麒麟KYLINOS禁用IPV6地址
原文链接:麒麟KYLINOS操作系统上禁用IPv6的方法
hello,大家好啊!今天我要给大家介绍的是在麒麟KYLINOS操作系统上禁用IPv6的方法。IPv6是最新的网络通信协议,旨在解决IPv4地址耗尽的问题。然而,在某些特定的网络环境或测试场景中,可能需要禁用IPv6以确保兼容性或满足其他需求。本文将介绍通过图形化界面、修改配置文件、命令行添加禁用IPv6等三种方式来实现这一目的。让我们开始吧!
注意事项
- 在进行任何系统配置更改之前,请确保您了解这些更改的影响,并考虑备份相关配置文件。
- 禁用IPv6可能会影响您的网络连接和某些依赖IPv6的应用程序或服务。
- 如果您不确定是否需要禁用IPv6,请咨询您的网络管理员或技术支持团队。
1.查看系统信息
pdsyw@pdsyw-pc:~/Desktop$ cat /etc/os-release
NAME="Kylin"
VERSION="银河麒麟桌面操作系统V10 (SP1)"
VERSION_US="Kylin Linux Desktop V10 (SP1)"
ID=kylin
ID_LIKE=debian
PRETTY_NAME="Kylin V10 SP1"
VERSION_ID="v10"
HOME_URL="http://www.kylinos.cn/"
SUPPORT_URL="http://www.kylinos.cn/support/technology.html"
BUG_REPORT_URL="http://www.kylinos.cn/"
PRIVACY_POLICY_URL="http://www.kylinos.cn"
VERSION_CODENAME=kylin
UBUNTU_CODENAME=kylin
PROJECT_CODENAME=V10SP1
KYLIN_RELEASE_ID="2303"
pdsyw@pdsyw-pc:~/Desktop$
pdsyw@pdsyw-pc:~/Desktop$ uname -a
Linux pdsyw-pc 4.19.71-30-kr990 #27b1-KYLINOS SMP PREEMPT Thu Jun 8 05:57:15 UTC 2023 aarch64 aarch64 aarch64 GNU/Linux
pdsyw@pdsyw-pc:~/Desktop$
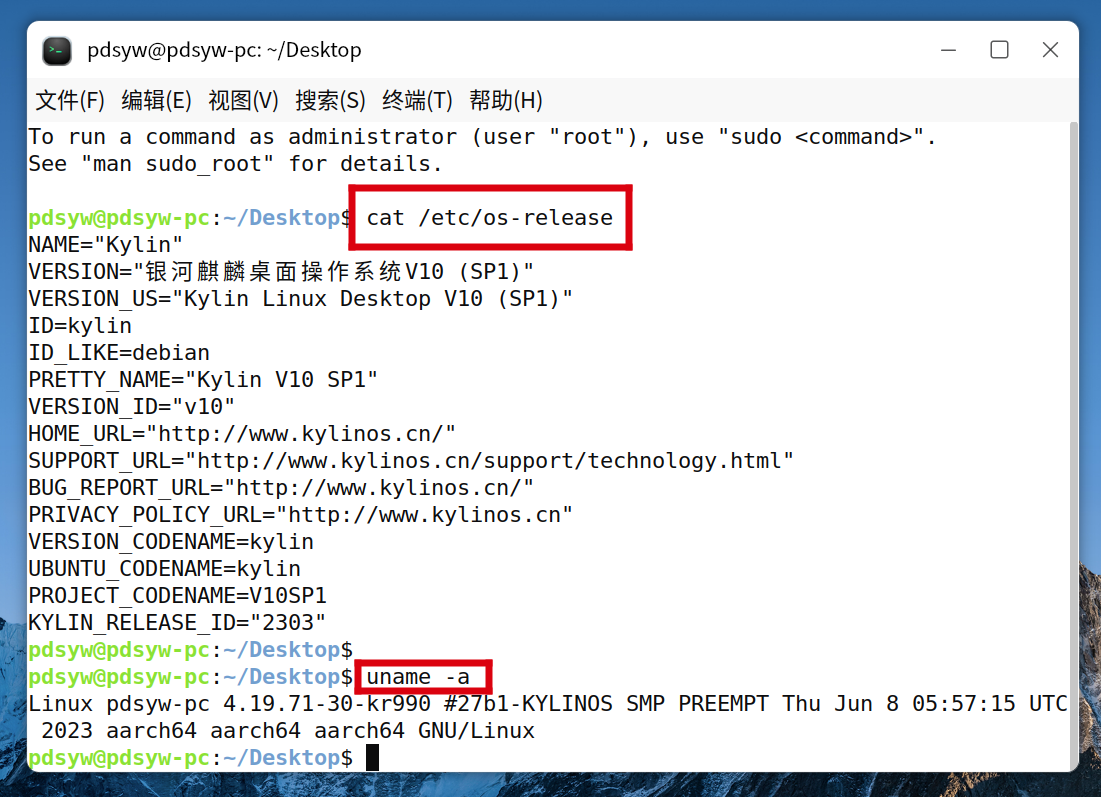
2.ping百度后发现默认使用ipv6地址
pdsyw@pdsyw-pc:~/Desktop$ ping www.baidu.com
PING www.baidu.com(240e:e9:6002:15c:0:ff:b015:146f (240e:e9:6002:15c:0:ff:b015:146f)) 56 data bytes
64 bytes from 240e:e9:6002:15c:0:ff:b015:146f (240e:e9:6002:15c:0:ff:b015:146f): icmp_seq=1 ttl=52 time=26.3 ms
64 bytes from 240e:e9:6002:15c:0:ff:b015:146f (240e:e9:6002:15c:0:ff:b015:146f): icmp_seq=2 ttl=52 time=20.1 ms
64 bytes from 240e:e9:6002:15c:0:ff:b015:146f (240e:e9:6002:15c:0:ff:b015:146f): icmp_seq=3 ttl=52 time=22.9 ms
64 bytes from 240e:e9:6002:15c:0:ff:b015:146f (240e:e9:6002:15c:0:ff:b015:146f): icmp_seq=4 ttl=52 time=31.7 ms
64 bytes from 240e:e9:6002:15c:0:ff:b015:146f (240e:e9:6002:15c:0:ff:b015:146f): icmp_seq=5 ttl=52 time=22.5 ms
64 bytes from 240e:e9:6002:15c:0:ff:b015:146f (240e:e9:6002:15c:0:ff:b015:146f): icmp_seq=6 ttl=52 time=24.7 ms
64 bytes from 240e:e9:6002:15c:0:ff:b015:146f (240e:e9:6002:15c:0:ff:b015:146f): icmp_seq=7 ttl=52 time=27.7 ms
^C
--- www.baidu.com ping statistics ---
7 packets transmitted, 7 received, 0% packet loss, time 6008ms
rtt min/avg/max/mdev = 20.101/25.109/31.654/3.543 ms
pdsyw@pdsyw-pc:~/Desktop$
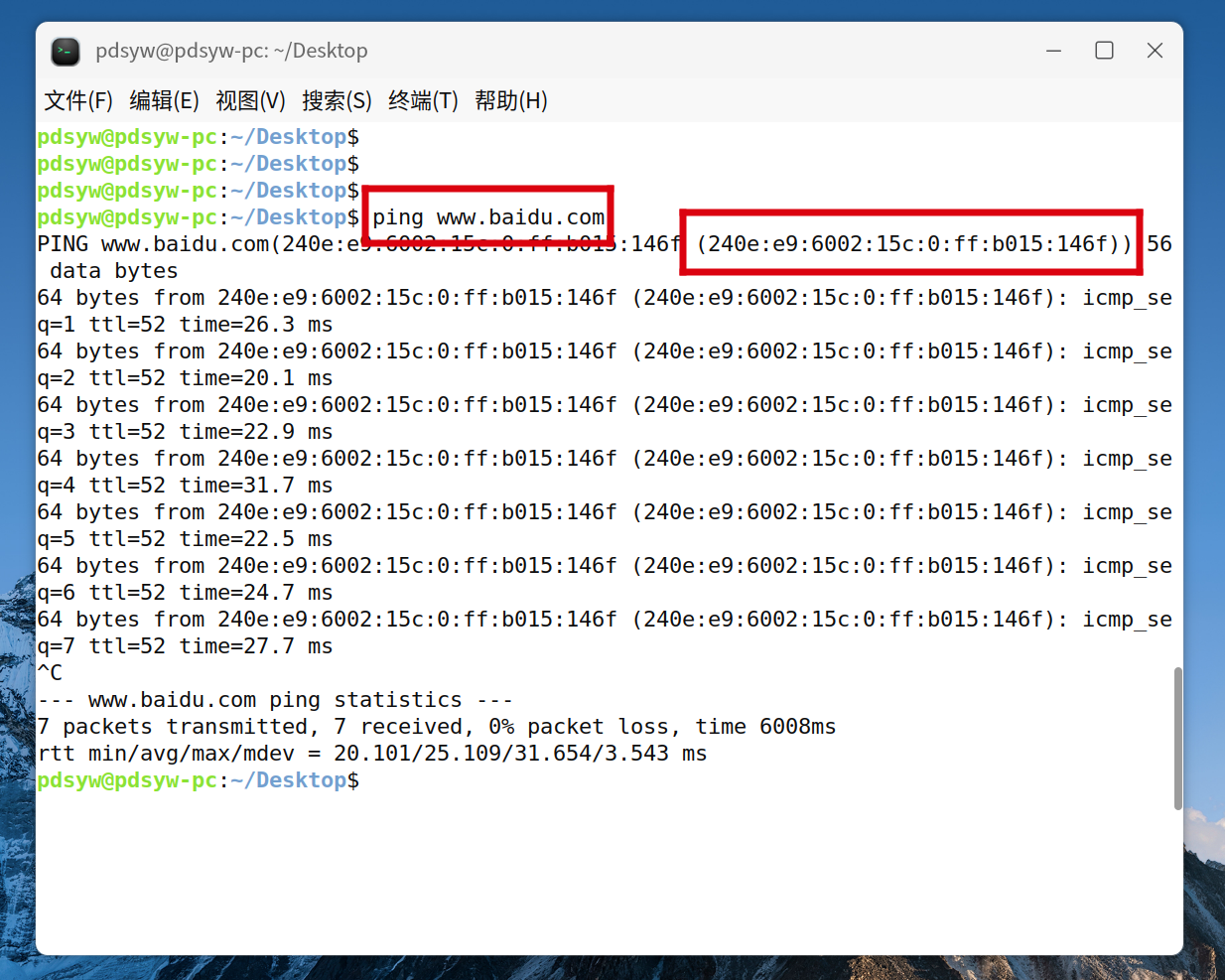
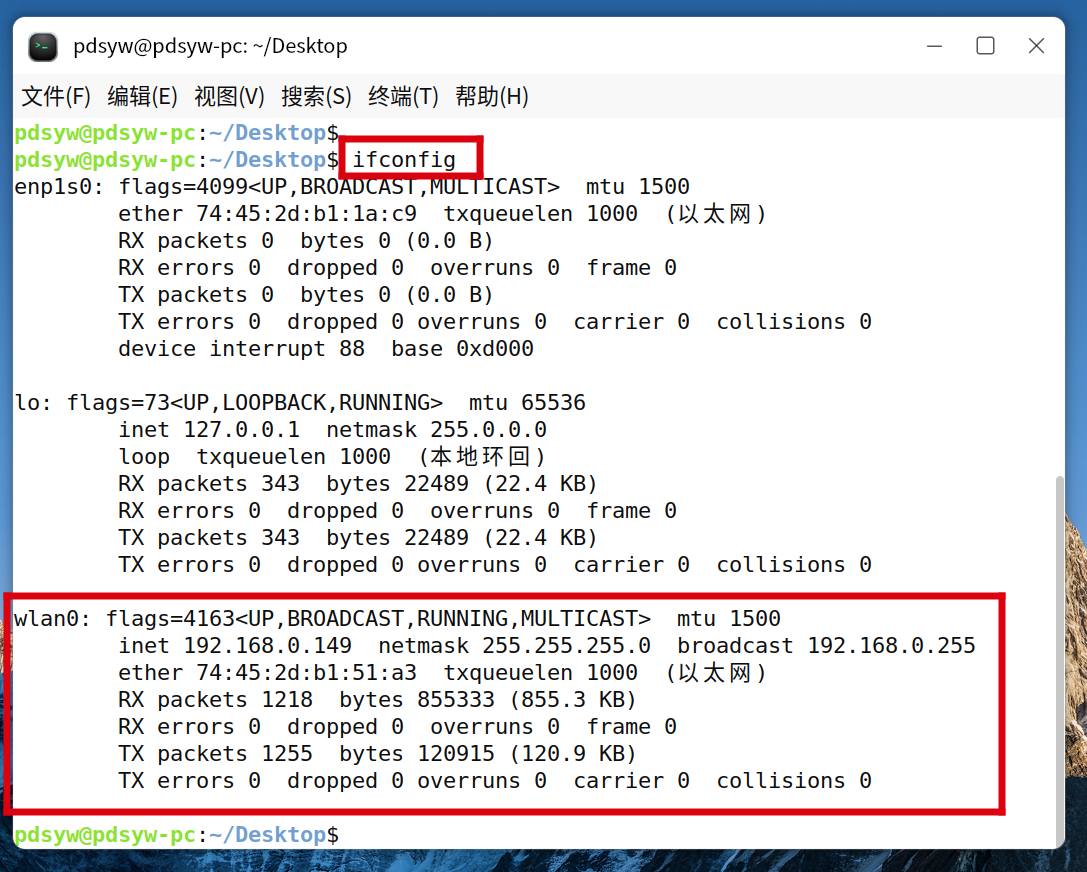
3.查看ip地址信息,发现已经默认配置了ipv6地址
pdsyw@pdsyw-pc:~/Desktop$ ifconfig
enp1s0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether 74:45:2d:b1:1a:c9 txqueuelen 1000 (以太网)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
device interrupt 88 base 0xd000
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (本地环回)
RX packets 1019 bytes 61491 (61.4 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1019 bytes 61491 (61.4 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
wlan0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.0.149 netmask 255.255.255.0 broadcast 192.168.0.255
inet6 fe80::1c87:9127:d39d:64cd prefixlen 64 scopeid 0x20<link>
inet6 240e:46c:8900:ca55:7958:d22b:b4a8:b895 prefixlen 64 scopeid 0x0<global>
inet6 240e:46c:8900:ca55:b269:ce29:45fa:572b prefixlen 64 scopeid 0x0<global>
ether 74:45:2d:b1:51:a3 txqueuelen 1000 (以太网)
RX packets 61819 bytes 84649969 (84.6 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 12685 bytes 1005292 (1.0 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
pdsyw@pdsyw-pc:~/Desktop$
方法一:图形化禁用
1.查看无线局域网
2.点击高级设置
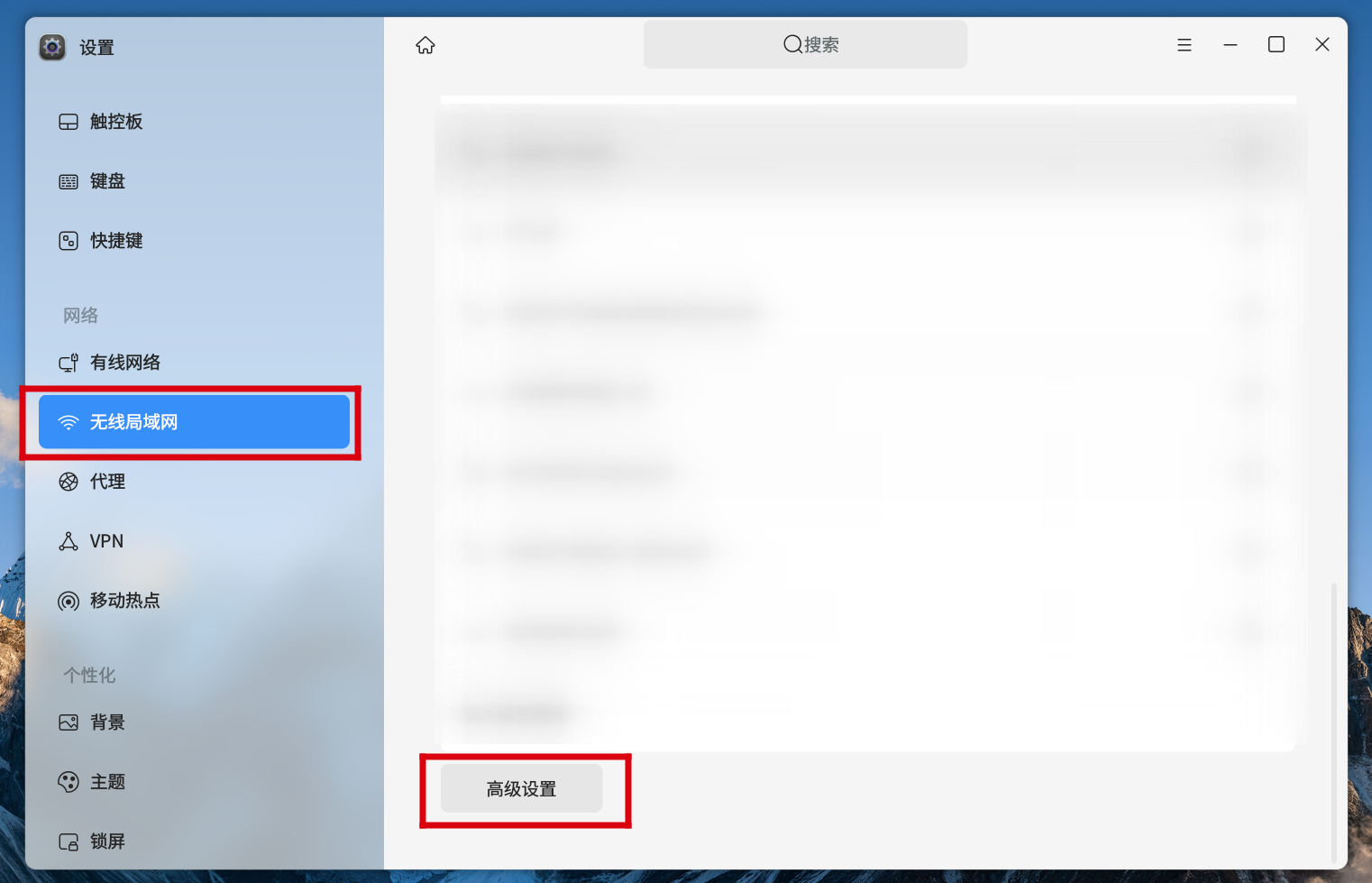
3.选择当前连接的WiFi,点击设置
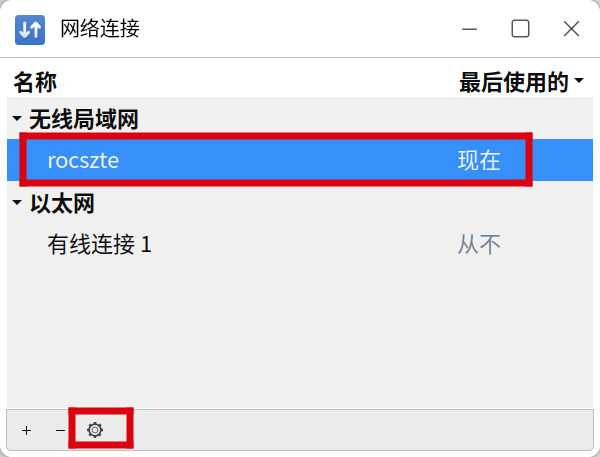
4.点击ipv6设置
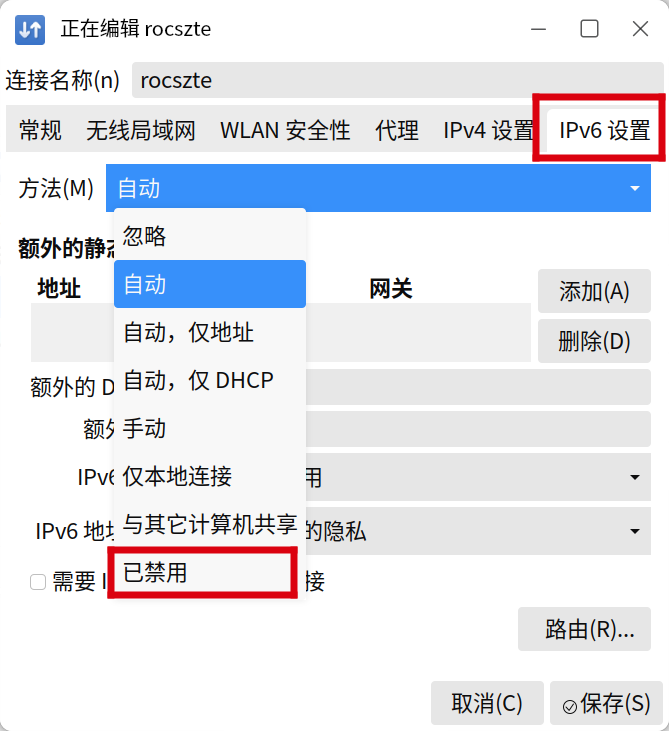
5.方法选择已禁用,点击保存
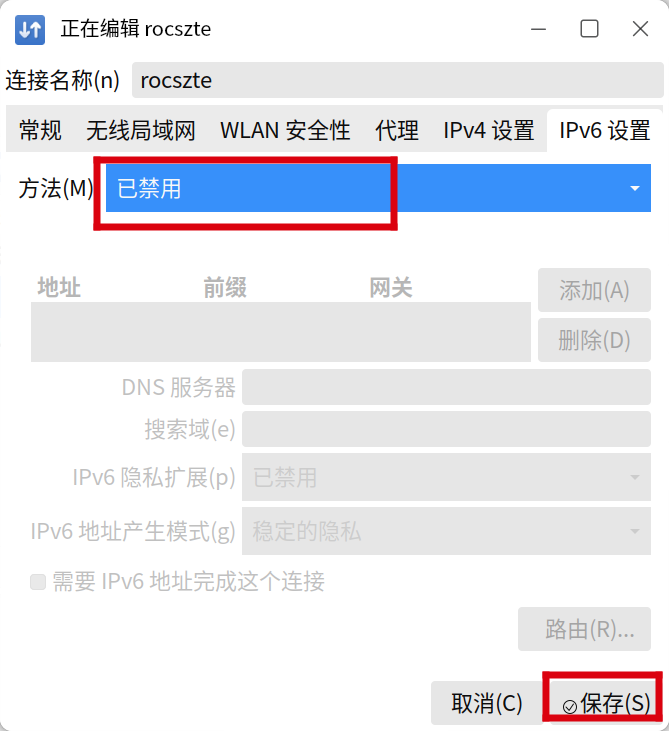
6.再次查看ip地址,已经没有ipv6地址
root@pdsyw-pc:~# ifconfig
enp1s0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether 74:45:2d:b1:1a:c9 txqueuelen 1000 (以太网)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
device interrupt 88 base 0xd000
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (本地环回)
RX packets 1237 bytes 73613 (73.6 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1237 bytes 73613 (73.6 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
wlan0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.0.149 netmask 255.255.255.0 broadcast 192.168.0.255
ether 74:45:2d:b1:51:a3 txqueuelen 1000 (以太网)
RX packets 62122 bytes 84675309 (84.6 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 12979 bytes 1027188 (1.0 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
root@pdsyw-pc:~#
[外链图片转存中…(img-5OWRvxE6-1704701360906)]
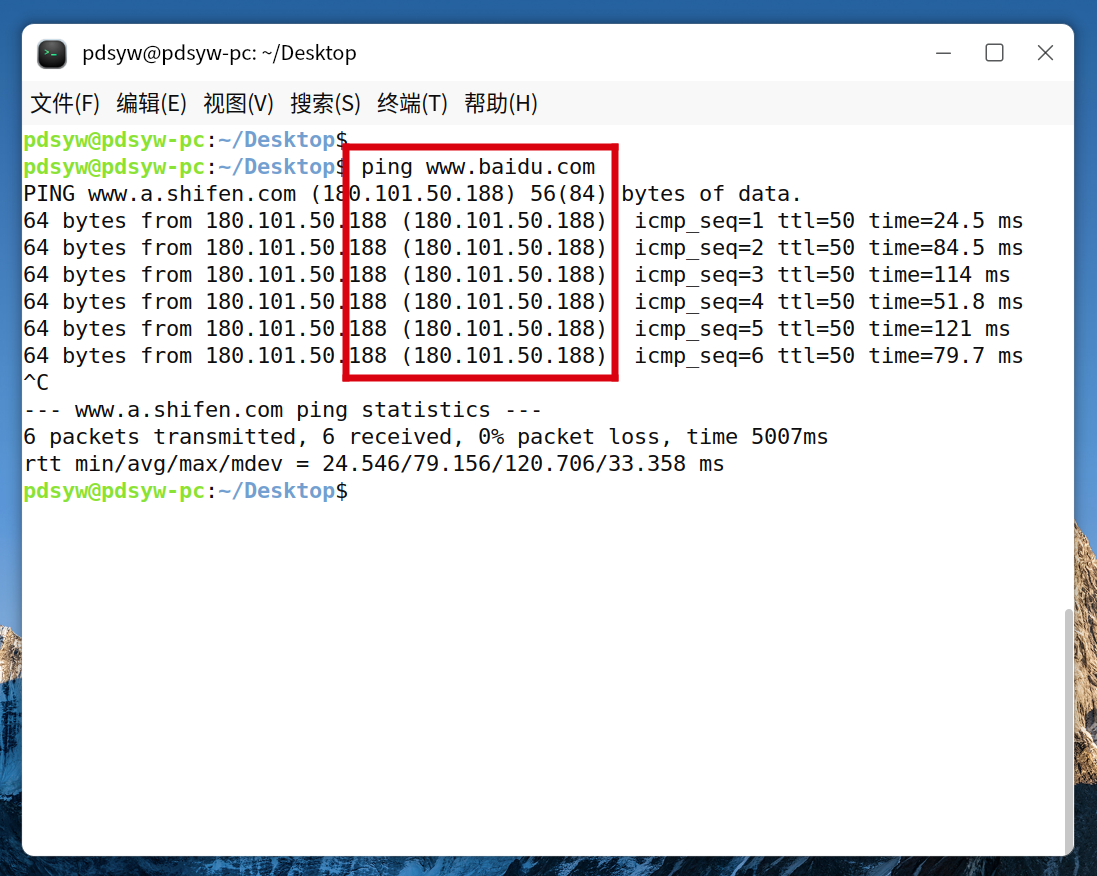
7.再次ping百度,默认使用ipv4地址
pdsyw@pdsyw-pc:~/Desktop$ ping www.baidu.com
PING www.a.shifen.com (180.101.50.188) 56(84) bytes of data.
64 bytes from 180.101.50.188 (180.101.50.188): icmp_seq=1 ttl=50 time=24.5 ms
64 bytes from 180.101.50.188 (180.101.50.188): icmp_seq=2 ttl=50 time=84.5 ms
64 bytes from 180.101.50.188 (180.101.50.188): icmp_seq=3 ttl=50 time=114 ms
64 bytes from 180.101.50.188 (180.101.50.188): icmp_seq=4 ttl=50 time=51.8 ms
64 bytes from 180.101.50.188 (180.101.50.188): icmp_seq=5 ttl=50 time=121 ms
64 bytes from 180.101.50.188 (180.101.50.188): icmp_seq=6 ttl=50 time=79.7 ms
^C
--- www.a.shifen.com ping statistics ---
6 packets transmitted, 6 received, 0% packet loss, time 5007ms
rtt min/avg/max/mdev = 24.546/79.156/120.706/33.358 ms
pdsyw@pdsyw-pc:~/Desktop$
方法二:编辑配置文件
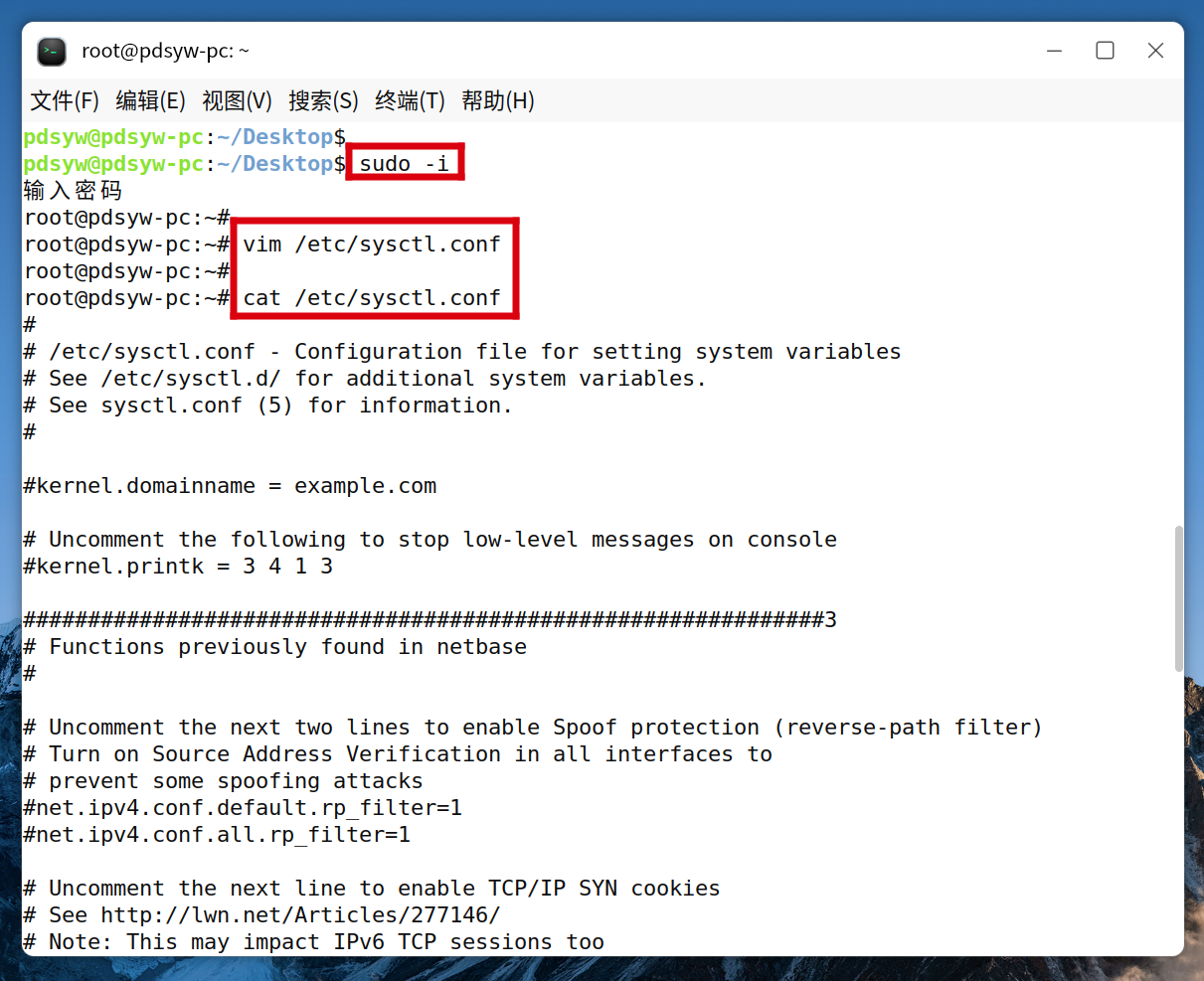
1.修改sysctl.conf,添加禁用ipv6的内容
pdsyw@pdsyw-pc:~/Desktop$ sudo -i
输入密码
root@pdsyw-pc:~#
root@pdsyw-pc:~# vim /etc/sysctl.conf
root@pdsyw-pc:~#
root@pdsyw-pc:~# cat /etc/sysctl.conf
#
# /etc/sysctl.conf - Configuration file for setting system variables
# See /etc/sysctl.d/ for additional system variables.
# See sysctl.conf (5) for information.
#
#kernel.domainname = example.com
# Uncomment the following to stop low-level messages on console
#kernel.printk = 3 4 1 3
##############################################################3
# Functions previously found in netbase
#
# Uncomment the next two lines to enable Spoof protection (reverse-path filter)
# Turn on Source Address Verification in all interfaces to
# prevent some spoofing attacks
#net.ipv4.conf.default.rp_filter=1
#net.ipv4.conf.all.rp_filter=1
# Uncomment the next line to enable TCP/IP SYN cookies
# See http://lwn.net/Articles/277146/
# Note: This may impact IPv6 TCP sessions too
#net.ipv4.tcp_syncookies=1
# Uncomment the next line to enable packet forwarding for IPv4
#net.ipv4.ip_forward=1
# Uncomment the next line to enable packet forwarding for IPv6
# Enabling this option disables Stateless Address Autoconfiguration
# based on Router Advertisements for this host
#net.ipv6.conf.all.forwarding=1
###################################################################
# Additional settings - these settings can improve the network
# security of the host and prevent against some network attacks
# including spoofing attacks and man in the middle attacks through
# redirection. Some network environments, however, require that these
# settings are disabled so review and enable them as needed.
#
# Do not accept ICMP redirects (prevent MITM attacks)
#net.ipv4.conf.all.accept_redirects = 0
#net.ipv6.conf.all.accept_redirects = 0
# _or_
# Accept ICMP redirects only for gateways listed in our default
# gateway list (enabled by default)
# net.ipv4.conf.all.secure_redirects = 1
#
# Do not send ICMP redirects (we are not a router)
#net.ipv4.conf.all.send_redirects = 0
#
# Do not accept IP source route packets (we are not a router)
#net.ipv4.conf.all.accept_source_route = 0
#net.ipv6.conf.all.accept_source_route = 0
#
# Log Martian Packets
#net.ipv4.conf.all.log_martians = 1
#
###################################################################
# Magic system request Key
# 0=disable, 1=enable all, >1 bitmask of sysrq functions
# See https://www.kernel.org/doc/html/latest/admin-guide/sysrq.html
# for what other values do
#kernel.sysrq=438
#add by jianglinxuan
fs.file-max = 6553500
#kernel.core_pattern = /tmp/core-%p-%e-%t
net.core.netdev_budget_usecs=6000
net.ipv4.ipfrag_high_thresh=335544320
net.ipv4.ipfrag_time=10
net.core.netdev_budget_usecs=6000
net.ipv4.ipfrag_high_thresh=335544320
net.ipv4.ipfrag_time=10
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv4.conf.all.secure_redirects = 0
net.ipv4.conf.default.secure_redirects = 0
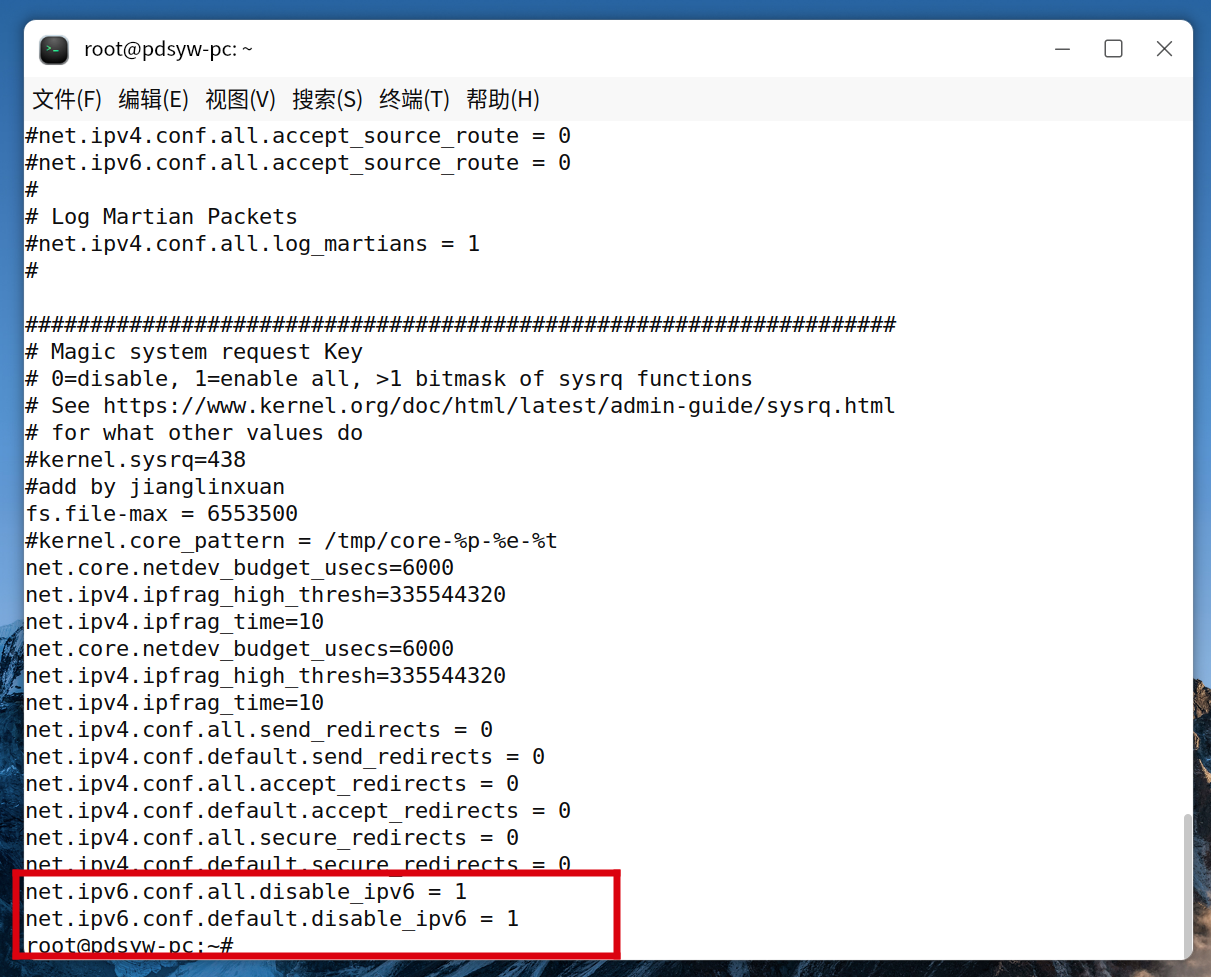
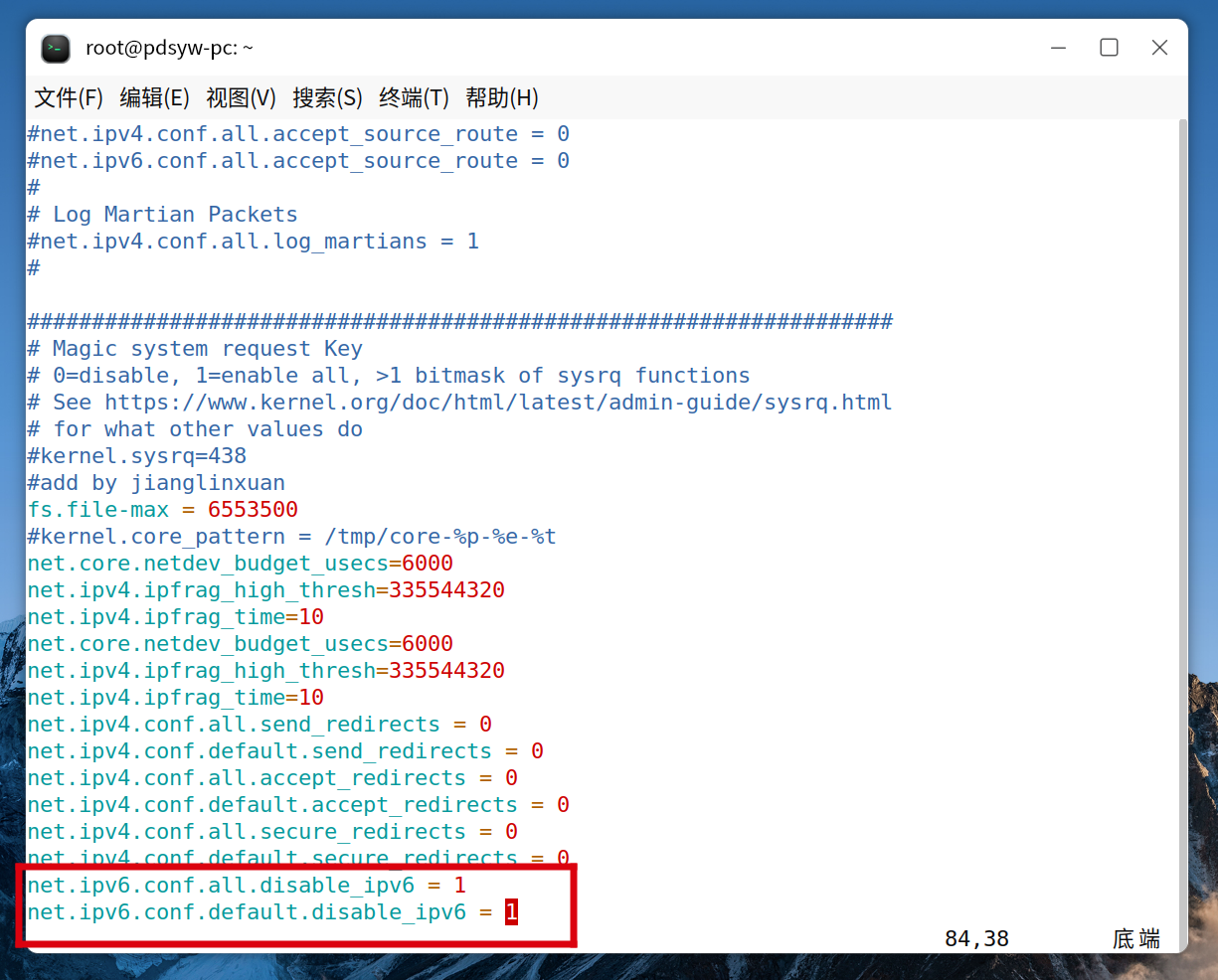
net.ipv6.conf.all.disable_ipv6 = 1
net.ipv6.conf.default.disable_ipv6 = 1
root@pdsyw-pc:~#
2.刷新配置,使配置生效
root@pdsyw-pc:~# sysctl -p /etc/sysctl.conf
fs.file-max = 6553500
net.core.netdev_budget_usecs = 6000
net.ipv4.ipfrag_high_thresh = 335544320
net.ipv4.ipfrag_time = 10
net.core.netdev_budget_usecs = 6000
net.ipv4.ipfrag_high_thresh = 335544320
net.ipv4.ipfrag_time = 10
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv4.conf.all.secure_redirects = 0
net.ipv4.conf.default.secure_redirects = 0
net.ipv6.conf.all.disable_ipv6 = 1
net.ipv6.conf.default.disable_ipv6 = 1
root@pdsyw-pc:~#

3.再次查看ip地址,已经没有ipv6地址
root@pdsyw-pc:~# ifconfig
enp1s0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether 74:45:2d:b1:1a:c9 txqueuelen 1000 (以太网)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
device interrupt 88 base 0xd000
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (本地环回)
RX packets 1237 bytes 73613 (73.6 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1237 bytes 73613 (73.6 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
wlan0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.0.149 netmask 255.255.255.0 broadcast 192.168.0.255
ether 74:45:2d:b1:51:a3 txqueuelen 1000 (以太网)
RX packets 62122 bytes 84675309 (84.6 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 12979 bytes 1027188 (1.0 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
root@pdsyw-pc:~#
[外链图片转存中…(img-nGenCVXc-1704701360908)]
4.再次ping百度,默认使用ipv4地址
pdsyw@pdsyw-pc:~/Desktop$ ping www.baidu.com
PING www.a.shifen.com (180.101.50.188) 56(84) bytes of data.
64 bytes from 180.101.50.188 (180.101.50.188): icmp_seq=1 ttl=50 time=24.5 ms
64 bytes from 180.101.50.188 (180.101.50.188): icmp_seq=2 ttl=50 time=84.5 ms
64 bytes from 180.101.50.188 (180.101.50.188): icmp_seq=3 ttl=50 time=114 ms
64 bytes from 180.101.50.188 (180.101.50.188): icmp_seq=4 ttl=50 time=51.8 ms
64 bytes from 180.101.50.188 (180.101.50.188): icmp_seq=5 ttl=50 time=121 ms
64 bytes from 180.101.50.188 (180.101.50.188): icmp_seq=6 ttl=50 time=79.7 ms
^C
--- www.a.shifen.com ping statistics ---
6 packets transmitted, 6 received, 0% packet loss, time 5007ms
rtt min/avg/max/mdev = 24.546/79.156/120.706/33.358 ms
pdsyw@pdsyw-pc:~/Desktop$

方法三:通过命令行修改
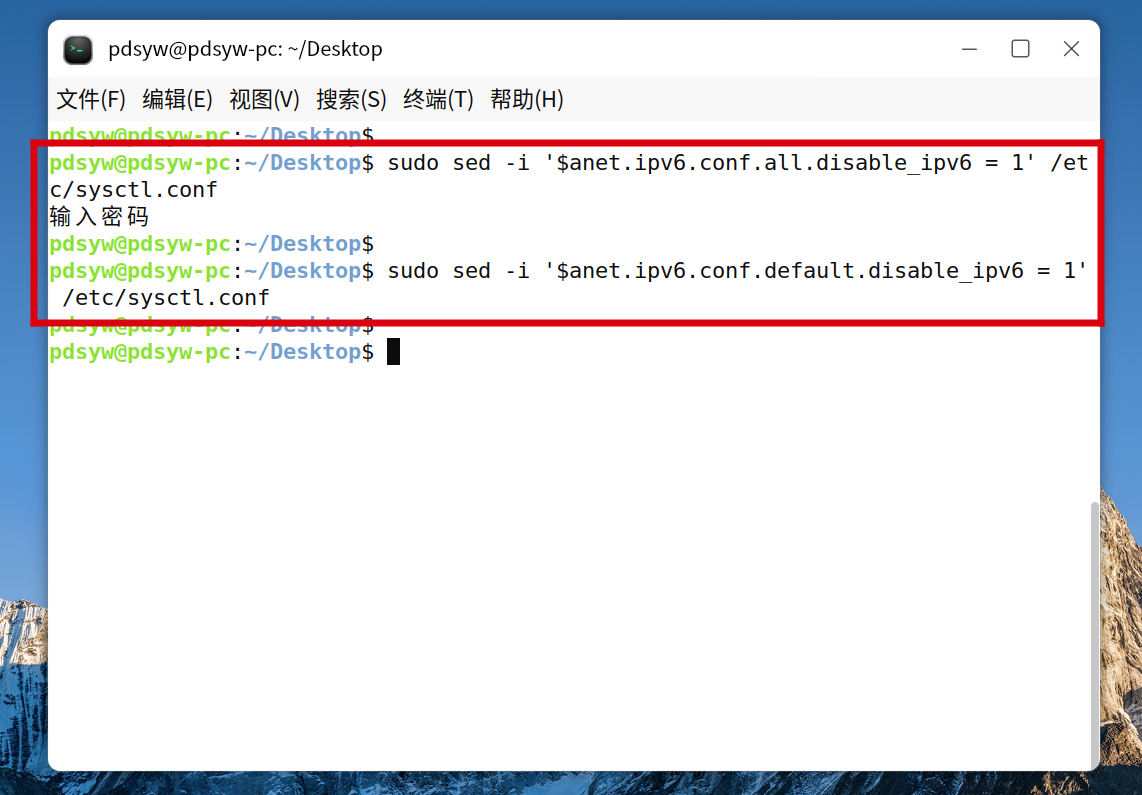
1.通过sed添加禁用ipv6的内容
pdsyw@pdsyw-pc:~/Desktop$ sudo sed -i '$anet.ipv6.conf.all.disable_ipv6 = 1' /etc/sysctl.conf
输入密码
pdsyw@pdsyw-pc:~/Desktop$
pdsyw@pdsyw-pc:~/Desktop$ sudo sed -i '$anet.ipv6.conf.default.disable_ipv6 = 1' /etc/sysctl.conf
pdsyw@pdsyw-pc:~/Desktop$
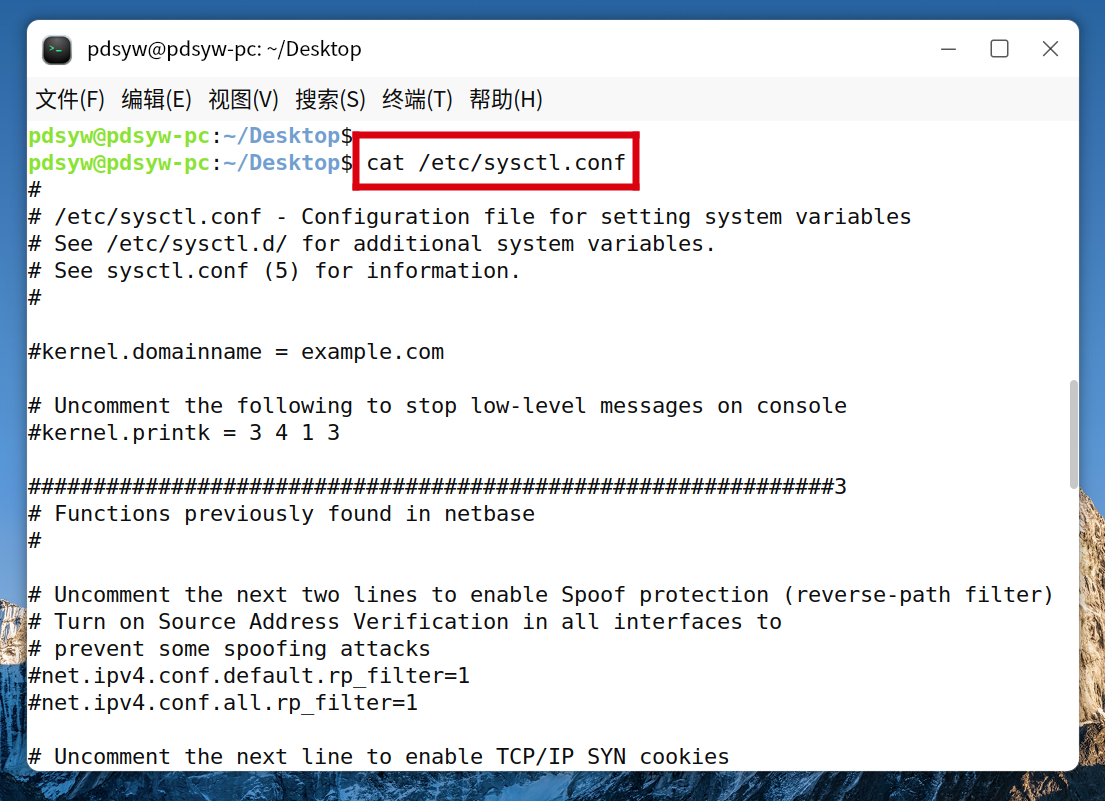
2.查看sysctl.conf已经添加完成
pdsyw@pdsyw-pc:~/Desktop$ cat /etc/sysctl.conf
#
# /etc/sysctl.conf - Configuration file for setting system variables
# See /etc/sysctl.d/ for additional system variables.
# See sysctl.conf (5) for information.
#
#kernel.domainname = example.com
# Uncomment the following to stop low-level messages on console
#kernel.printk = 3 4 1 3
##############################################################3
# Functions previously found in netbase
#
# Uncomment the next two lines to enable Spoof protection (reverse-path filter)
# Turn on Source Address Verification in all interfaces to
# prevent some spoofing attacks
#net.ipv4.conf.default.rp_filter=1
#net.ipv4.conf.all.rp_filter=1
# Uncomment the next line to enable TCP/IP SYN cookies
# See http://lwn.net/Articles/277146/
# Note: This may impact IPv6 TCP sessions too
#net.ipv4.tcp_syncookies=1
# Uncomment the next line to enable packet forwarding for IPv4
#net.ipv4.ip_forward=1
# Uncomment the next line to enable packet forwarding for IPv6
# Enabling this option disables Stateless Address Autoconfiguration
# based on Router Advertisements for this host
#net.ipv6.conf.all.forwarding=1
###################################################################
# Additional settings - these settings can improve the network
# security of the host and prevent against some network attacks
# including spoofing attacks and man in the middle attacks through
# redirection. Some network environments, however, require that these
# settings are disabled so review and enable them as needed.
#
# Do not accept ICMP redirects (prevent MITM attacks)
#net.ipv4.conf.all.accept_redirects = 0
#net.ipv6.conf.all.accept_redirects = 0
# _or_
# Accept ICMP redirects only for gateways listed in our default
# gateway list (enabled by default)
# net.ipv4.conf.all.secure_redirects = 1
#
# Do not send ICMP redirects (we are not a router)
#net.ipv4.conf.all.send_redirects = 0
#
# Do not accept IP source route packets (we are not a router)
#net.ipv4.conf.all.accept_source_route = 0
#net.ipv6.conf.all.accept_source_route = 0
#
# Log Martian Packets
#net.ipv4.conf.all.log_martians = 1
#
###################################################################
# Magic system request Key
# 0=disable, 1=enable all, >1 bitmask of sysrq functions
# See https://www.kernel.org/doc/html/latest/admin-guide/sysrq.html
# for what other values do
#kernel.sysrq=438
#add by jianglinxuan
fs.file-max = 6553500
#kernel.core_pattern = /tmp/core-%p-%e-%t
net.core.netdev_budget_usecs=6000
net.ipv4.ipfrag_high_thresh=335544320
net.ipv4.ipfrag_time=10
net.core.netdev_budget_usecs=6000
net.ipv4.ipfrag_high_thresh=335544320
net.ipv4.ipfrag_time=10
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv4.conf.all.secure_redirects = 0
net.ipv4.conf.default.secure_redirects = 0
net.ipv6.conf.all.disable_ipv6 = 1
net.ipv6.conf.default.disable_ipv6 = 1
pdsyw@pdsyw-pc:~/Desktop$
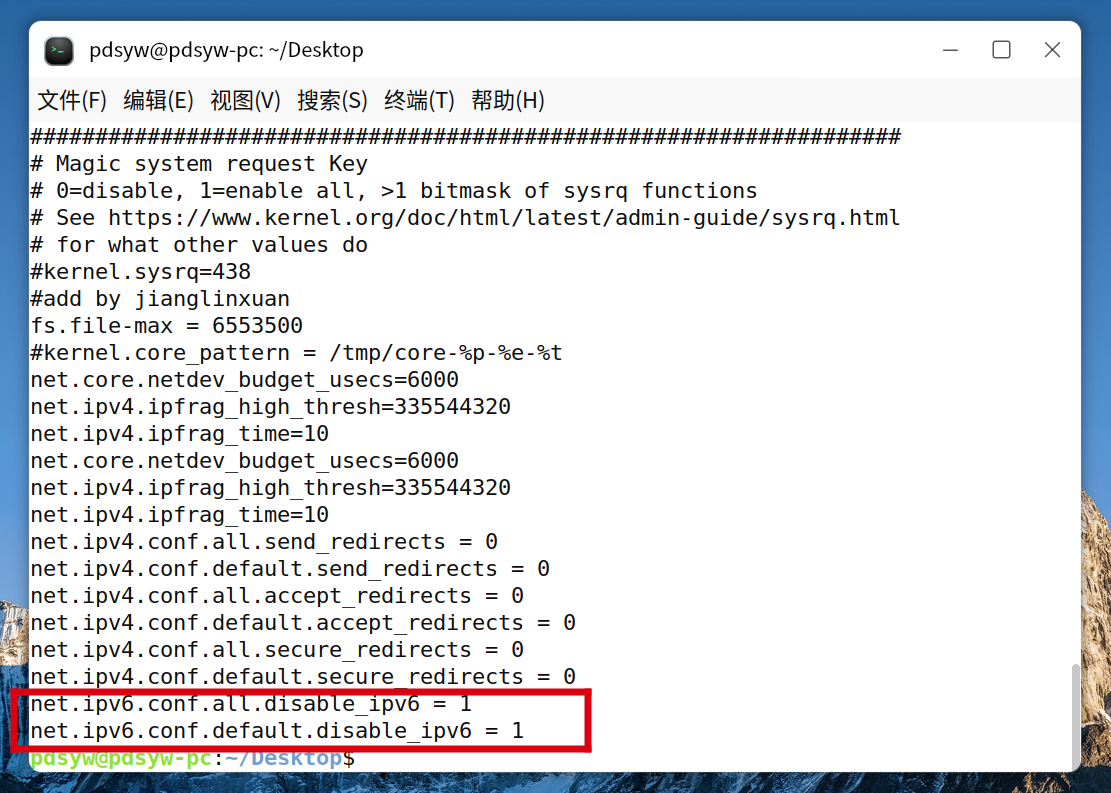
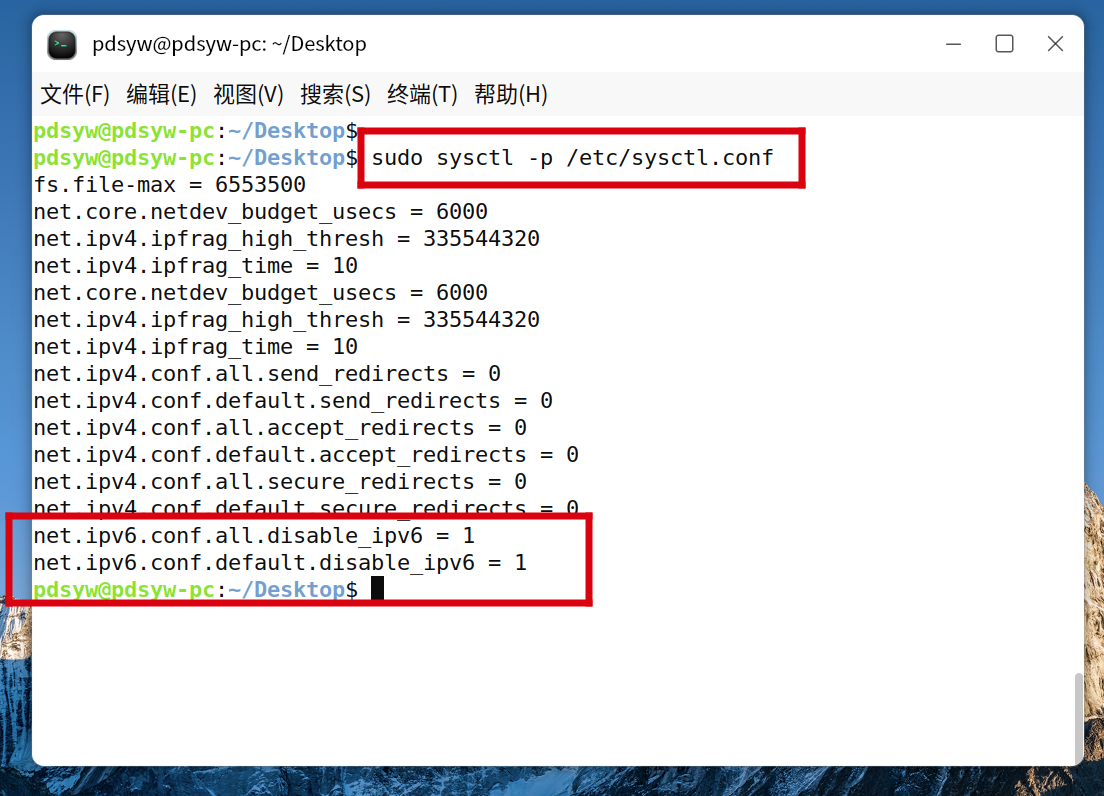
3.刷新配置,使配置生效
pdsyw@pdsyw-pc:~/Desktop$ sudo sysctl -p /etc/sysctl.conf
fs.file-max = 6553500
net.core.netdev_budget_usecs = 6000
net.ipv4.ipfrag_high_thresh = 335544320
net.ipv4.ipfrag_time = 10
net.core.netdev_budget_usecs = 6000
net.ipv4.ipfrag_high_thresh = 335544320
net.ipv4.ipfrag_time = 10
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv4.conf.all.secure_redirects = 0
net.ipv4.conf.default.secure_redirects = 0
net.ipv6.conf.all.disable_ipv6 = 1
net.ipv6.conf.default.disable_ipv6 = 1
pdsyw@pdsyw-pc:~/Desktop$
4.再次查看ip地址,已经没有ipv6地址
root@pdsyw-pc:~# ifconfig
enp1s0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether 74:45:2d:b1:1a:c9 txqueuelen 1000 (以太网)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
device interrupt 88 base 0xd000
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
loop txqueuelen 1000 (本地环回)
RX packets 1237 bytes 73613 (73.6 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1237 bytes 73613 (73.6 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
wlan0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.0.149 netmask 255.255.255.0 broadcast 192.168.0.255
ether 74:45:2d:b1:51:a3 txqueuelen 1000 (以太网)
RX packets 62122 bytes 84675309 (84.6 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 12979 bytes 1027188 (1.0 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
root@pdsyw-pc:~#
5.再次ping百度,默认使用ipv4地址
pdsyw@pdsyw-pc:~/Desktop$ ping www.baidu.com
PING www.a.shifen.com (180.101.50.188) 56(84) bytes of data.
64 bytes from 180.101.50.188 (180.101.50.188): icmp_seq=1 ttl=50 time=24.5 ms
64 bytes from 180.101.50.188 (180.101.50.188): icmp_seq=2 ttl=50 time=84.5 ms
64 bytes from 180.101.50.188 (180.101.50.188): icmp_seq=3 ttl=50 time=114 ms
64 bytes from 180.101.50.188 (180.101.50.188): icmp_seq=4 ttl=50 time=51.8 ms
64 bytes from 180.101.50.188 (180.101.50.188): icmp_seq=5 ttl=50 time=121 ms
64 bytes from 180.101.50.188 (180.101.50.188): icmp_seq=6 ttl=50 time=79.7 ms
^C
--- www.a.shifen.com ping statistics ---
6 packets transmitted, 6 received, 0% packet loss, time 5007ms
rtt min/avg/max/mdev = 24.546/79.156/120.706/33.358 ms
pdsyw@pdsyw-pc:~/Desktop$

通过在麒麟KYLINOS上禁用IPv6,您可以根据特定的网络需求或测试要求调整系统配置。无论是通过图形化界面、修改配置文件还是命令行,每种方法都有其适用场景。希望这篇文章能帮助到需要在麒麟KYLINOS上禁用IPv6的朋友们。如果你有任何问题或者更多的经验分享,请在评论区留言,我们一起讨论。
最后,如果你觉得这篇文章有用,请分享转发。点个关注和在看吧,让我们一起探索和学习更多关于Linux系统管理和网络配置的知识!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!