10.0.0.61: icmp_seq=13 ttl=64 time=0.869 ms #7 13 间隔6秒
64 bytes from 10.0.0.61: icmp_seq=19 ttl=64 time=0.482 ms
64 bytes from 10.0.0.61: icmp_seq=25 ttl=64 time=0.378 ms
64 bytes from 10.0.0.61: icmp_seq=31 ttl=64 time=0.329 ms
64 bytes from 10.0.0.61: icmp_seq=37 ttl=64 time=0.857 ms
64 bytes from 10.0.0.61: icmp_seq=43 ttl=64 time=0.314 ms
64 bytes from 10.0.0.61: icmp_seq=49 ttl=64 time=0.360 ms
64 bytes from 10.0.0.61: icmp_seq=55 ttl=64 time=0.349 ms
64 bytes from 10.0.0.61: icmp_seq=61 ttl=64 time=0.552 ms
64 bytes from 10.0.0.61: icmp_seq=67 ttl=64 time=0.283 ms
64 bytes from 10.0.0.61: icmp_seq=73 ttl=64 time=0.407 ms
64 bytes from 10.0.0.61: icmp_seq=79 ttl=64 time=0.297 ms
64 bytes from 10.0.0.61: icmp_seq=85 ttl=64 time=0.428 ms
64 bytes from 10.0.0.61: icmp_seq=91 ttl=64 time=0.390 ms
64 bytes from 10.0.0.61: icmp_seq=97 ttl=64 time=0.691 ms
64 bytes from 10.0.0.61: icmp_seq=103 ttl=64 time=0.537 ms
64 bytes from 10.0.0.61: icmp_seq=109 ttl=64 time=0.546 ms
64 bytes from 10.0.0.61: icmp_seq=115 ttl=64 time=0.382 ms
64 bytes from 10.0.0.61: icmp_seq=121 ttl=64 time=0.337 ms
?
1.6.8 防火墙规则的保存与恢复
iptables-save 默认输出到屏幕
iptables-restore 加上文件
写入到/etc/sysconfig/iptables
[root@oldboy-m01 ~]# iptables-save >/etc/sysconfig/iptables
[root@oldboy-m01 ~]# cat /etc/sysconfig/iptables
# Generated by iptables-save v1.4.21 on Wed Feb 12 15:31:43 2020
*filter
:INPUT DROP [92:7008]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [127:14360]
-A INPUT -p icmp -m limit --limit 10/min -j ACCEPT
-A INPUT -p tcp -m tcp --dport 22 -j ACCEPT
-A INPUT -p tcp -m multiport --dports 80,443 -j ACCEPT
COMMIT
# Completed on Wed Feb 12 15:31:43 2020
# Generated by iptables-save v1.4.21 on Wed Feb 12 15:31:43 2020
*nat
:PREROUTING ACCEPT [559:51047]
:INPUT ACCEPT [60:6814]
:OUTPUT ACCEPT [6801:408868]
:POSTROUTING ACCEPT [6801:408868]
COMMIT
# Completed on Wed Feb 12 15:31:43 2020
[root@oldboy-m01 ~]# iptables -nL
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 limit: avg 10/min burst 5
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 80,443
?
Chain FORWARD (policy ACCEPT)
target prot opt source destination
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@oldboy-m01 ~]# iptables -D 1
iptables: Bad rule (does a matching rule exist in that chain?).
[root@oldboy-m01 ~]#
[root@oldboy-m01 ~]# iptables -D INPUT 1
[root@oldboy-m01 ~]# iptables -nL
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 80,443
?
Chain FORWARD (policy ACCEPT)
target prot opt source destination
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@oldboy-m01 ~]# iptables-restore </etc/sysconfig/iptables
[root@oldboy-m01 ~]# iptables -nL
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 limit: avg 10/min burst 5
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 80,443
?
Chain FORWARD (policy ACCEPT)
target prot opt source destination
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
?
补充:
systemctl restart iptables #读取 /etc/sysconfig/iptables内容
1.6.9 filter表小结
封ip 端口 网段
禁止ping
限制速度和并发
iptables filter表 功能 可以在 云服务器使用
1.7 实际生产用法
iptables配置方式
逛公园模式: 默认规则是 ACCEPT
看电影模式: 默认规则是 DROP
默认是拒绝 去电影院
(1)ssh可以连接进来
[root@m01 ~]# iptables -F
[root@m01 ~]# iptables -X
[root@m01 ~]# iptables -Z
[root@m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
?
Chain FORWARD (policy ACCEPT)
target prot opt source destination
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@m01 ~]# iptables -A INPUT -p tcp --dport 22 -j ACCEPT
[root@m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
?
Chain FORWARD (policy ACCEPT)
target prot opt source destination
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
(2)设置允许本机lo通讯规则
允许本机回环lo接口数据流量流出与流入
iptables -A INPUT -i lo -j ACCEPT
iptables -A OUTPUT -o lo -j ACCEPT
(3)配置默认规则及 放行 80 443端口
[root@m01 ~]# iptables -P INPUT DROP
[root@m01 ~]# iptables -P FORWARD DROP
[root@m01 ~]# iptables -P OUTPUT ACCEPT
?
[root@m01 ~]# iptables -A INPUT -m multiport -p tcp --dport 443,80 -j ACCEPT
[root@m01 ~]# iptables -nL
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 443,80
?
Chain FORWARD (policy DROP)
target prot opt source destination
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
[root@m01 ~]# iptables -A INPUT -s 10.0.0.0/24 -j ACCEPT
[root@m01 ~]# iptables -A INPUT -s 172.16.1.0/24 -j ACCEPT
#此处还可以添加 vpn网段 比如说 10.7.1.0/24
?
[root@m01 ~]# iptables -nL
Chain INPUT (policy DROP)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 443,80
ACCEPT all -- 10.0.0.0/24 0.0.0.0/0
ACCEPT all -- 172.16.1.0/24 0.0.0.0/0
?
Chain FORWARD (policy DROP)
target prot opt source destination
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
[root@m01 ~]# iptables-save
# Generated by iptables-save v1.4.21 on Wed Jul 24 23:42:00 2019
*filter
:INPUT DROP [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [24:3008]
-A INPUT -p tcp -m tcp --dport 22 -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m multiport --dports 443,80 -j ACCEPT
-A INPUT -s 10.0.0.0/24 -j ACCEPT
-A INPUT -s 172.16.1.0/24 -j ACCEPT
-A OUTPUT -o lo -j ACCEPT
COMMIT
# Completed on Wed Jul 24 23:42:00 2019
- 汇总
[root@oldboy-m01 ~]# iptables-save
# Generated by iptables-save v1.4.21 on Wed Feb 12 15:51:48 2020
*filter
:INPUT DROP [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [1:60]
-A INPUT -p tcp -m tcp --dport 22 -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m multiport --dports 443,80 -j ACCEPT
-A INPUT -s 10.0.0.0/24 -j ACCEPT
-A INPUT -s 172.16.1.0/24 -j ACCEPT
-A INPUT -s 10.7.1.0/24 -j ACCEPT
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A OUTPUT -o lo -j ACCEPT
-A OUTPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
COMMIT
# Completed on Wed Feb 12 15:51:48 2020
# Generated by iptables-save v1.4.21 on Wed Feb 12 15:51:48 2020
*nat
:PREROUTING ACCEPT [2:458]
:INPUT ACCEPT [0:0]
:OUTPUT ACCEPT [417:25020]
:POSTROUTING ACCEPT [417:25020]
COMMIT
# Completed on Wed Feb 12 15:51:48 2020
?
1.8 nat
共享上网
端口转发/端口映射
ip映射
[root@m01 ~]# iptables -P INPUT ACCEPT
[root@m01 ~]# iptables -P FORWARD ACCEPT
[root@m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
DROP icmp -- 0.0.0.0/0 0.0.0.0/0 icmptype 8
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 443,80
ACCEPT all -- 10.0.0.0/24 0.0.0.0/0
ACCEPT all -- 172.16.1.0/24 0.0.0.0/0
?
Chain FORWARD (policy ACCEPT)
target prot opt source destination
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
[root@m01 ~]# iptables -F
[root@m01 ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
?
Chain FORWARD (policy ACCEPT)
target prot opt source destination
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
1.8.1 实现共享上网
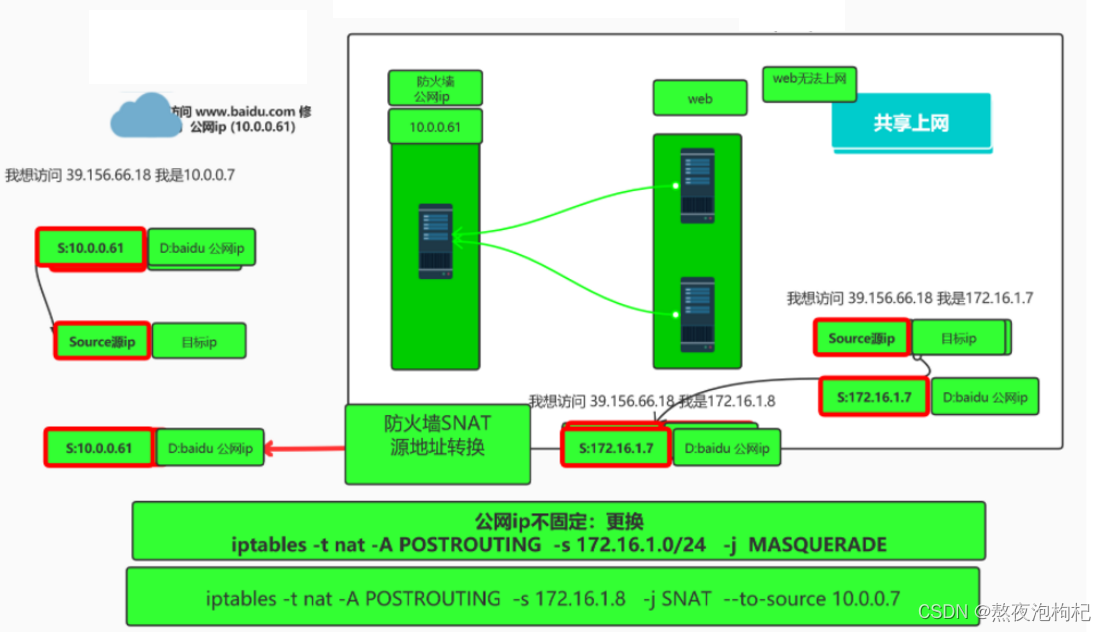
- 防火墙配置
[root@m01 ~]# iptables -t nat -A POSTROUTING -s 172.16.1.0/24 -j SNAT --to-source 10.0.0.61
[root@m01 ~]# echo 'net.ipv4.ip_forward = 1' >> /etc/sysctl.conf
[root@m01 ~]# sysctl -p
net.ipv4.icmp_echo_ignore_all = 0
net.ipv4.ip_forward = 1
注意事项:
公网ip不固定:
iptables -t nat -A POSTROUTING -s 172.16.1.0/24 -j MASQUERADE
- web配置
[root@web01 ~]# cat /etc/sysconfig/network-scripts/ifcfg-eth0
TYPE=Ethernet
BOOTPROTO=none
NAME=eth0
DEVICE=eth0
ONBOOT=no
IPADDR=10.0.0.7
PREFIX=24
GATEWAY=10.0.0.254
DNS1=223.5.5.5
GATEWAY=10.0.0.254
[root@web01 ~]# cat /etc/sysconfig/network-scripts/ifcfg-eth1
TYPE=Ethernet
IPADDR=172.16.1.7
PREFIX=24
NAME=eth1
DEVICE=eth1
ONBOOT=yes
GATEWAY=172.16.1.61
DNS1=1.2.4.8
[root@web01 ~]# systemctl restart network
[root@m01 ~]# ssh 172.16.1.7
Last login: Wed Jul 24 23:06:58 2019 from 10.0.0.1
[root@web01 ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST> mtu 1500 qdisc pfifo_fast state DOWN group default qlen 1000
link/ether 00:0c:29:b2:e3:7e brd ff:ff:ff:ff:ff:ff
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:b2:e3:88 brd ff:ff:ff:ff:ff:ff
inet 172.16.1.7/24 brd 172.16.1.255 scope global eth1
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:feb2:e388/64 scope link
valid_lft forever preferred_lft forever
[root@web01 ~]# ping baidu.com
PING baidu.com (220.181.38.148) 56(84) bytes of data.
64 bytes from 220.181.38.148 (220.181.38.148): icmp_seq=1 ttl=127 time=8.90 ms
64 bytes from 220.181.38.148 (220.181.38.148): icmp_seq=2 ttl=127 time=7.52 ms
64 bytes from 220.181.38.148 (220.181.38.148): icmp_seq=3 ttl=127 time=9.28 ms
64 bytes from 220.181.38.148 (220.181.38.148): icmp_seq=4 ttl=127 time=9.36 ms
^C
--- baidu.com ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3006ms
rtt min/avg/max/mdev = 7.528/8.769/9.364/0.746 ms
[root@web01 ~]# ping 1.2.4.8
PING 1.2.4.8 (1.2.4.8) 56(84) bytes of data.
64 bytes from 1.2.4.8: icmp_seq=1 ttl=127 time=76.4 ms
64 bytes from 1.2.4.8: icmp_seq=2 ttl=127 time=76.8 ms
^C
--- 1.2.4.8 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 76.440/76.637/76.834/0.197 ms
- 完成后 在web01 发出 ip r和ping 外网ip的结果
[root@web01 ~]# ip r
default via 172.16.1.61 dev eth1
169.254.0.0/16 dev eth1 scope link metric 1003
172.16.1.0/24 dev eth1 proto kernel scope link src 172.16.1.7
[root@web01 ~]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 172.16.1.61 0.0.0.0 UG 0 0 0 eth1
169.254.0.0 0.0.0.0 255.255.0.0 U 1003 0 0 eth1
172.16.1.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
[root@web01 ~]# ping baidu.com
PING baidu.com (39.156.69.79) 56(84) bytes of data.
64 bytes from 39.156.69.79 (39.156.69.79): icmp_seq=1 ttl=127 time=21.7 ms
64 bytes from 39.156.69.79 (39.156.69.79): icmp_seq=2 ttl=127 time=32.6 ms
^C
--- baidu.com ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 21.781/27.214/32.647/5.433 ms
1.8.2 实现端口转发
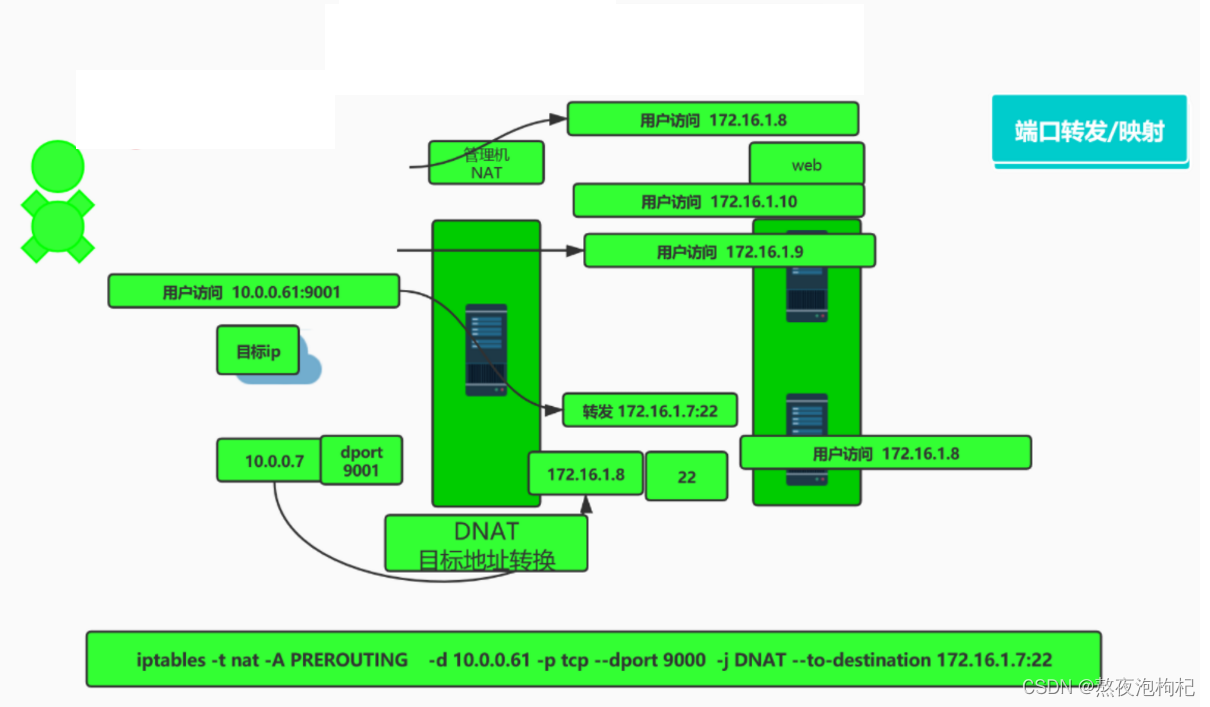
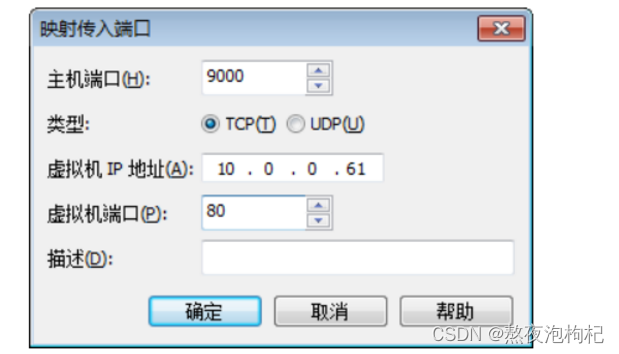
[root@m01 ~]# iptables -t nat -A PREROUTING -d 10.0.0.61 -p tcp --dport 9000 -j DNAT --to-destination 172.16.1.7:22
[root@m01 ~]# iptables -nL -t nat
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DNAT tcp -- 0.0.0.0/0 10.0.0.61 tcp dpt:9000 to:172.16.1.7:22
?
Chain INPUT (policy ACCEPT)
target prot opt source destination
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
?
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 172.16.1.0/24 0.0.0.0/0 to:10.0.0.61
测试与检查
本地shell中
[d:\~]$ ssh root@10.0.0.61 9000
1.8.3 实现ip映射
ip a add 10.0.0.62/24 dev eth0 label eth0:0
?
[root@m01 ~]# iptables -t nat -A PREROUTING -d 10.0.0.62 -j DNAT --to-destination 172.16.1.7
[root@m01 ~]# iptables -nL -t nat
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DNAT tcp -- 0.0.0.0/0 10.0.0.61 tcp dpt:9000 to:172.16.1.7:22
DNAT all -- 0.0.0.0/0 10.0.0.62 to:172.16.1.7
?
Chain INPUT (policy ACCEPT)
target prot opt source destination
?
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
?
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 172.16.1.0/24 0.0.0.0/0 to:10.0.0.61
1.8.4 nat表总结
实现共享上网
端口转发
nat功能在 云服务器无法使用 替代品叫: NAT网关
2. 自我总结
排错必备命令:
tcpdump -nni eth0 port 9000 抓包工具
route -n 查看路由信息(主要看网关)看第一行的内容
ICMP是控制协议,不需要端口号
nat的snat是提供内网上网的
nat的dnat是从外网连接内网的服务器的
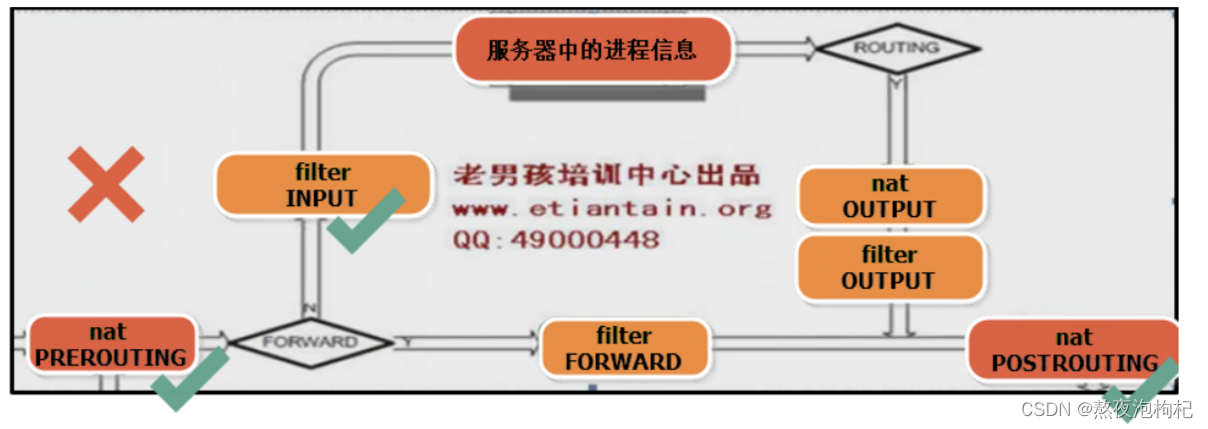
iptalbles在网络层的上面和下面进行控制
ip 截获ip tables按照三个表进行过滤··
iptables命令来把配置下面的表:
filter表:控制放行和拒绝的,比如22端放行(常用)
nat表: sant dant作用(常用),网络地址转换
mangle表:改写头部信息的,一般用不到
raw表
网卡双路由(三种数据包情况)
1. 是不是找我的80端口的服务
2. 找我的,转发到另一个服务器上,可能找后端的服务去了
3. 由应用层直接出去出去的有数据包
有函数的地方就是链
不指定表,默认的就是filter表
停止firewalld,然后安装iptables
yum list | grep iptables 安装server端
input:允许谁进
如果不加-t 指定表的话就是走的是filter表
3. 练习题
https://www.jianshu.com/p/19422676b854
(1)请写出查看iptables当前所有规则的命令。
iptables-save
iptables -nL
iptables -nL -t nat
(2)禁止来自10.0.0.188 ip地址访问80端口的请求
iptables -I INPUT -s 10.0.0.188 -p tcp --dport 80 -j DROP
(3)如何使在命令行执行的iptables规则永久生效?
iptables-save
?
/etc/sysconfig/iptables
(4)实现把访问10.0.0.3:80的请求转到172.16.1.17:80
iptables -t nat -A PREROUTING -d 10.0.0.3 -p tcp --dport 80 -j DNAT --to-destination 172.16.xxxx:80
(5)实现172.16.1.0/24段所有主机通过124.32.54.26外网IP共享上网。
iptables -t nat -A POSTROUTING -s 172.16.1.0/24 -j SNAT --to-source 123.32.54.26
?
iptables -t nat -A POSTROUTING -s 172.16.1.0/24 -j SNAT MASQUERADE
(6)案例 iptalbes 实现防止syn ddos 和ping攻击
-A FORWARD -p tcp --syn -m limit --limit 1/s --limit-burst 5 -j ACCEPT
-A FORWARD -p tcp --tcp-flags SYN,ACK,FIN,RST RST -m limit --limit 1/s -j ACCEPT
-A FORWARD -p icmp --icmp-type echo-request -m limit --limit 1/s -j ACCEPT
说明:第一行:每秒中最多允许5个新连接。第二行:防止各种端口扫描。第三行:Ping洪水攻击(Ping of Death),可以根据需要调整或关闭
防火墙 笔试题 www.jianshu.com/p/2180face8381
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!