9. DashBoard
2023-12-17 20:36:17
9. DashBoard
-
在kubernetes中完成的所有操作都是通过命令行工具kubectl完成的。
-
为了提供更丰富的用户体验,kubernetes还开发了一个基于web的用户界面(Dashboard)。
-
用户可以使用Dashboard部署容器化的应用,还可以监控应用的状态,执行故障排查以及管理kubernetes中各种资源。
9.1 部署Dashboard
下载yaml,并运行Dashboard
[root@k8s-master ~]# wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.7.0/aio/deploy/recommended.yaml
--2023-12-18 02:00:42-- https://raw.githubusercontent.com/kubernetes/dashboard/v2.7.0/aio/deploy/recommended.yaml
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.111.133, 185.199.108.133, 185.199.109.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.111.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 7621 (7.4K) [text/plain]
Saving to: ‘recommended.yaml’
recommended.yaml 100%[============================================================>] 7.44K 15.9KB/s in 0.5s
2023-12-18 02:00:45 (15.9 KB/s) - ‘recommended.yaml’ saved [7621/7621]
[root@k8s-master ~]# ls
anaconda-ks.cfg inventory kube-flannel.yml recommended.yaml
# 修改kubernetes-dashboard的Service类型
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
type: NodePort # 新增
ports:
- port: 443
targetPort: 8443
nodePort: 30001 # 新增
selector:
k8s-app: kubernetes-dashboard
[root@k8s-master ~]# vi recommended.yaml
[root@k8s-master ~]# cat recommended.yaml
# Copyright 2017 The Kubernetes Authors.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
# You may obtain a copy of the License at
#
# http://www.apache.org/licenses/LICENSE-2.0
#
# Unless required by applicable law or agreed to in writing, software
# distributed under the License is distributed on an "AS IS" BASIS,
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
apiVersion: v1
kind: Namespace
metadata:
name: kubernetes-dashboard
---
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
type: NodePort
ports:
- port: 443
targetPort: 8443
nodePort: 30001
selector:
k8s-app: kubernetes-dashboard
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-certs
namespace: kubernetes-dashboard
type: Opaque
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-csrf
namespace: kubernetes-dashboard
type: Opaque
data:
csrf: ""
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-key-holder
namespace: kubernetes-dashboard
type: Opaque
---
kind: ConfigMap
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-settings
namespace: kubernetes-dashboard
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
rules:
# Allow Dashboard to get, update and delete Dashboard exclusive secrets.
- apiGroups: [""]
resources: ["secrets"]
resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs", "kubernetes-dashboard-csrf"]
verbs: ["get", "update", "delete"]
# Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map.
- apiGroups: [""]
resources: ["configmaps"]
resourceNames: ["kubernetes-dashboard-settings"]
verbs: ["get", "update"]
# Allow Dashboard to get metrics.
- apiGroups: [""]
resources: ["services"]
resourceNames: ["heapster", "dashboard-metrics-scraper"]
verbs: ["proxy"]
- apiGroups: [""]
resources: ["services/proxy"]
resourceNames: ["heapster", "http:heapster:", "https:heapster:", "dashboard-metrics-scraper", "http:dashboard-metrics-scraper"]
verbs: ["get"]
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
rules:
# Allow Metrics Scraper to get metrics from the Metrics server
- apiGroups: ["metrics.k8s.io"]
resources: ["pods", "nodes"]
verbs: ["get", "list", "watch"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kubernetes-dashboard
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: kubernetes-dashboard
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
spec:
securityContext:
seccompProfile:
type: RuntimeDefault
containers:
- name: kubernetes-dashboard
image: kubernetesui/dashboard:v2.7.0
imagePullPolicy: Always
ports:
- containerPort: 8443
protocol: TCP
args:
- --auto-generate-certificates
- --namespace=kubernetes-dashboard
# Uncomment the following line to manually specify Kubernetes API server Host
# If not specified, Dashboard will attempt to auto discover the API server and connect
# to it. Uncomment only if the default does not work.
# - --apiserver-host=http://my-address:port
volumeMounts:
- name: kubernetes-dashboard-certs
mountPath: /certs
# Create on-disk volume to store exec logs
- mountPath: /tmp
name: tmp-volume
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsUser: 1001
runAsGroup: 2001
volumes:
- name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard
nodeSelector:
"kubernetes.io/os": linux
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
---
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: dashboard-metrics-scraper
name: dashboard-metrics-scraper
namespace: kubernetes-dashboard
spec:
ports:
- port: 8000
targetPort: 8000
selector:
k8s-app: dashboard-metrics-scraper
---
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: dashboard-metrics-scraper
name: dashboard-metrics-scraper
namespace: kubernetes-dashboard
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: dashboard-metrics-scraper
template:
metadata:
labels:
k8s-app: dashboard-metrics-scraper
spec:
securityContext:
seccompProfile:
type: RuntimeDefault
containers:
- name: dashboard-metrics-scraper
image: kubernetesui/metrics-scraper:v1.0.8
ports:
- containerPort: 8000
protocol: TCP
livenessProbe:
httpGet:
scheme: HTTP
path: /
port: 8000
initialDelaySeconds: 30
timeoutSeconds: 30
volumeMounts:
- mountPath: /tmp
name: tmp-volume
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsUser: 1001
runAsGroup: 2001
serviceAccountName: kubernetes-dashboard
nodeSelector:
"kubernetes.io/os": linux
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
volumes:
- name: tmp-volume
emptyDir: {}
# 部署
[root@k8s-master ~]# kubectl apply -f recommended.yaml
namespace/kubernetes-dashboard created
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
service/dashboard-metrics-scraper created
deployment.apps/dashboard-metrics-scraper created
# 查看namespace下的kubernetes-dashboard下的资源
[root@k8s-master ~]# kubectl get pod,svc -n kubernetes-dashboard
NAME READY STATUS RESTARTS AGE
pod/dashboard-metrics-scraper-5657497c4c-jw9km 0/1 ContainerCreating 0 34s
pod/kubernetes-dashboard-78f87ddfc-vcfzt 0/1 ContainerCreating 0 34s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/dashboard-metrics-scraper ClusterIP 10.101.86.124 <none> 8000/TCP 34s
service/kubernetes-dashboard NodePort 10.98.6.114 <none> 443:30001/TCP 34s
[root@k8s-master ~]# kubectl get pods -n kubernetes-dashboard -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
dashboard-metrics-scraper-5657497c4c-jw9km 1/1 Running 0 42s 10.244.1.9 k8s-node1 <none> <none>
kubernetes-dashboard-78f87ddfc-vcfzt 1/1 Running 0 42s 10.244.2.9 k8s-node2 <none> <none>
[root@k8s-master ~]#
创建访问账户,获取token
[root@k8s-master ~]# mkdir dashboard
[root@k8s-master ~]# cd dashboard/
[root@k8s-master dashboard]# ls
[root@k8s-master dashboard]# vi user.yaml
[root@k8s-master dashboard]# vi ClusterRoleBinding
[root@k8s-master dashboard]# cat user.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin
namespace: kubernetes-dashboard
[root@k8s-master dashboard]# cat ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: admin
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin
namespace: kubernetes-dashboard
[root@k8s-master dashboard]# kubectl apply -f user.yaml
serviceaccount/admin created
[root@k8s-master dashboard]# kubectl apply -f ClusterRoleBinding
clusterrolebinding.rbac.authorization.k8s.io/admin created
[root@k8s-master dashboard]# kubectl get -f user.yaml
NAME SECRETS AGE
admin 0 14s
[root@k8s-master dashboard]# kubectl get -f ClusterRoleBinding
NAME ROLE AGE
admin ClusterRole/cluster-admin 17s
[root@k8s-master dashboard]# kubectl -n kubernetes-dashboard create token admin
eyJhbGciOiJSUzI1NiIsImtpZCI6Ikk0Y2JXVDljaXZkWlotbzJTQU5KWTlkRXJnR3VSVFhKYnpUZ3JNTmNBLWMifQ.eyJhdWQiOlsiaHR0cHM6Ly9rdWJlcm5ldGVzLmRlZmF1bHQuc3ZjLmNsdXN0ZXIubG9jYWwiXSwiZXhwIjoxNzAyODQxNTY5LCJpYXQiOjE3MDI4Mzc5NjksImlzcyI6Imh0dHBzOi8va3ViZXJuZXRlcy5kZWZhdWx0LnN2Yy5jbHVzdGVyLmxvY2FsIiwia3ViZXJuZXRlcy5pbyI6eyJuYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsInNlcnZpY2VhY2NvdW50Ijp7Im5hbWUiOiJhZG1pbiIsInVpZCI6ImVhNWMwNDZlLTM4ODItNDdhZS1iZGQ1LTkwZTFhNjU4ODc5ZSJ9fSwibmJmIjoxNzAyODM3OTY5LCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZXJuZXRlcy1kYXNoYm9hcmQ6YWRtaW4ifQ.DtEBQjFJBeMbcr_Daprk1kV5_5Jz2fno0k5QrTGX7CF12vedX1KYQXgQQKiXWhVEgJu5Q_bx7qmGcupQZCyX8EyYu5CN6-Gzedcp8dB4_C_CIVGj9XQPeaPxpIfzryovGE972Z2I6JUaJx_cyAbo0HeFvs1CT6rPvJydr60bKjTztxp_NixCWk962mBsPRQREkbhAOiJUUSlgNQs-22ETVU1MJeExdzTxhw4nOAFRjiQ_RbJG93NW7CaXwnTL65DvoBa_7xztXMsQ19vBxvESgF_O7lKll0g7wY459_gEh_234z2kXEpD1sCLsVoUmVx477-98PygEfseNoU-MXFPw
[root@k8s-master dashboard]# kubectl get serviceaccount -n kubernetes-dashboard
NAME SECRETS AGE
admin 0 20m
default 0 49m
kubernetes-dashboard 0 49m
# 保存在文档以便以后使用
[root@k8s-master dashboard]# vi token
[root@k8s-master dashboard]# cat token
eyJhbGciOiJSUzI1NiIsImtpZCI6Ikk0Y2JXVDljaXZkWlotbzJTQU5KWTlkRXJnR3VSVFhKYnpUZ3JNTmNBLWMifQ.eyJhdWQiOlsiaHR0cHM6Ly9rdWJlcm5ldGVzLmRlZmF1bHQuc3ZjLmNsdXN0ZXIubG9jYWwiXSwiZXhwIjoxNzAyODQxNTY5LCJpYXQiOjE3MDI4Mzc5NjksImlzcyI6Imh0dHBzOi8va3ViZXJuZXRlcy5kZWZhdWx0LnN2Yy5jbHVzdGVyLmxvY2FsIiwia3ViZXJuZXRlcy5pbyI6eyJuYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsInNlcnZpY2VhY2NvdW50Ijp7Im5hbWUiOiJhZG1pbiIsInVpZCI6ImVhNWMwNDZlLTM4ODItNDdhZS1iZGQ1LTkwZTFhNjU4ODc5ZSJ9fSwibmJmIjoxNzAyODM3OTY5LCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZXJuZXRlcy1kYXNoYm9hcmQ6YWRtaW4ifQ.DtEBQjFJBeMbcr_Daprk1kV5_5Jz2fno0k5QrTGX7CF12vedX1KYQXgQQKiXWhVEgJu5Q_bx7qmGcupQZCyX8EyYu5CN6-Gzedcp8dB4_C_CIVGj9XQPeaPxpIfzryovGE972Z2I6JUaJx_cyAbo0HeFvs1CT6rPvJydr60bKjTztxp_NixCWk962mBsPRQREkbhAOiJUUSlgNQs-22ETVU1MJeExdzTxhw4nOAFRjiQ_RbJG93NW7CaXwnTL65DvoBa_7xztXMsQ19vBxvESgF_O7lKll0g7wY459_gEh_234z2kXEpD1sCLsVoUmVx477-98PygEfseNoU-MXFPw
如果需要删除admin ServiceAccount和ClusterRoleBinding。
kubectl -n kubernetes-dashboard delete serviceaccount admin
kubectl -n kubernetes-dashboard delete clusterrolebinding admin
** 通过浏览器访问Dashboard的UI**
-
在登录页面上输入上面的token
将生成的token复制粘贴到这个
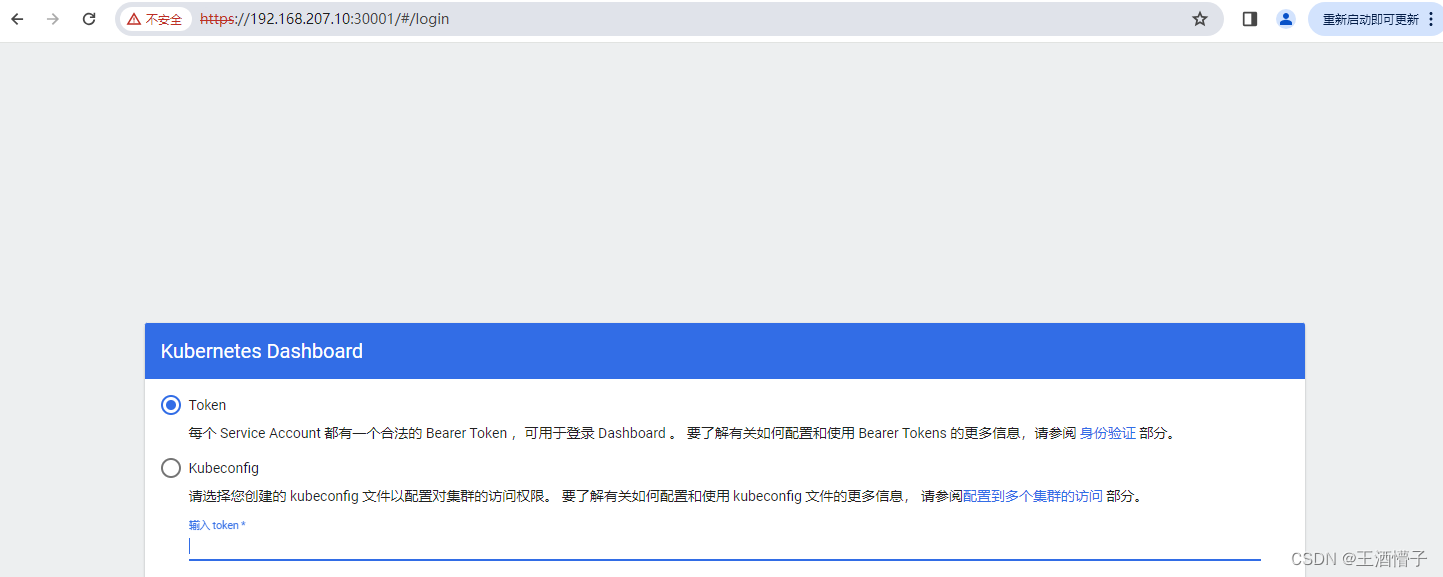
出现下面界面代表登录成功
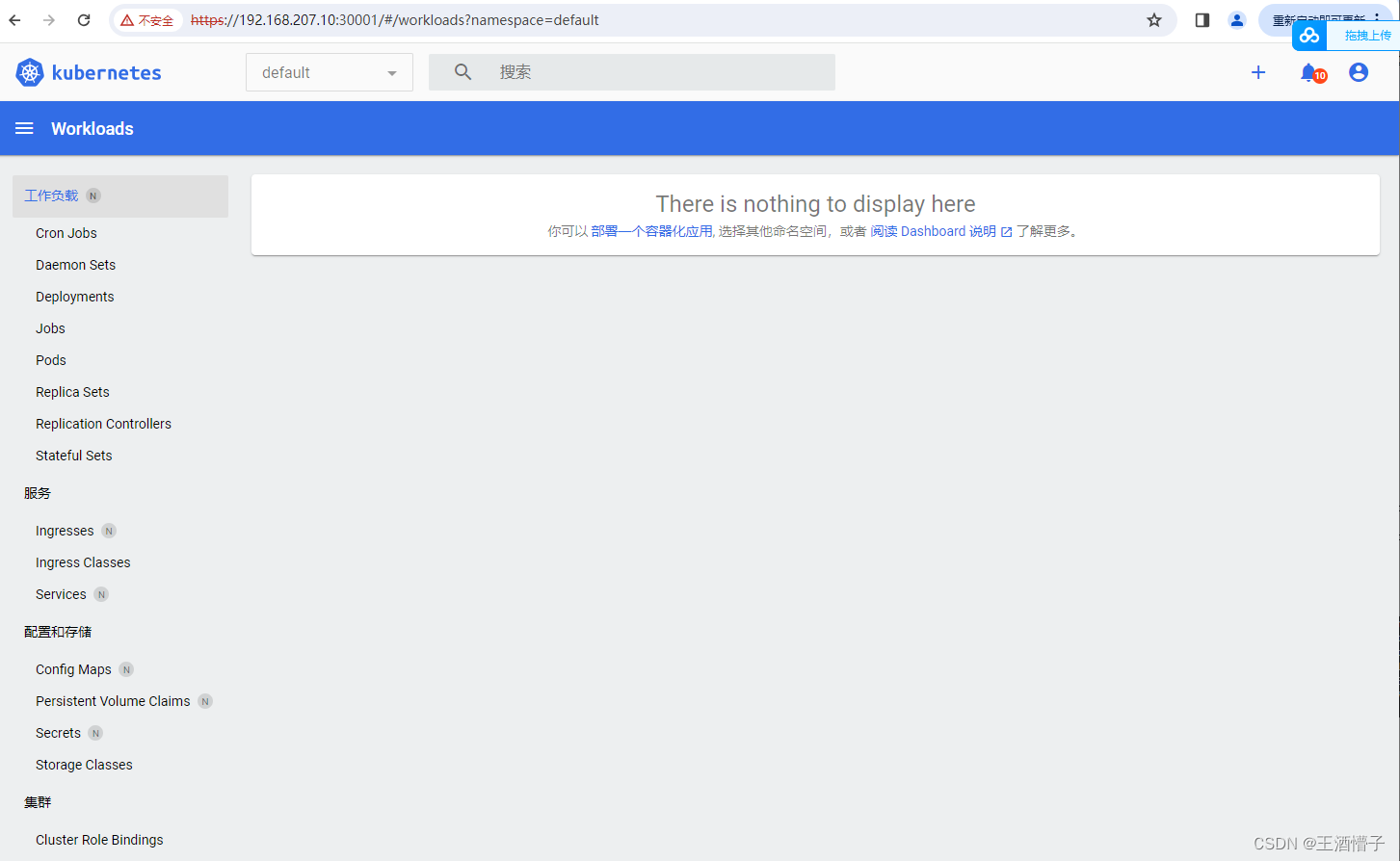
9.2 使用DashBoard
创建一个pod查看
[root@k8s-master dashboard]# vi httpd.yaml
[root@k8s-master dashboard]# cat httpd.yaml
apiVersion: v1
kind: Pod
metadata:
name: pod-pullimage
namespace: dev
labels:
app: httpdlab
spec:
nodeName: k8s-node2
containers:
- name: httpd
image: httpd:latest
imagePullPolicy: IfNotPresent
[root@k8s-master dashboard]# kubectl apply -f httpd.yaml
pod/pod-pullimage created
[root@k8s-master dashboard]# kubectl get -f httpd.yaml
NAME READY STATUS RESTARTS AGE
pod-pullimage 1/1 Running 0 6s
[root@k8s-master dashboard]# kubectl get pods -n dev
NAME READY STATUS RESTARTS AGE
pod-pullimage 1/1 Running 0 16s
可以查看到有一个在namespace是dev运行的pod
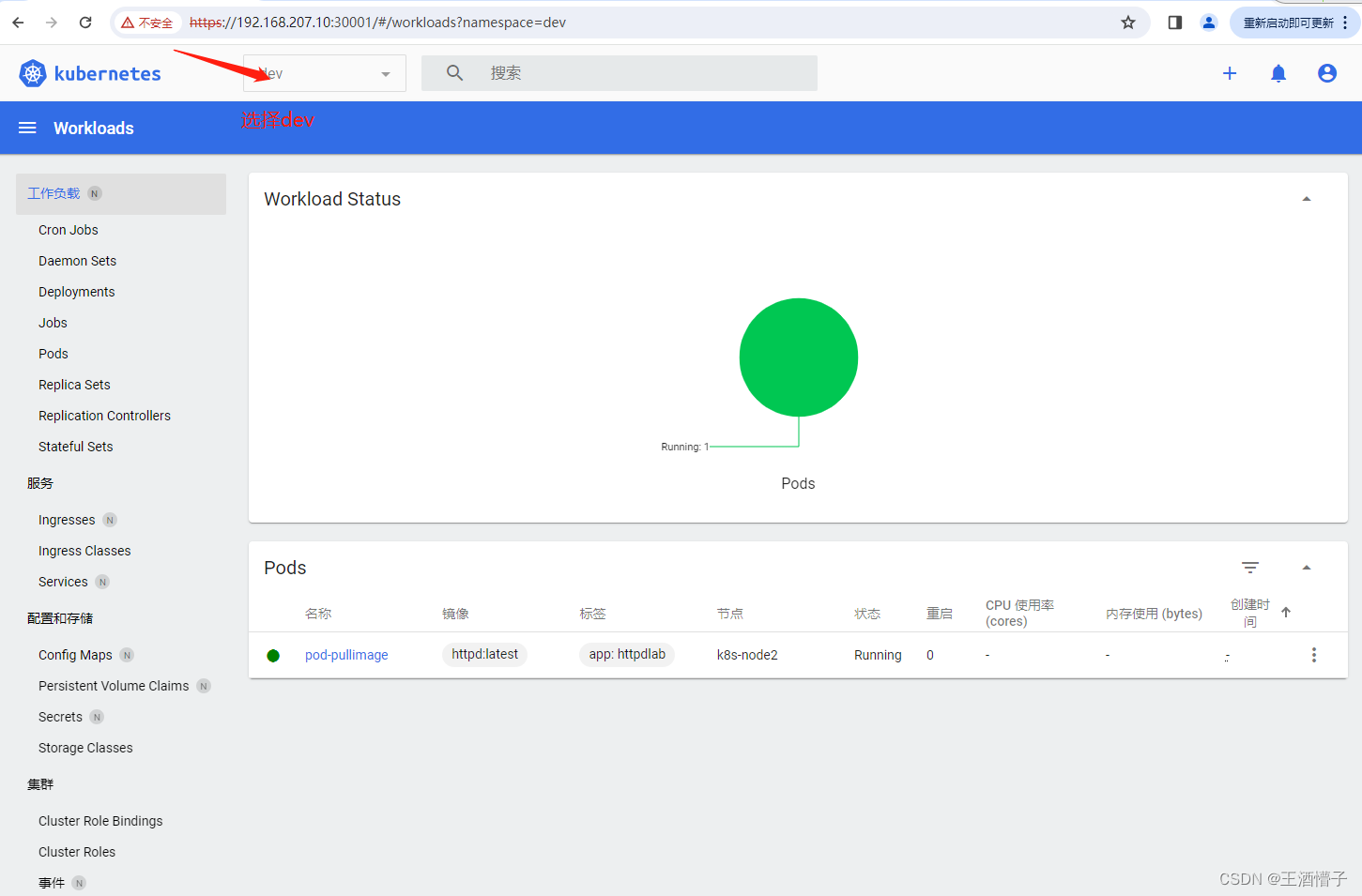
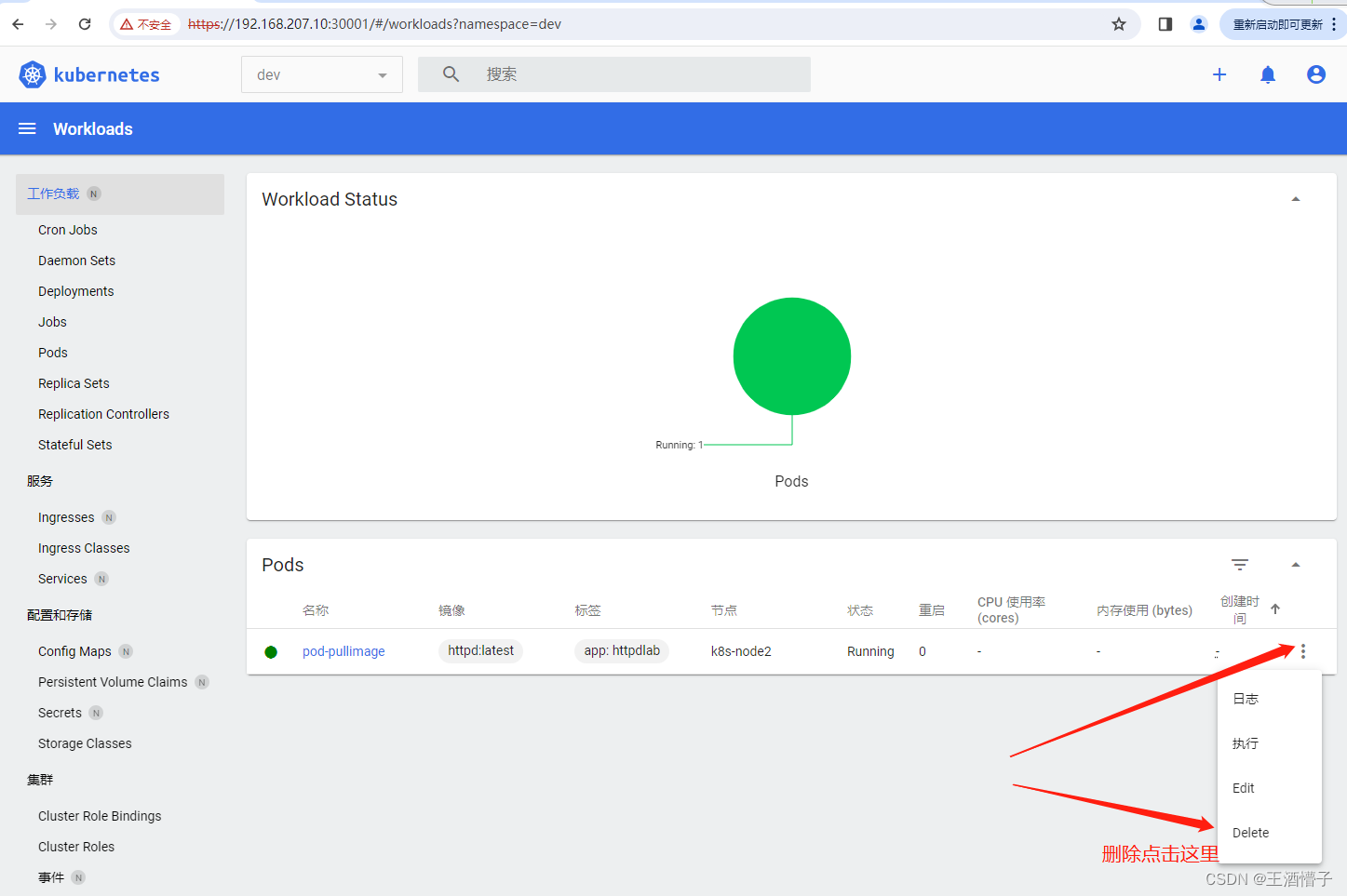
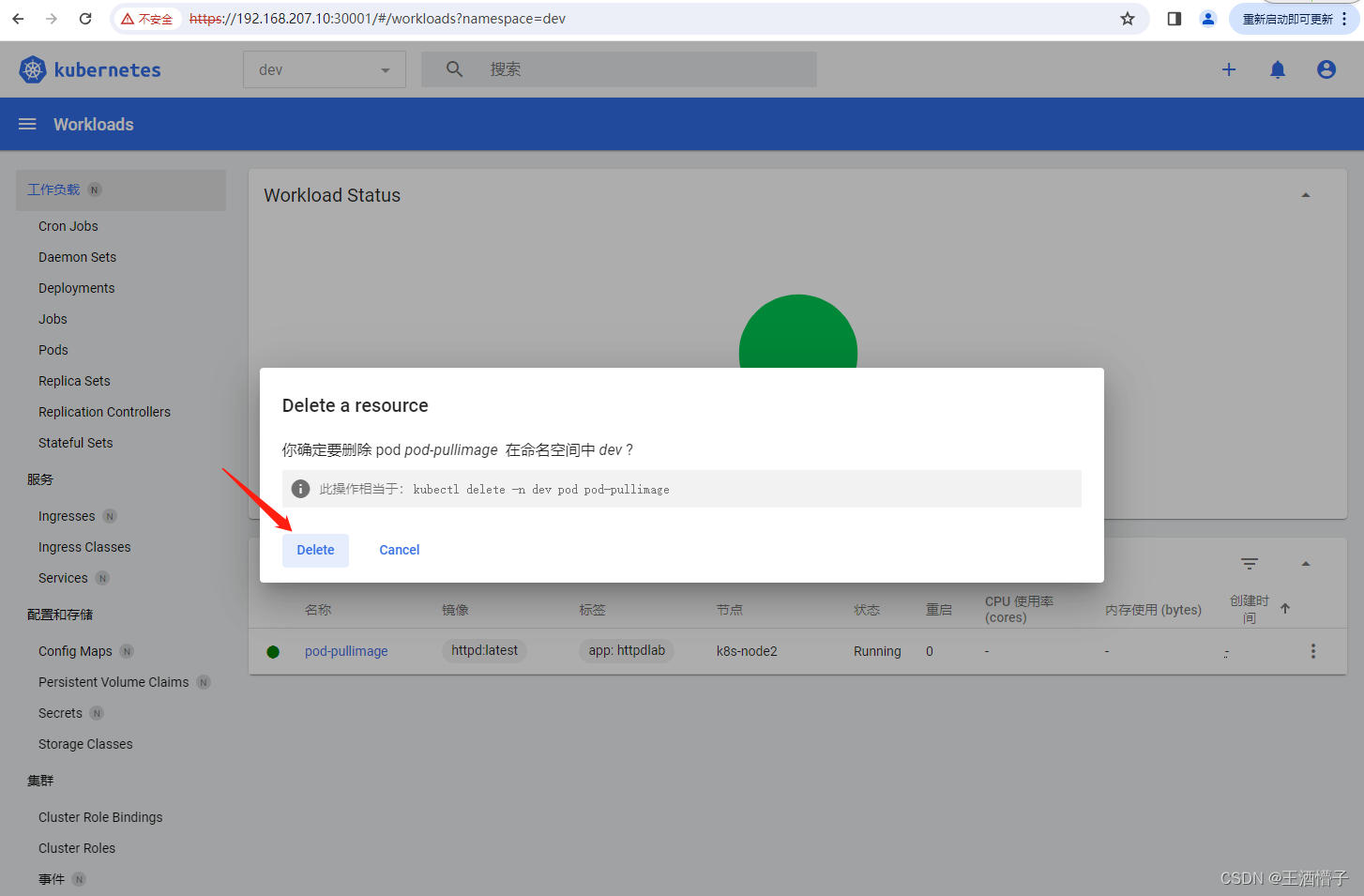
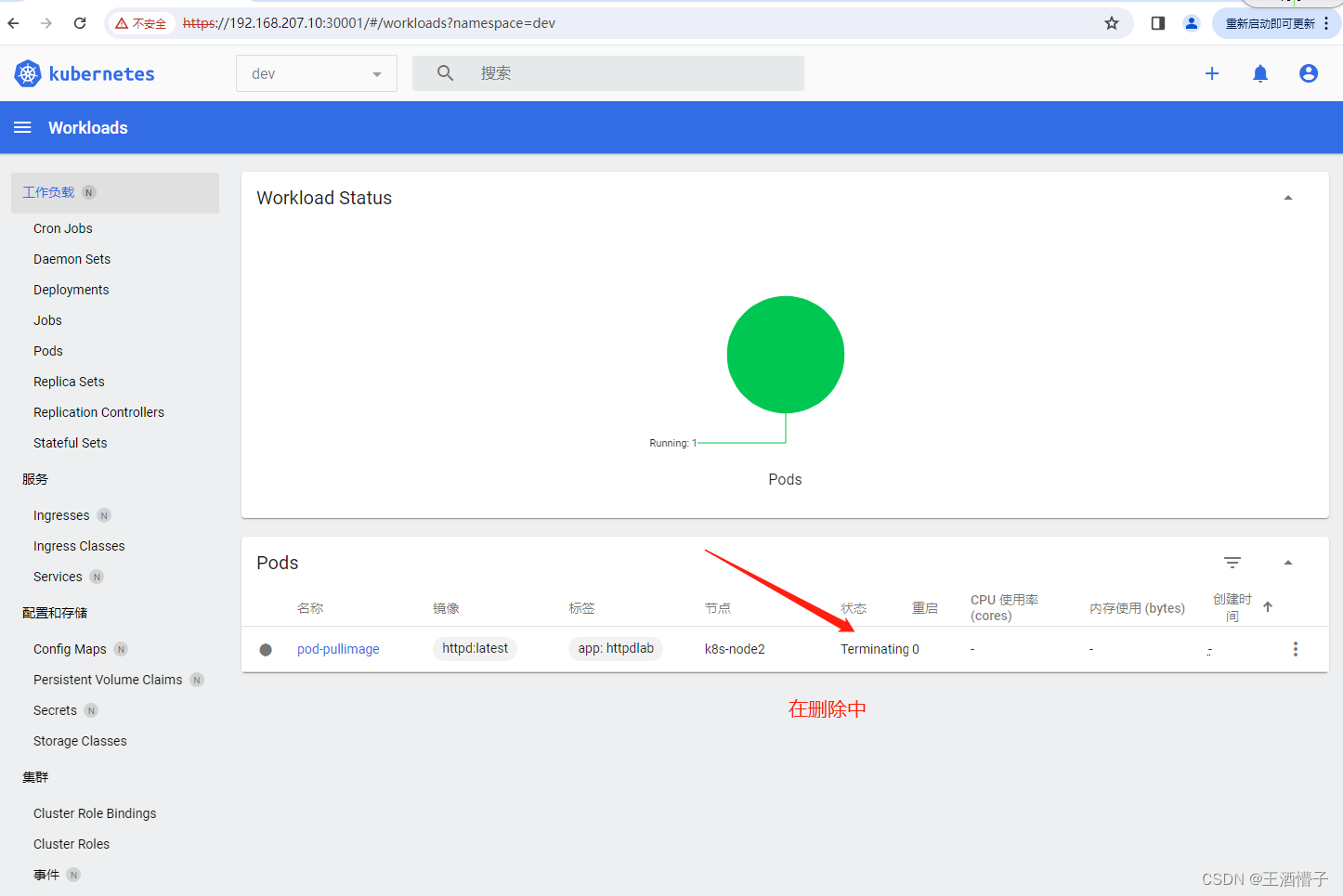
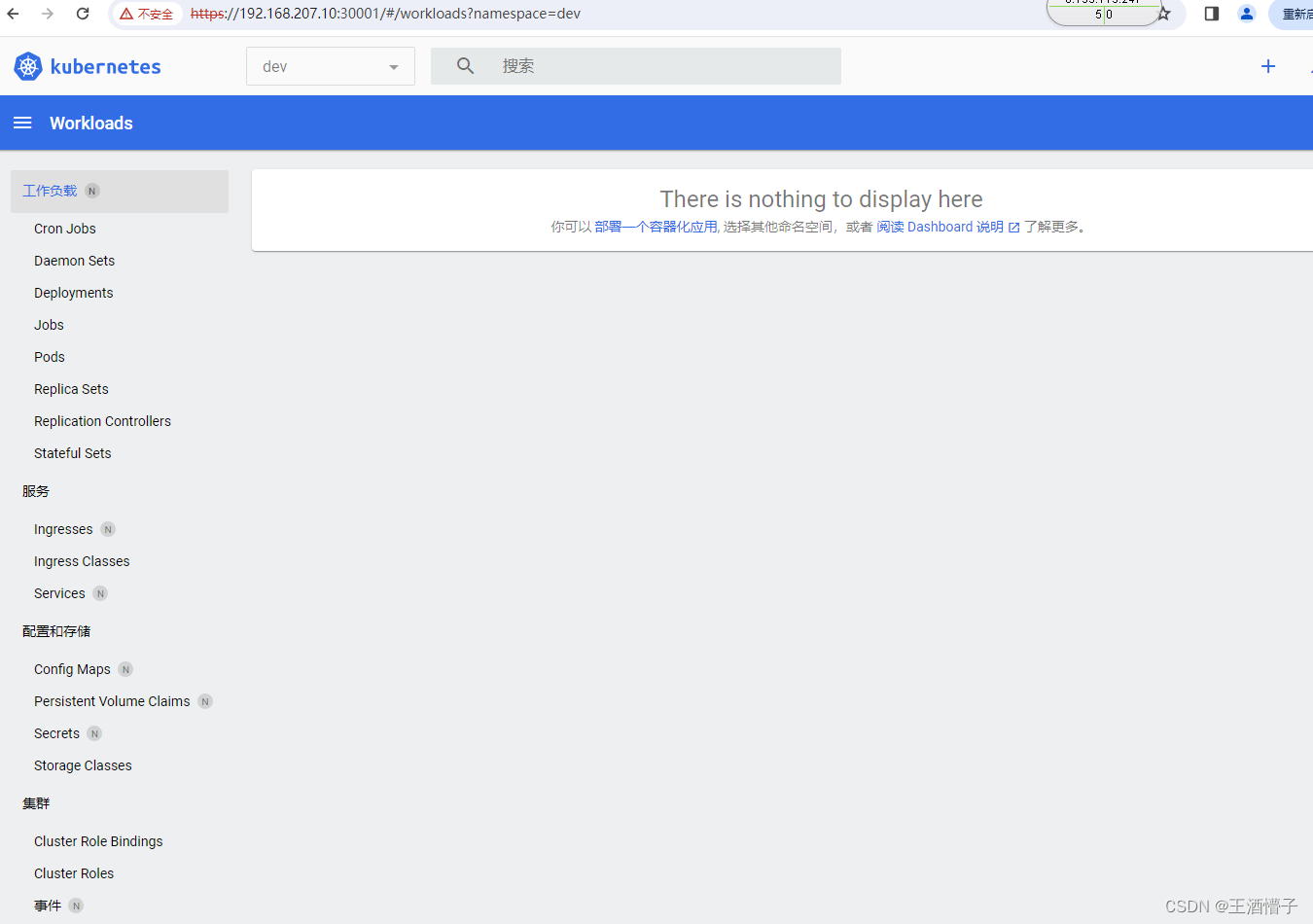
删除成功
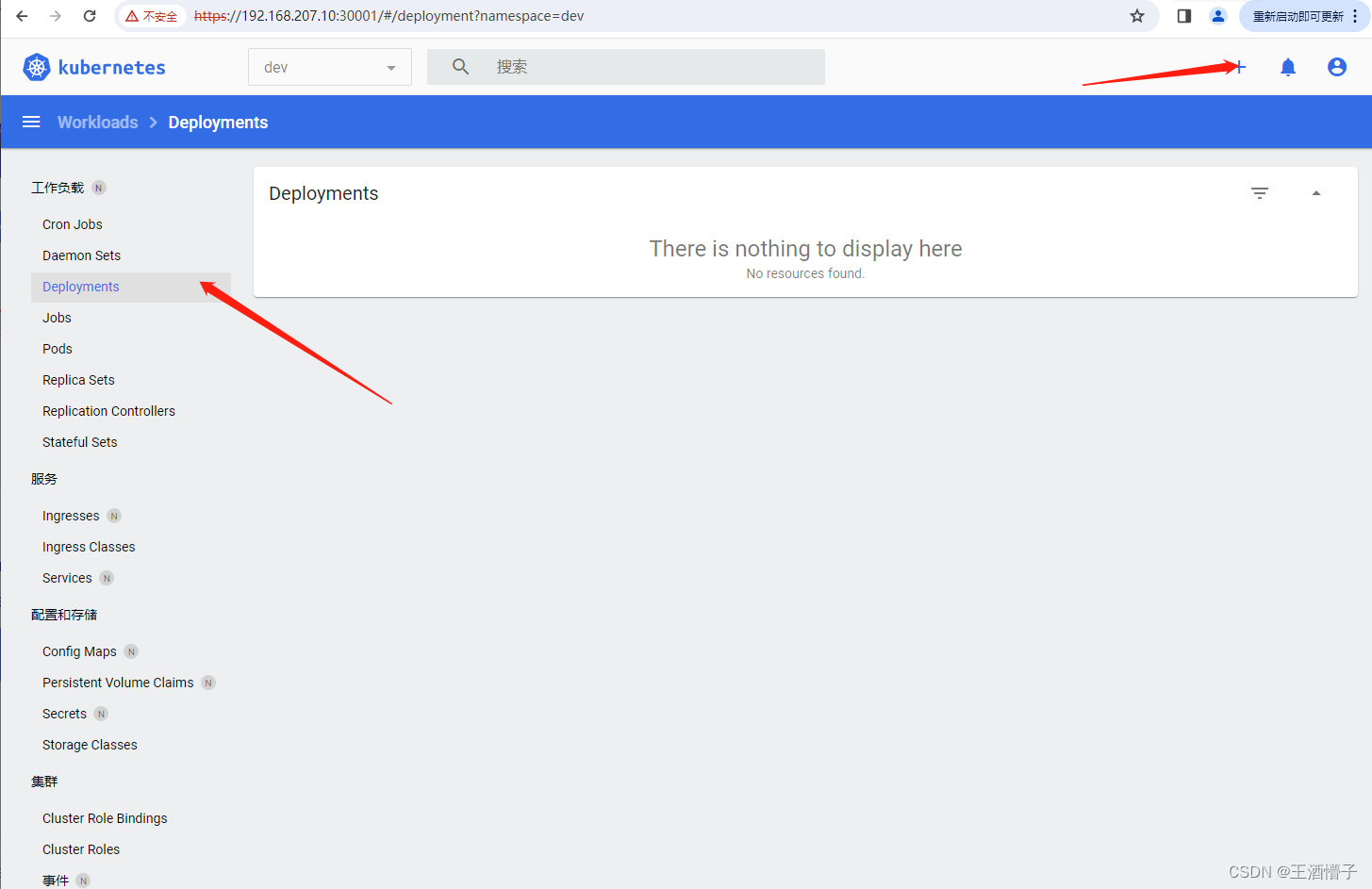
创建deploy
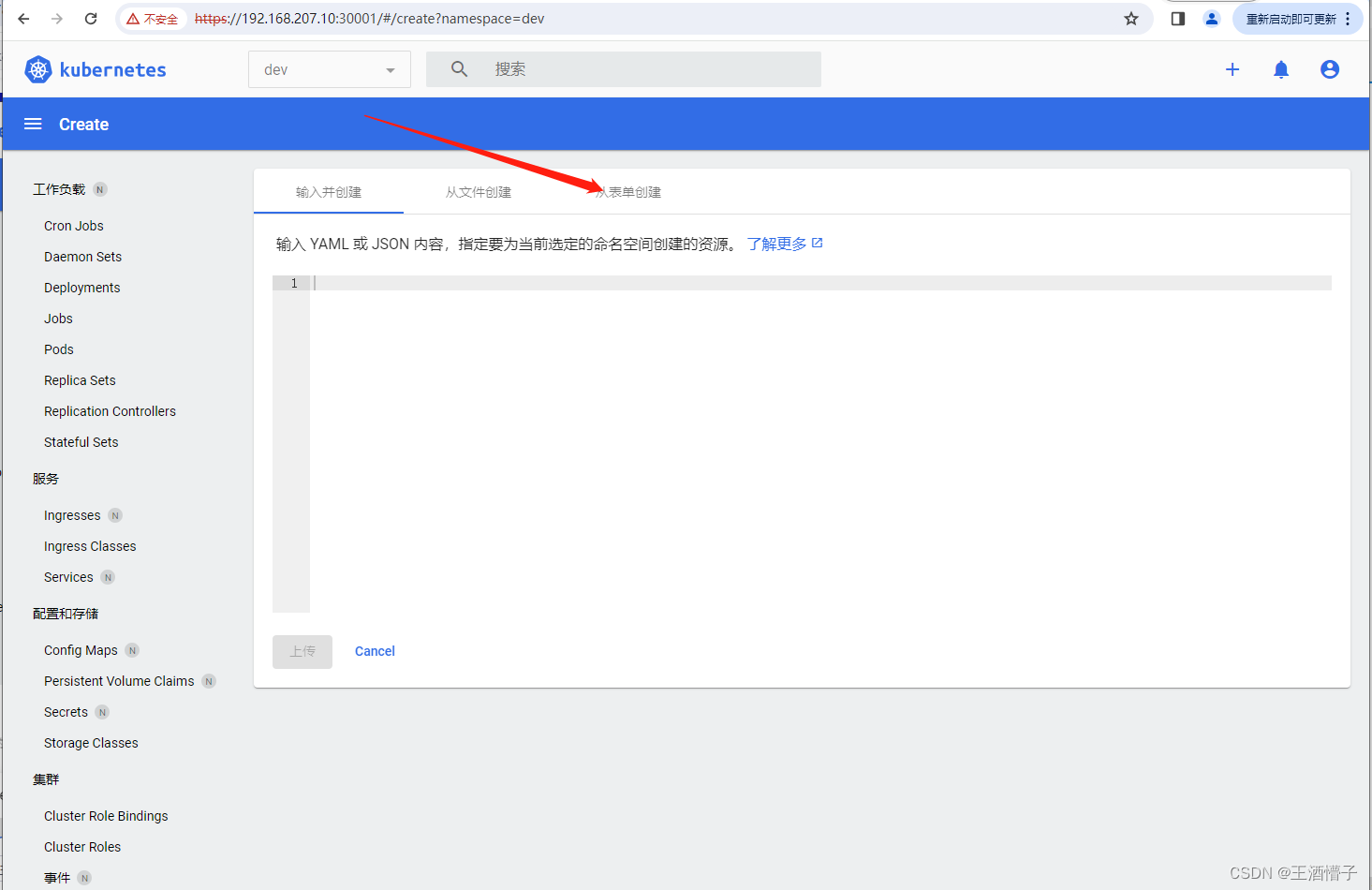
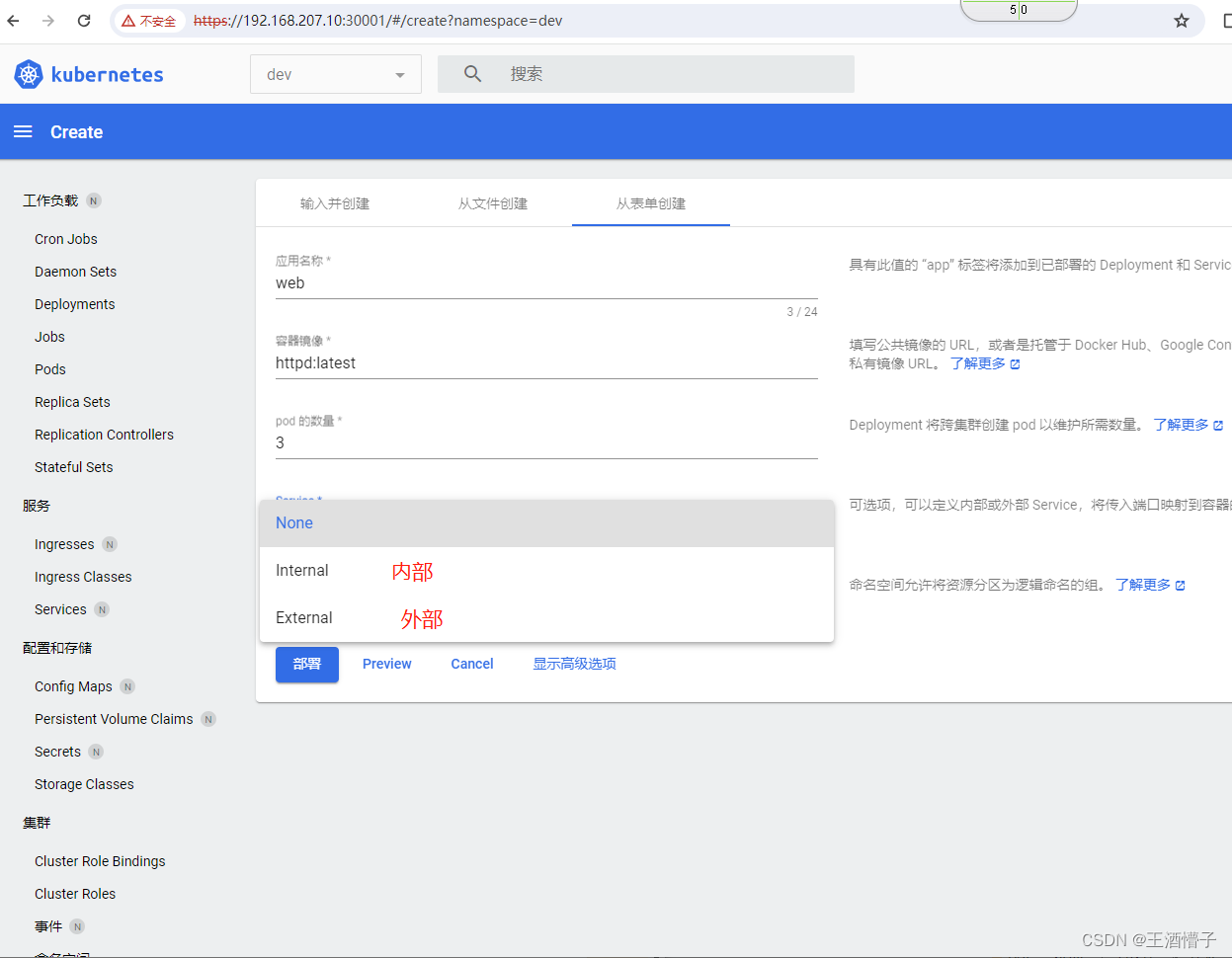
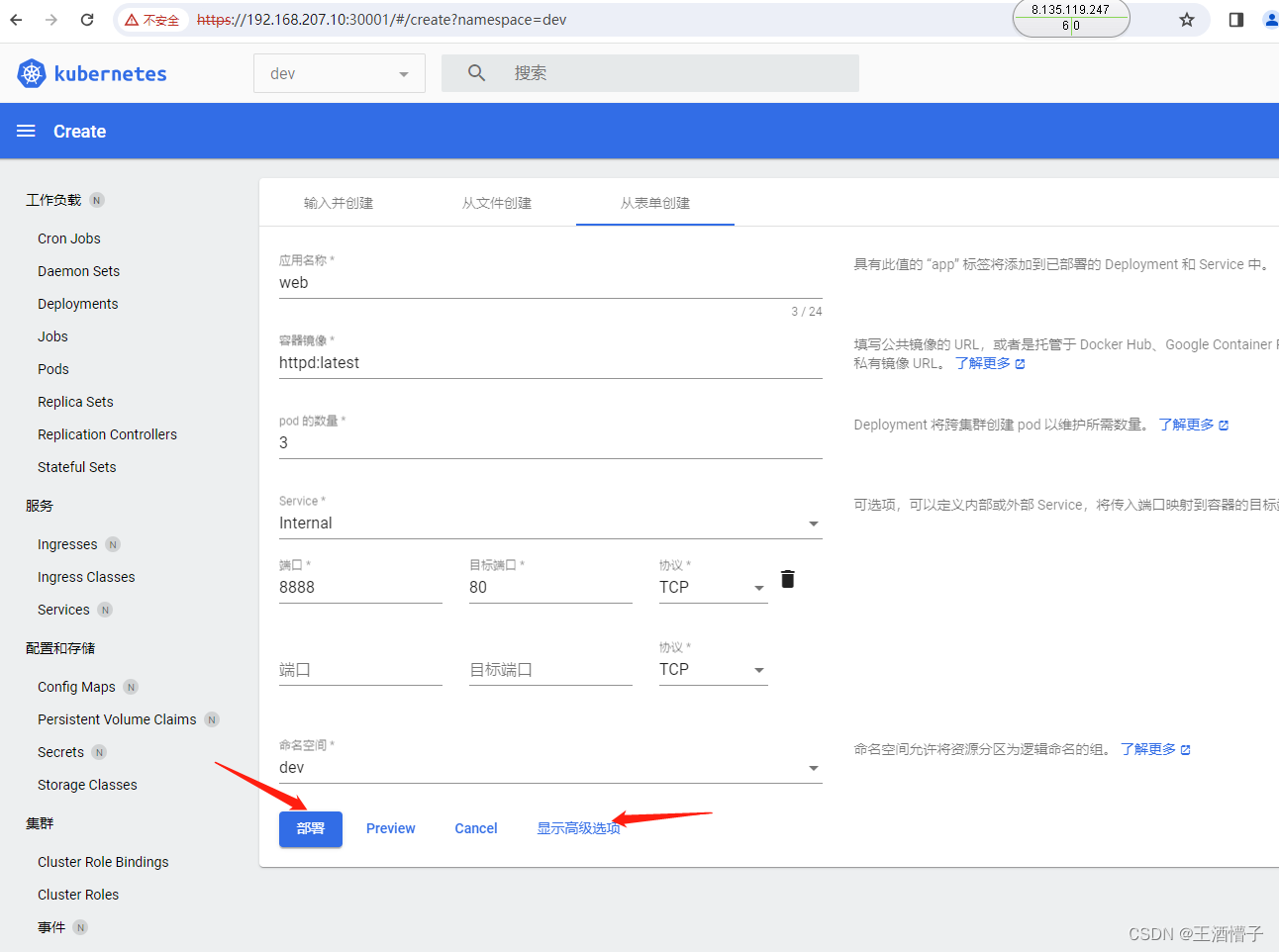
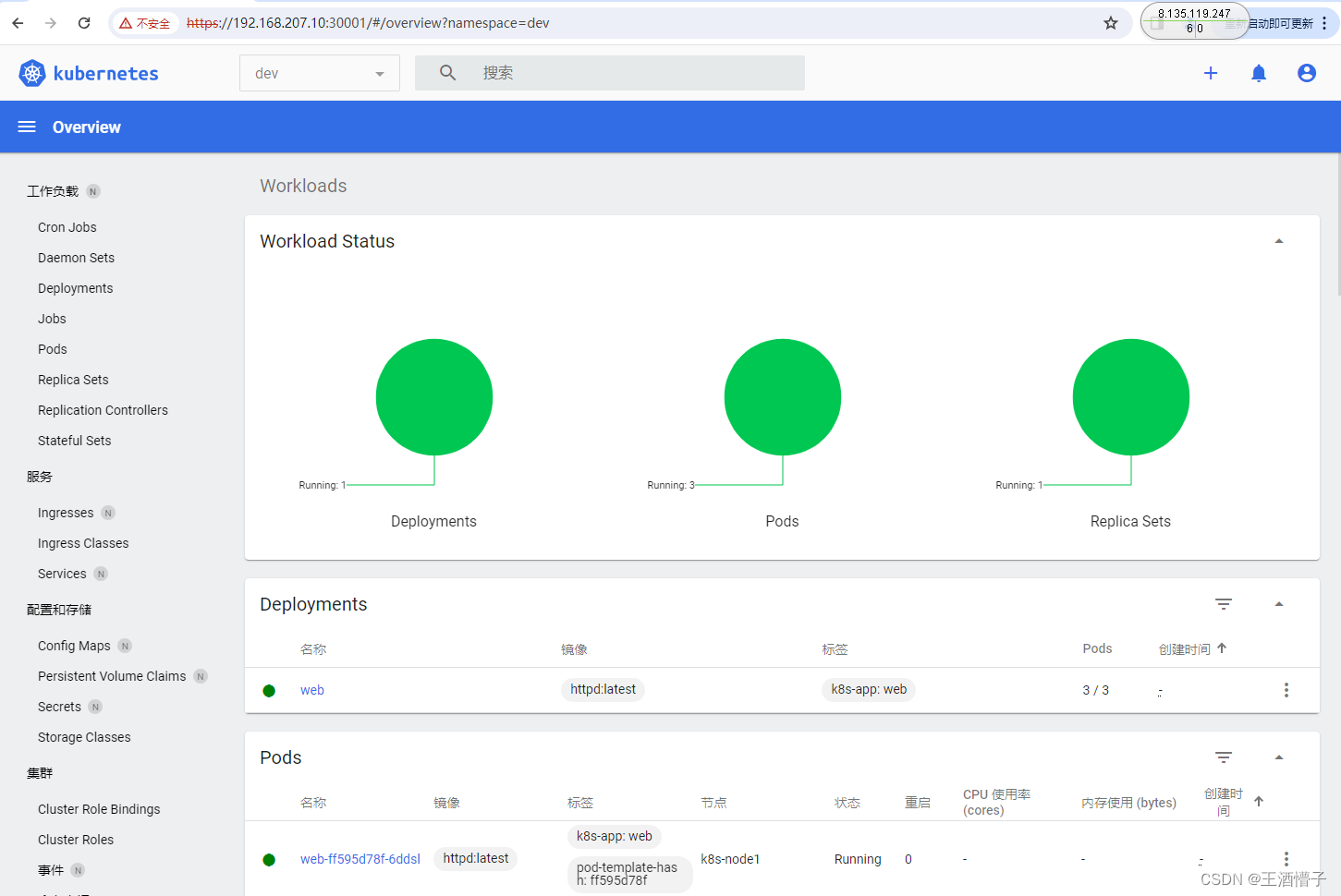
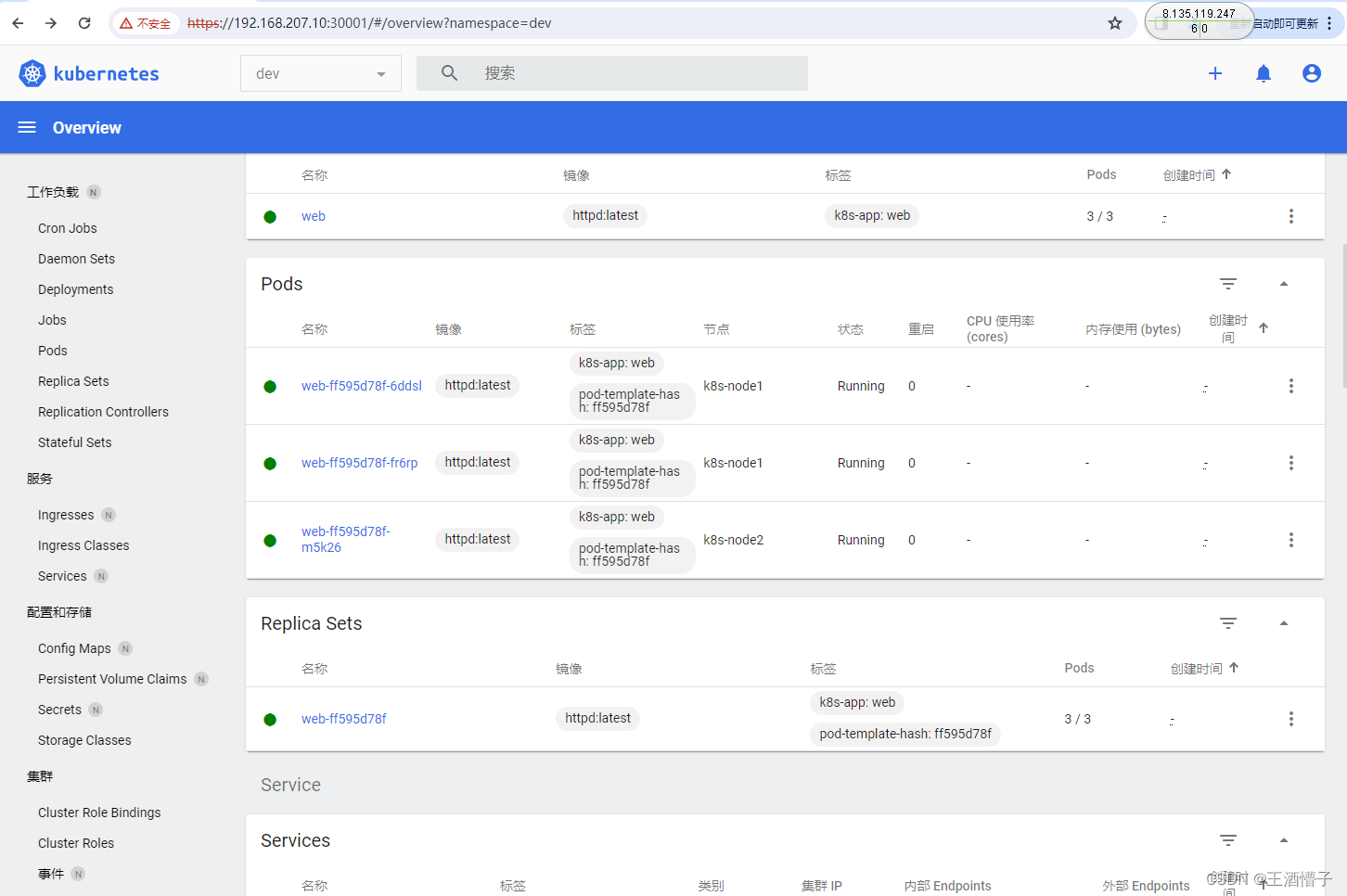
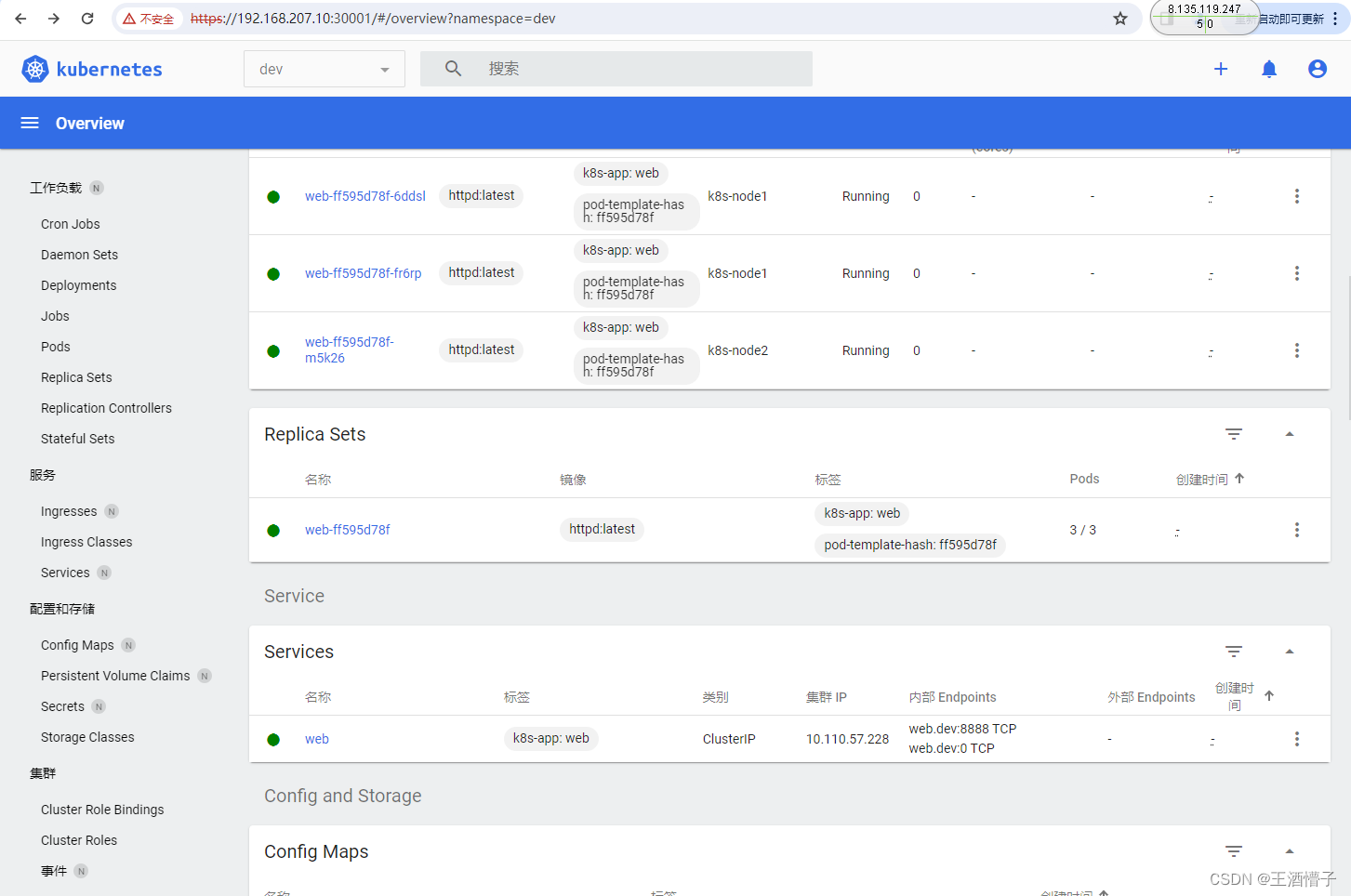
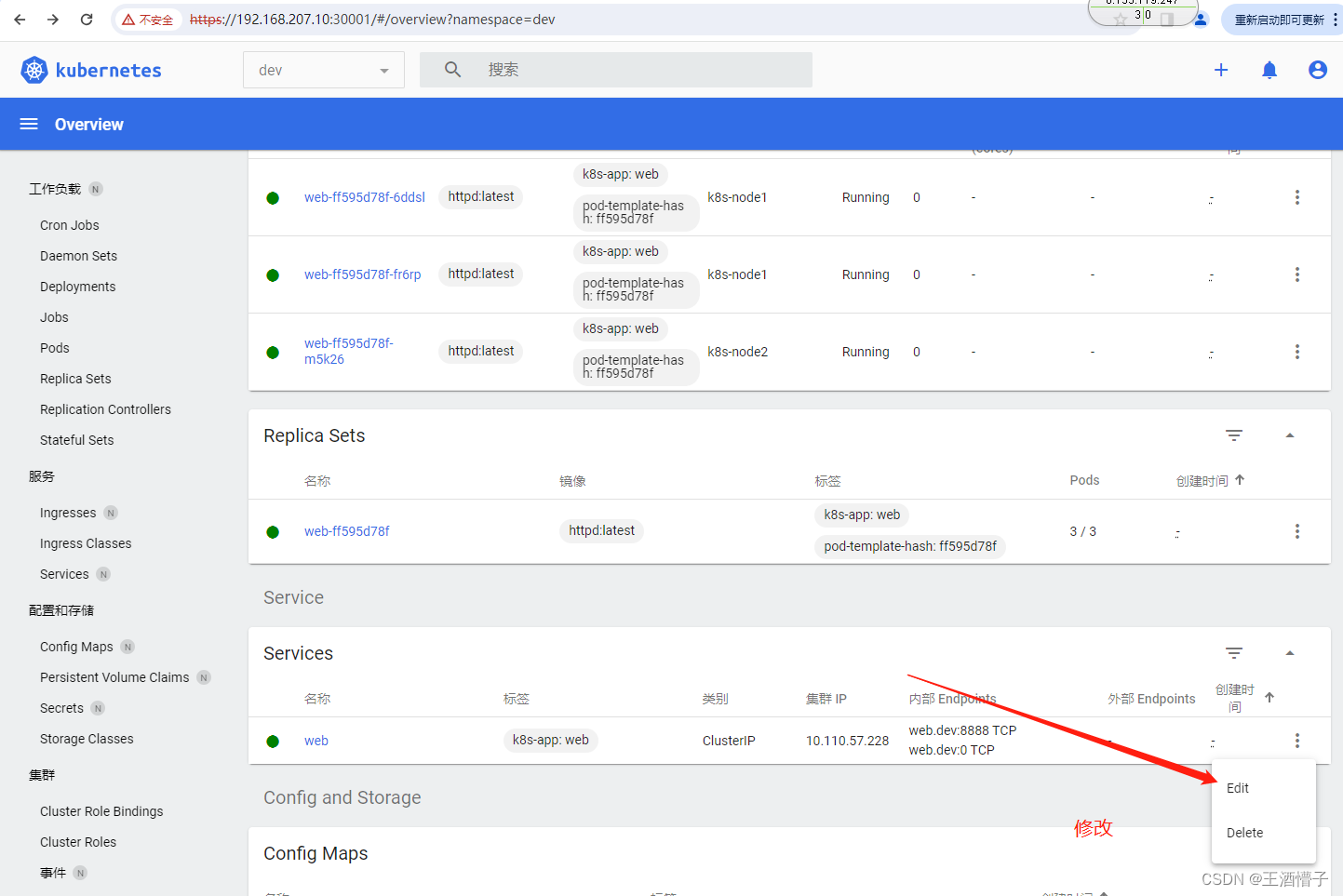
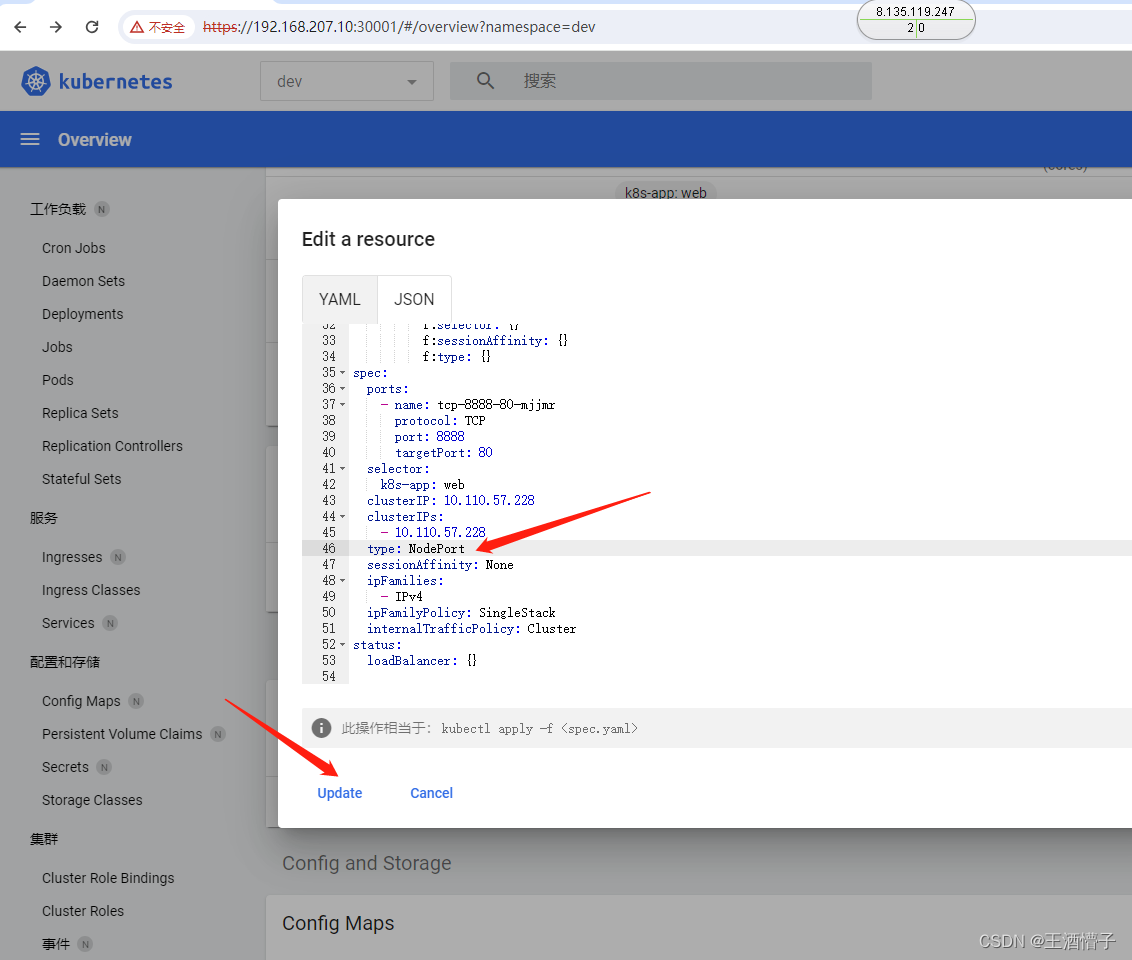
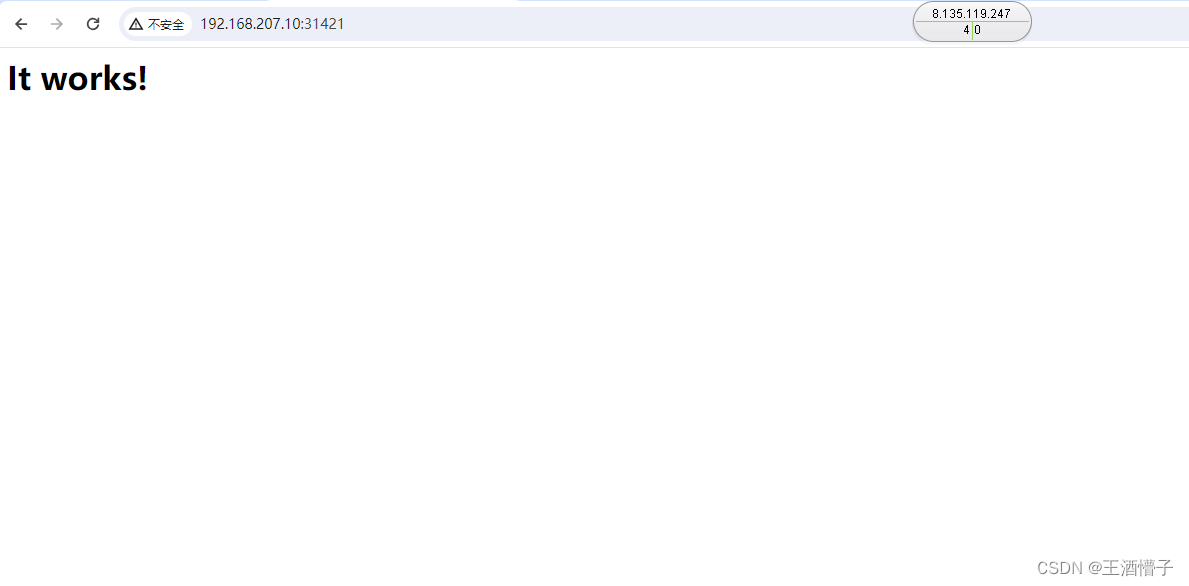
[root@k8s-master dashboard]# curl 10.110.57.228:8888
<html><body><h1>It works!</h1></body></html>
[root@k8s-master dashboard]# curl 10.110.57.228:8888
<html><body><h1>It works!</h1></body></html>
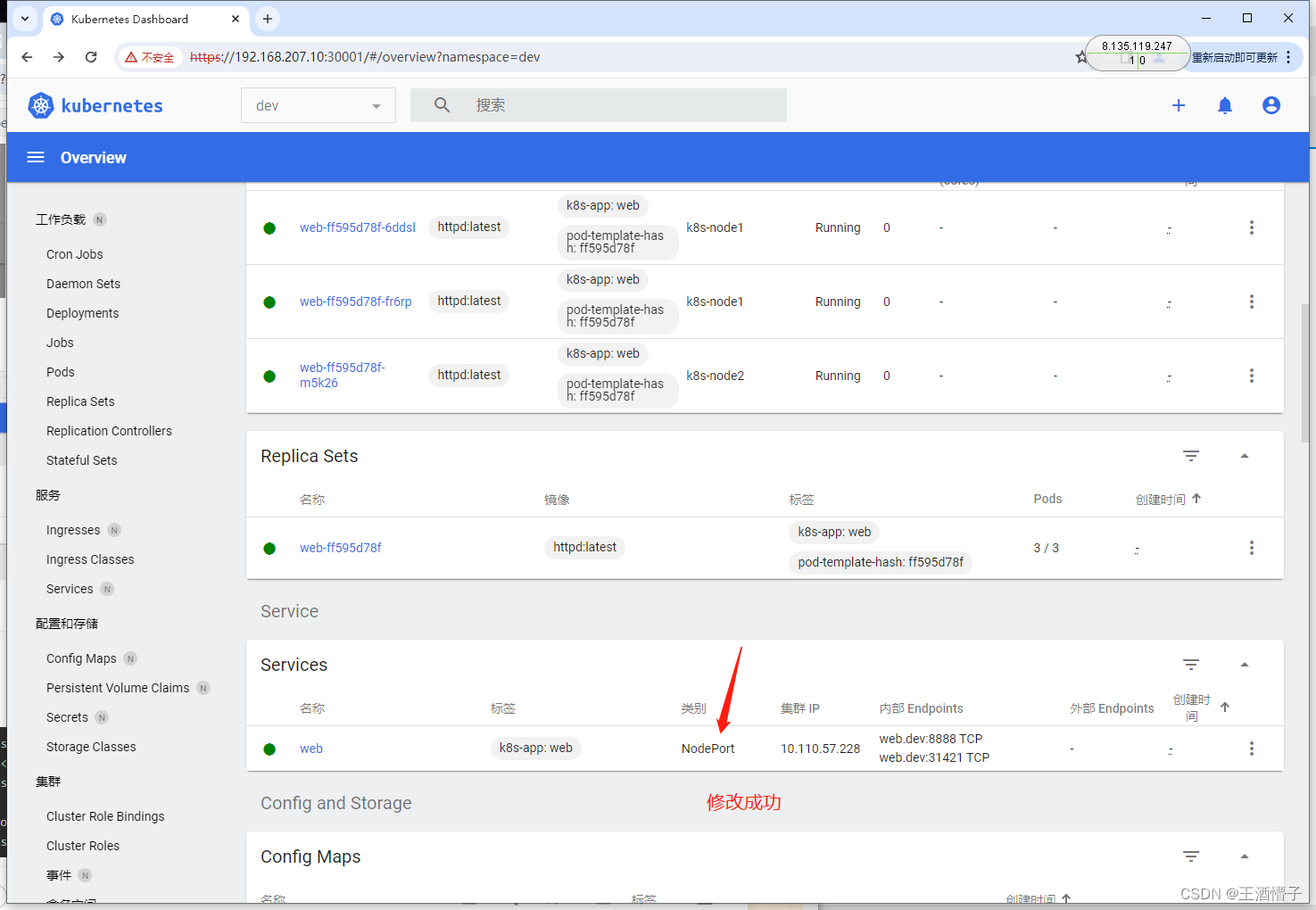
[root@k8s-master dashboard]# kubectl get svc -n dev
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
web NodePort 10.110.57.228 <none> 8888:31421/TCP 7m5s
文章来源:https://blog.csdn.net/whl0102222/article/details/135048825
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!