H3CIE面试项目
挂了挂了,不找借口了,我是个菜狗
这个是我讲的项目,分享出来仅供参考,暂时懒得整理文章排版,凑合着看吧
项目讲述
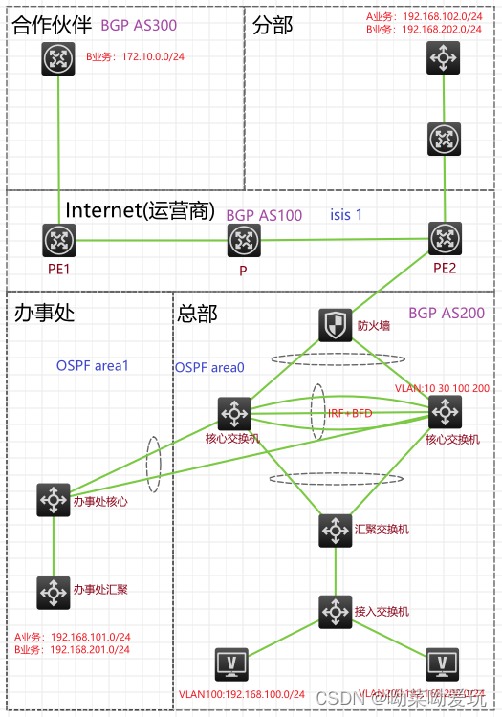
网络整体介绍
本次项目由5个区域构成,总部、办事处、Internet、分部、合作伙伴。
各区域存在两个业务,分为A业务、B业务。
总部地址规划(A业务:192.168.100.0/24、B业务:192.168.200.0/24)
办事处地址规划(A业务:192.168.101.0/24、B业务:192.168.201.0/24)
分部地址规划(A业务:192.168.102.0/24、B业务:192.168.202.0/24)
合作伙伴只知晓B业务(172.10.0.0/24)
整个网络只能总部的A业务能与分部、办事处互通,分部与办事处之间A业务不能互通。
总部和办事处只有A业务可以访问互联网,办事处访问互联网从公司总部出去。
合作伙伴只使用B业务访问我公司的B业务。
网络详细介绍
IRF
为了简化配置方便管理,总部的两台核心交换机做了IRF堆叠。
链路上,核心之间使用2组万兆光口和SFP+高速电缆交错相连,加强链路的可靠性。
检测机制上,使用BFD MAD方式检测堆叠分裂。在堆叠分裂的情况下,将从设备所有接口down掉,保障网络的正常通信。
VLAN
在堆叠好的核心交换机上有VLAN10 30 100 200,核心交换机与防火墙和办事处交换机通过三层Vlanif接口进行互联,VLAN10用于核心与防火墙互联,VLAN30用于核心与办事处互联,VLAN100是分部的A业务,VLAN200是分部的B业务
链路聚合 trunk
核心交换机与上行下行设备之间通过配置静态链路聚合来提高链路的总带宽和可靠性
核心交换机到SW4到SW5之间都是是TRUNK链路,只允许VLAN100 200通过
DHCP
总部的A业务是普通用户段,使用DHCP动态获取IP地址。并且在汇聚、接入上开启DHCP SNOOPING,将除了通向DHCP服务器的端口全划到untrust域,防止PC从其他违规接入DHCP服务器中获取到不合法的IP地址
ARP
总部的B业务是敏感用户段,通过手工配置IP地址,并且在核心上将配置静态ARP表项,实现IP地址和MAC地址的固定映射,并且将未使用IP绑定MAC地址0000.0000.0000,防止非法用户私自配置使用
OSPF
总部和办事处之间使用OSPF获取路由,总部在区域0里、分部在区域1里。
防火墙通过配置默认路由访问Internet,并且在OSPF中下发默认路由,使得总部的设备都能够通过默认路由访问外部网络。
办事处使用了低端交换机,接受不了大量路由信息,所以将OSPF区域设置为STUB区域,减少外部路由的注入。
为加快OSPF的收敛,将总部和办事处设备的互联链路全部修改为P2P网络类型。
并且在总部汇聚交换机上配置静默端口,使业务VLAN中不能收到OSPF协议报文。
NAT
在防火墙使用"Easy_ip+ACL"的方式访问外网,ACL只允许总部和办事处各自的A业务通过,并在出方向调用ACL,只让总部和办事处的A业务通过NAT转换能够正常上网
ISIS
Internet区域由运营商维护。使用承载能力强,收敛速度快的ISIS获取路由。
BGP
总部、运营商、合作伙伴分为三个AS,AS之间使用BGP传输路由
运营商内部,通过“ISIS+IBGP”的方式,使用环回口建立BGP邻居
运营商与总部之间、运营商与合作伙伴之间通过“静态路由+EBGP”的方式,使用物理口建立BGP邻居
GRE over IPSEC
在总部与分部之间使用GRE over IPSEC VPN,并且通过感兴趣流匹配,保护各自的A业务可以互通
MPLS
运营商之间使用MPLS生成LSP,便于后续PE设备之间使用BGP传递私网路由
VRF
在运营商PE上将与总部、合作伙伴接口加进相同的VPN实例中。
并且在PE9上,将VPN实例和公共实例中将直连路由相互复制,实现VPN实例和公共实例的路由互通
BGP MPLS VPN
在总部与合作伙伴公司使用BGP/MPLS VPN保证私网业务的正常通信
ACL只允许总部的B业务通过,并使用filter-policy在BGP的出方向进行过滤,只让合作伙伴能收到总部B业务的路由
配置
IRF
Core_SW2
irf domain 100
irf member 1 priority 32
interface range Ten-GigabitEthernet1/0/51 Ten-GigabitEthernet1/0/52
shutdown
irf-port 1/1
port group interface Ten-GigabitEthernet1/0/51
irf-port 1/2
port group interface Ten-GigabitEthernet1/0/52
interface range Ten-GigabitEthernet1/0/51 Ten-GigabitEthernet1/0/52
undo shutdown
irf-port-configuration active
Core_SW3
irf member 1 renumber 2
reboot
irf domain 100
interface range Ten-GigabitEthernet2/0/51 Ten-GigabitEthernet2/0/52
shutdown
irf-port 2/1
port group interface Ten-GigabitEthernet2/0/51
irf-port 2/2
port group interface Ten-GigabitEthernet2/0/52
interface range Ten-GigabitEthernet2/0/51 Ten-GigabitEthernet2/0/52
undo shutdown
save f
irf-port-configuration active
IRF_BDF MAD
Core_SW
vlan 250
interface Vlan-interface250
mad bfd enable
mad ip address 192.168.250.1 24 member 1
mad ip address 192.168.250.2 24 member 2
interface range GigabitEthernet1/0/48 GigabitEthernet2/0/48
port access vlan 250
undo stp enable
VLAN
Core_SW
vlan 10 30 100 200
SW4
vlan 100 200
SW5
vlan 100 200
SW6
vlan 30 40
SW7
VLAN 40
SW8
VLAN 50
链路聚合
Core_SW
interface Bridge-Aggregation10
interface Bridge-Aggregation20
interface Bridge-Aggregation30
interface range GigabitEthernet1/0/1 GigabitEthernet2/0/1
port link-aggregation group 10
interface range GigabitEthernet1/0/2 GigabitEthernet2/0/2
port link-aggregation group 20
interface range GigabitEthernet1/0/3 GigabitEthernet2/0/3
port link-aggregation group 30
FW1
interface Route-Aggregation 10
interface range GigabitEthernet1/0/2 GigabitEthernet1/0/3
port link-aggregation group 10
SW4
interface Bridge-Aggregation20
interface range GigabitEthernet1/0/1 GigabitEthernet1/0/2
port link-aggregation group 20
SW6
interface Bridge-Aggregation30
interface range GigabitEthernet1/0/1 GigabitEthernet1/0/2
port link-aggregation group 30
TRUNK
Core_SW
interface Bridge-Aggregation20
port link-type trunk
port trunk permit vlan 100 200
SW4
interface Bridge-Aggregation20
port link-type trunk
port trunk permit vlan 100 200
interface GigabitEthernet1/0/3
port link-type trunk
port trunk permit vlan 100 200
SW5
interface GigabitEthernet1/0/3
port link-type trunk
port trunk permit vlan 100 200
IP
Core_SW
interface Vlan-interface10
ip address 192.168.10.1 30
interface Vlan-interface30
ip address 192.168.30.1 30
interface Vlan-interface100
ip address 192.168.100.1 255.255.255.0
interface Vlan-interface200
ip address 192.168.200.1 255.255.255.0
interface LoopBack0
ip address 1.0.0.23 255.255.255.255
interface Bridge-Aggregation10
port access vlan 10
interface Bridge-Aggregation30
port access vlan 30
FW1
interface Route-Aggregation10
ip address 192.168.10.2 30
interface GigabitEthernet1/0/0
ip address 10.1.1.1 30
interface LoopBack0
ip address 1.0.0.1 255.255.255.255
SW6
interface Vlan-interface30
ip address 192.168.30.2 30
interface Vlan-interface40
ip address 192.168.40.1 30
interface LoopBack0
ip address 1.0.0.6 255.255.255.255
interface Bridge-Aggregation30
port access vlan 30
interface GigabitEthernet1/0/3
port access vlan 40
SW7
interface Vlan-interface40
ip address 192.168.40.2 30
interface LoopBack0
ip address 1.0.0.7 255.255.255.255
interface LoopBack101
ip address 192.168.101.1 24
interface LoopBack201
ip address 192.168.201.1 24
interface GigabitEthernet1/0/3
port access vlan 40
SW8
interface Vlan-interface30
ip address 192.168.50.2 30
interface LoopBack0
ip address 1.0.0.8 255.255.255.255
interface LoopBack102
ip address 192.168.102.1 24
interface LoopBack202
ip address 192.168.202.1 24
PE9
interface GigabitEthernet0/0/0
ip address 10.1.1.2 30
interface GigabitEthernet0/0/1
ip address 100.1.1.1 30
interface GigabitEthernet0/0/2
ip address 10.1.2.1 30
interface LoopBack0
ip address 1.0.0.9 255.255.255.255
P10
interface GigabitEthernet0/0/1
ip address 100.1.1.2 30
interface GigabitEthernet0/0/2
ip address 100.1.2.1 30
interface LoopBack0
ip address 1.0.0.10 255.255.255.255
PE11
interface GigabitEthernet0/0/0
ip address 10.1.3.1 30
interface GigabitEthernet0/0/2
ip address 100.1.2.2 30
interface LoopBack0
ip address 1.0.0.11 255.255.255.255
R12
interface GigabitEthernet0/0/1
ip address 192.168.50.1 30
interface GigabitEthernet0/0/2
ip address 10.1.2.2 30
interface LoopBack0
ip address 1.0.0.12 255.255.255.255
P13
interface GigabitEthernet0/0/0
ip address 10.1.3.2 30
interface LoopBack0
ip address 1.0.0.13 255.255.255.255
interface LoopBack172
ip address 172.10.0.1 24
FW策略
FW1
security-zone name Trust
import interface GigabitEthernet1/0/0
import interface Route-Aggregation10
security-policy ip
rule 1 name t2l
action pass
source-zone Trust
source-zone local
destination-zone Trust
destination-zone local
DHCP
Core_SW
dhcp enable
dhcp server ip-pool vlan100
gateway-list 192.168.100.1
network 192.168.100.0 mask 255.255.255.0
address range 192.168.100.10 192.168.100.200
dns-list 114.114.114.114
interface Vlan-interface100
dhcp server apply ip-pool vlan100
SW5
interface GigabitEthernet1/0/1
port access vlan 100
interface GigabitEthernet1/0/2
port access vlan 200
DHCP_SNOOPING
SW4
dhcp snooping enable
interface Bridge-Aggregation20
dhcp snooping trust
SW5
dhcp snooping enable
interface GigabitEthernet1/0/3
dhcp snooping trust
OSPF
Core_SW
ospf 1
area 0.0.0.0
network 192.168.10.0 0.0.0.255
network 192.168.30.0 0.0.0.255
network 192.168.100.0 0.0.0.255
network 192.168.200.0 0.0.0.255
FW1
ospf 1
default-route-advertise
area 0.0.0.0
network 192.168.10.0 0.0.0.255
SW6
ospf 1
area 0.0.0.0
network 192.168.30.0 0.0.0.255
ospf 1
area 0.0.0.1
network 192.168.40.0 0.0.0.255
stub
SW7
ospf 1
area 0.0.0.1
network 192.168.40.0 0.0.0.255
stub
分部OSPF
#SW7
ospf 1
area 0.0.0.2
network 192.168.50.0 0.0.0.255
network 192.168.102.0 0.0.0.255
network 192.168.202.0 0.0.0.255
interface Vlan-interface50
ip address 192.168.50.2 255.255.255.252
interface GigabitEthernet1/0/1
port access vlan 50
#R12
ospf 1
default-route-advertise
area 0.0.0.2
network 192.168.50.0 0.0.0.255
GRE over IPsec VPN
FW1
ip route-static 0.0.0.0 0 10.1.1.2
acl advanced 3000
rule 0 permit ip source 1.0.0.1 0 destination 1.0.0.12 0
rule 5 permit ip source 192.168.100.0 0.0.0.255 destination 192.168.102.0 0.0.0.255
ike keychain 1
pre-shared-key address 10.1.2.2 key simple 123
ike profile 1
keychain 1
match remote identity address 10.1.2.2 255.255.255.255
ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
ipsec policy-template tem 1
transform-set 1
ike-profile 1
ipsec policy h3c 1 isakmp template tem
interface GigabitEthernet1/0/0
ipsec apply policy h3c
#######
interface Tunnel0 mode gre
ip address 180.0.0.1 255.255.255.0
source LoopBack0
destination 1.0.0.12
R12
ip route-static 0.0.0.0 0 10.1.2.1
acl advanced 3000
rule 0 permit ip source 1.0.0.12 0 destination 1.0.0.1 0
rule 5 permit ip source 192.168.102.0 0.0.0.255 destination 192.168.100.0 0.0.0.255
ike keychain 1
pre-shared-key address 10.1.1.1 key simple 123
ike profile 1
keychain 1
match remote identity address 10.1.1.1 255.255.255.255
ipsec transform-set 1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
ipsec policy h3c 1 isakmp
ike-profile 1
transform-set 1
security acl 3000
remote-address 10.1.1.1
interface GigabitEthernet0/0/2
ipsec apply policy h3c
#######
interface Tunnel0 mode gre
ip address 180.0.0.2 255.255.255.0
source LoopBack0
destination 1.0.0.1
isis
PE9
isis 1
network-entity 49.0000.0000.0000.0001.00
is-level level-1
interface GigabitEthernet0/0/1
isis enable 1
interface LoopBack0
isis enable 1
P10
isis 1
network-entity 49.0000.0000.0000.0002.00
is-level level-1
interface GigabitEthernet0/0/1
isis enable 1
interface GigabitEthernet0/0/2
isis enable 1
interface LoopBack0
isis enable 1
PE11
isis 1
network-entity 49.0000.0000.0000.0003.00
is-level level-1
interface GigabitEthernet0/0/2
isis enable 1
interface LoopBack0
isis enable 1
MPLS ldp
PE9
mpls lsr-id 1.0.0.9
mpls ldp
interface GigabitEthernet0/0/1
mpls enable
mpls ldp enable
P10
mpls lsr-id 1.0.0.10
mpls ldp
interface GigabitEthernet0/0/1
mpls enable
mpls ldp enable
interface GigabitEthernet0/0/2
mpls enable
mpls ldp enable
PE11
mpls lsr-id 1.0.0.11
mpls ldp
interface GigabitEthernet0/0/2
mpls enable
mpls ldp enable
VRF
PE9
ip vpn-instance h3c
route-distinguisher 1:1
vpn-target 1:1 import-extcommunity
vpn-target 1:1 export-extcommunity
interface GigabitEthernet0/0/0
ip binding vpn-instance h3c
ip address 10.1.1.2 255.255.255.252
PE11
ip vpn-instance h3c
route-distinguisher 1:1
vpn-target 1:1 import-extcommunity
vpn-target 1:1 export-extcommunity
interface GigabitEthernet0/0/0
ip binding vpn-instance h3c
ip address 10.1.3.1 255.255.255.252
MP-IBGP
PE9
bgp 100
router-id 1.0.0.9
peer 1.0.0.10 as-number 100
peer 1.0.0.10 connect-interface LoopBack0
peer 1.0.0.11 as-number 100
peer 1.0.0.11 connect-interface LoopBack0
address-family vpnv4 unicast
peer 1.0.0.10 enable
peer 1.0.0.11 enable
P10
bgp 100
router-id 1.0.0.10
peer 1.0.0.9 as-number 100
peer 1.0.0.9 connect-interface LoopBack0
peer 1.0.0.11 as-number 100
peer 1.0.0.11 connect-interface LoopBack0
address-family vpnv4 unicast
peer 1.0.0.9 enable
peer 1.0.0.11 enable
PE11
bgp 100
router-id 1.0.0.11
peer 1.0.0.9 as-number 100
peer 1.0.0.9 connect-interface LoopBack0
peer 1.0.0.10 as-number 100
peer 1.0.0.10 connect-interface LoopBack0
address-family vpnv4 unicast
peer 1.0.0.9 enable
peer 1.0.0.10 enable
MP-EBGP
PE9
bgp 100
ip vpn-instance h3c
peer 10.1.1.1 as-number 200
address-family ipv4 unicast
import-route direct
peer 10.1.1.1 enable
PE11
bgp 100
ip vpn-instance h3c
peer 10.1.3.2 as-number 300
address-family ipv4 unicast
import-route direct
peer 10.1.3.2 enable
FW1
bgp 200
peer 10.1.1.2 as-number 100
address-family ipv4 unicast
import-route direct
peer 10.1.1.2 enable
R13
bgp 300
peer 10.1.3.1 as-number 100
address-family ipv4 unicast
import-route direct
peer 10.1.3.1 enable
BGP引入
FW1
bgp 200
address-family ipv4 unicast
import-route ospf 1
ospf
import-route bgp
VRF public
通过路由复制实现Public与VRF路由互通
PE9
ip vpn-instance h3c
address-family ipv4
route-replicate from public protocol direct //可以实现将Public的直连路由引入到VRF test里
ip public-instance
address-family ipv4
route-replicate from vpn-instance h3c protocol direct //可以实现将VRF test的直连路由引入到Public路由表里
路由过滤
FW1
acl basic 2100
rule 0 permit source 192.168.200.0 0.0.0.255
bgp 200
address-family ipv4 unicast
filter-policy 2100 export
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!