【网络安全】vulhub靶场搭建与一个漏洞的简单示例
2023-12-14 13:37:14
vulhub是一个经典的靶场,里面大约包含了200个不同的漏洞,可以说是安全从业者必刷。
无需docker知识,简单执行一条命令即可编译、运行一个完整的漏洞靶场镜像。
我的环境是CentOS 7。
先安装docker
sudo curl -L "https://github.com/docker/compose/releases/download/1.24.1/docker-compose-$(uname -s)-$(uname -m)" -o /usr/local/bin/docker-compose
sudo chmod +x /usr/local/bin/docker-compose
sudo ln -s /usr/local/bin/docker-compose /usr/bin/docker-compose
sudo ln -s /usr/local/bin/docker-compose /usr/bin/docker-compose
# 测试安装是否成功
docker-compose --version下载并解压vulhub
wget https://github.com/vulhub/vulhub/archive/master.zip -O vulhub-master.zip
unzip vulhub-master.zip开始漏洞复现,以nginx的路径穿越为例,先进入到目录
cd vulhub-master/nginx/insecure-configuration启动容器
docker-compose up -d但是我提示端口8081被占用了。?
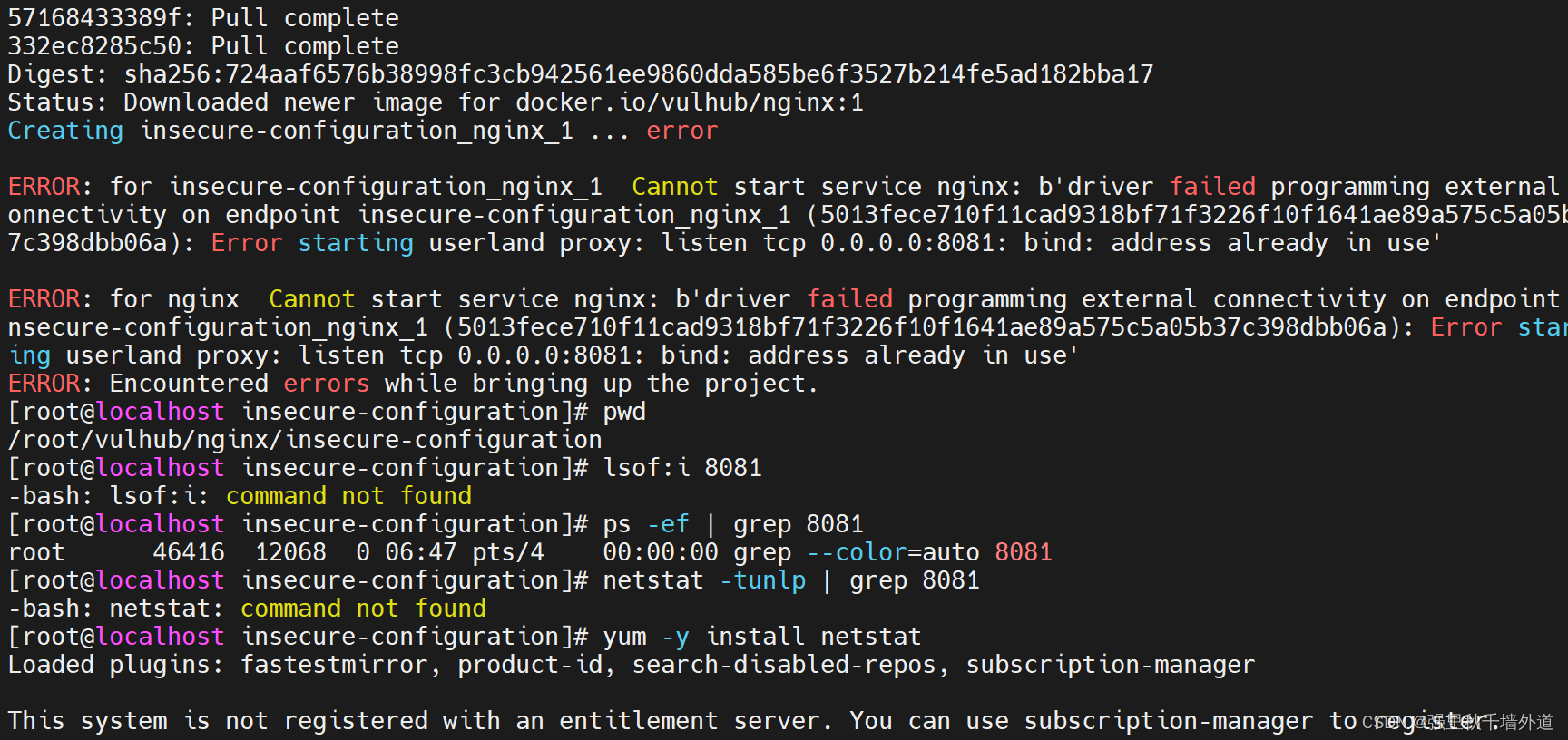
于是我通过命令lsof来查看被谁占用了,并且杀死了这个进程。
[root@localhost insecure-configuration]# lsof -i:8081
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
hfish-ser 1838 root 28u IPv6 21344 0t0 TCP *:tproxy (LISTEN)
[root@localhost insecure-configuration]# kill -9 1838
[root@localhost insecure-configuration]#
启动成功:
[root@localhost insecure-configuration]# docker-compose up -d
Starting insecure-configuration_nginx_1 ... done
[root@localhost insecure-configuration]#
接下来查看本机ip地址以供接下来在浏览器访问
[root@localhost insecure-configuration]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:f2:d6:95 brd ff:ff:ff:ff:ff:ff
inet 192.168.2.10/24 brd 192.168.2.255 scope global noprefixroute dynamic ens33
valid_lft 84107sec preferred_lft 84107sec
inet6 fe80::a466:2bb7:eb37:3777/64 scope link noprefixroute
valid_lft forever preferred_lft forever
3: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
link/ether 02:42:b3:7b:50:3d brd ff:ff:ff:ff:ff:ff
inet 172.17.0.1/16 scope global docker0
valid_lft forever preferred_lft forever
4: br-a3c74a0e1112: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:91:c1:67:e6 brd ff:ff:ff:ff:ff:ff
inet 172.18.0.1/16 scope global br-a3c74a0e1112
valid_lft forever preferred_lft forever
inet6 fe80::42:91ff:fec1:67e6/64 scope link
valid_lft forever preferred_lft forever
10: vethee69003@if9: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-a3c74a0e1112 state UP group default
link/ether 06:fc:b7:6d:cf:a1 brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet6 fe80::4fc:b7ff:fe6d:cfa1/64 scope link
valid_lft forever preferred_lft forever
[root@localhost insecure-configuration]#
文章来源:https://blog.csdn.net/weixin_39445116/article/details/134899384
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!