Tekton 基于 gitlab 触发流水线
Tekton 基于 gitlab 触发流水线
Tekton EventListener 在8080端口监听事件,Gitlab 提交代码产生push 事件,gitlab webhook触发tekton流水线执行。
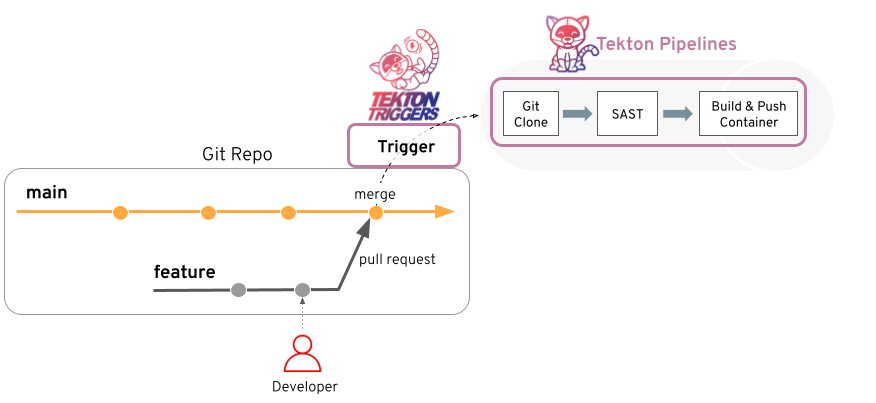
前置要求:
- kubernetes集群中已部署
tekton pipeline、tekton triggers以及tekton dashboard三个组件; - 本示例使用LoadBalancer 暴露 EventListener service,集群中有可用负载均衡器分配IP地址。
创建serviceaccount
官方示例:https://github.com/tektoncd/triggers/blob/main/examples/rbac.yaml
因为 EventListener 最终需要创建 taskrun、pipelinerun 同时会查询一些其他信息,因此需要为其配置一个 serviceAccount,同时还需要为这个 serviceAccount 赋予相应的权限。
$ cat serviceAccount.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: tekton-triggers-example-sa
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: triggers-example-eventlistener-binding
subjects:
- kind: ServiceAccount
name: tekton-triggers-example-sa
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: tekton-triggers-eventlistener-roles
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: triggers-example-eventlistener-clusterbinding
subjects:
- kind: ServiceAccount
name: tekton-triggers-example-sa
namespace: default
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: tekton-triggers-eventlistener-clusterroles
应用yaml
kubectl apply -f serviceAccount.yaml
创建EventListener
EventListener 是一个 Kubernetes 对象,用于侦听 Kubernetes 集群上指定端口上的事件。它公开了一个可寻址接收器,用于接收传入事件并指定一个或多个 Triggers 。
$ cat eventListener.yaml
apiVersion: triggers.tekton.dev/v1beta1
kind: EventListener
metadata:
name: gitlab-pr
spec:
serviceAccountName: tekton-triggers-example-sa
resources:
kubernetesResource:
serviceType: LoadBalancer
triggers:
- name: pr-trigger
bindings:
- ref: gitlab-pr-trigger-binding
template:
ref: gitlab-pr-trigger-template
应用yaml
kubectl apply -f eventListener.yaml
创建TriggerBinding
TriggerBinding 允许您从事件负载中提取字段并将它们绑定到命名参数,然后可以在 TriggerTemplate 中使用这些命名参数。
$ cat triggerBinding.yaml
apiVersion: triggers.tekton.dev/v1beta1
kind: TriggerBinding
metadata:
name: gitlab-pr-trigger-binding
spec:
params:
- name: message
value: hello
应用yaml
kubectl apply -f triggerBinding.yaml
创建TriggerTemplate
TriggerTemplate 是指定资源蓝图的资源,例如 TaskRun 或 PipelineRun ,当您的EventListener 检测到事件。它公开了您可以在资源模板中的任何位置使用的参数。
以下示例通过pipelineSpec和taskSpec直接引入task并运行:
$ cat triggerTemplate.yaml
apiVersion: triggers.tekton.dev/v1beta1
kind: TriggerTemplate
metadata:
name: gitlab-pr-trigger-template
spec:
params:
- name: message
default: hello
resourcetemplates:
- apiVersion: tekton.dev/v1beta1
kind: PipelineRun
metadata:
generateName: hello-
spec:
params:
- name: message
value: $(tt.params.message)
pipelineSpec:
tasks:
- name: hello-message
taskSpec:
steps:
- name: run-hello
image: alpine
script: |
echo $(params.message)
应用yaml
kubectl apply -f triggerTemplate.yaml
完整示例
$ cat githlab_trigger.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: tekton-triggers-example-sa
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: triggers-example-eventlistener-binding
subjects:
- kind: ServiceAccount
name: tekton-triggers-example-sa
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: tekton-triggers-eventlistener-roles
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: triggers-example-eventlistener-clusterbinding
subjects:
- kind: ServiceAccount
name: tekton-triggers-example-sa
namespace: default
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: tekton-triggers-eventlistener-clusterroles
---
apiVersion: triggers.tekton.dev/v1beta1
kind: EventListener
metadata:
name: gitlab-pr
spec:
serviceAccountName: tekton-triggers-example-sa
resources:
kubernetesResource:
serviceType: LoadBalancer
triggers:
- name: pr-trigger
bindings:
- ref: gitlab-pr-trigger-binding
template:
ref: gitlab-pr-trigger-template
---
apiVersion: triggers.tekton.dev/v1beta1
kind: TriggerBinding
metadata:
name: gitlab-pr-trigger-binding
spec:
params:
- name: message
value: hello
---
apiVersion: triggers.tekton.dev/v1beta1
kind: TriggerTemplate
metadata:
name: gitlab-pr-trigger-template
spec:
params:
- name: message
default: hello
resourcetemplates:
- apiVersion: tekton.dev/v1beta1
kind: PipelineRun
metadata:
generateName: hello-
spec:
params:
- name: message
value: $(tt.params.message)
pipelineSpec:
tasks:
- name: hello-message
taskSpec:
steps:
- name: run-hello
image: alpine
script: |
echo $(params.message)
应用以上配置
kubectl apply -f githlab_trigger.yaml
配置gitlab webhook
查看EventListener service 监听地址和端口
root@kube001:~# kubectl get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
el-gitlab-pr LoadBalancer 10.96.0.235 192.168.72.224 8080:31293/TCP,9000:30628/TCP 8m7s
EventListener service 使用LoadBalancer 方式暴露到集群外,访问地址为:
http://192.168.72.224:8080
访问gitlab管理界面,新建demo项目,在项目Settings---> Webhooks中配置 EventListener 监听地址:
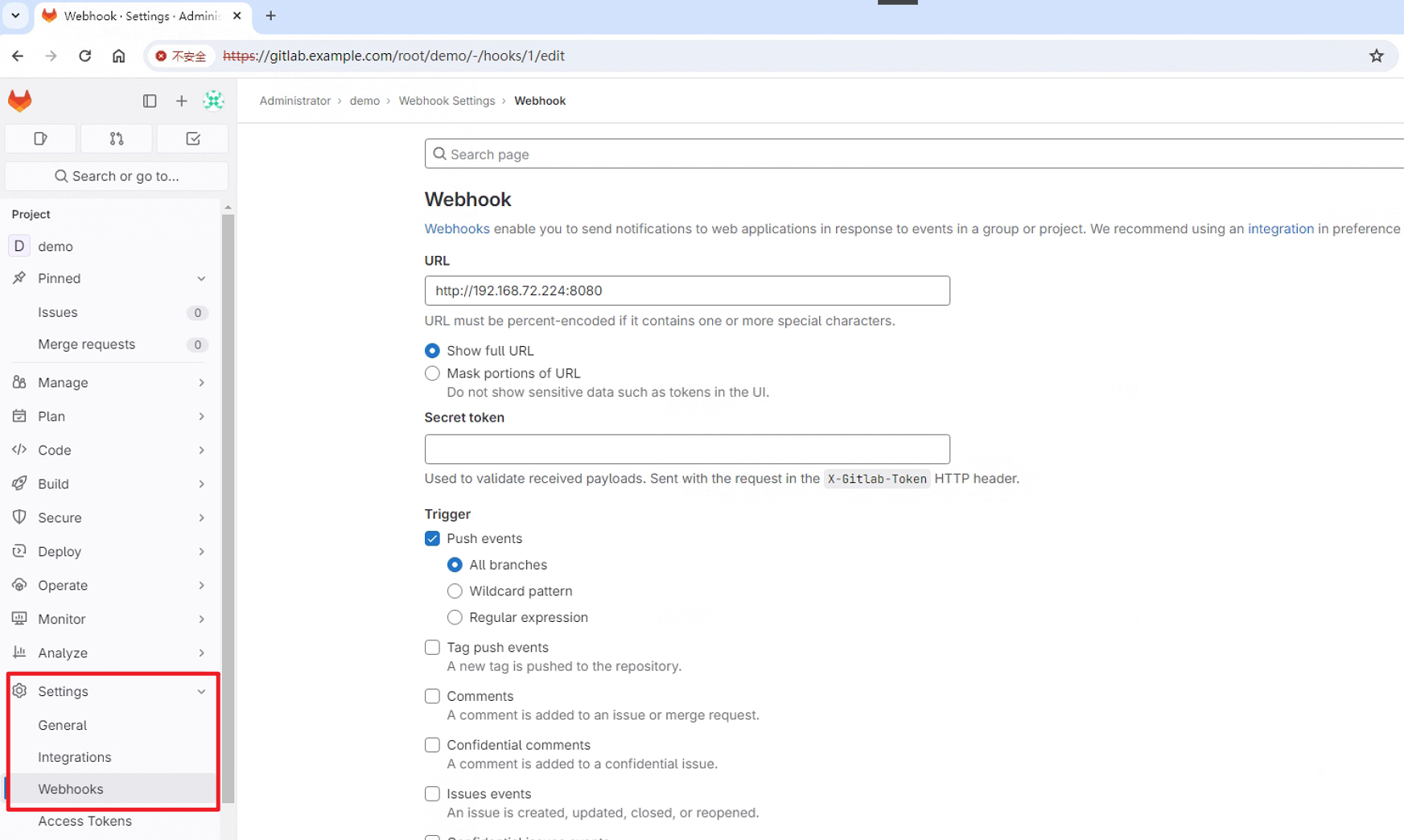
点击Push events进行测试,或者推送代码到gitlab项目仓库
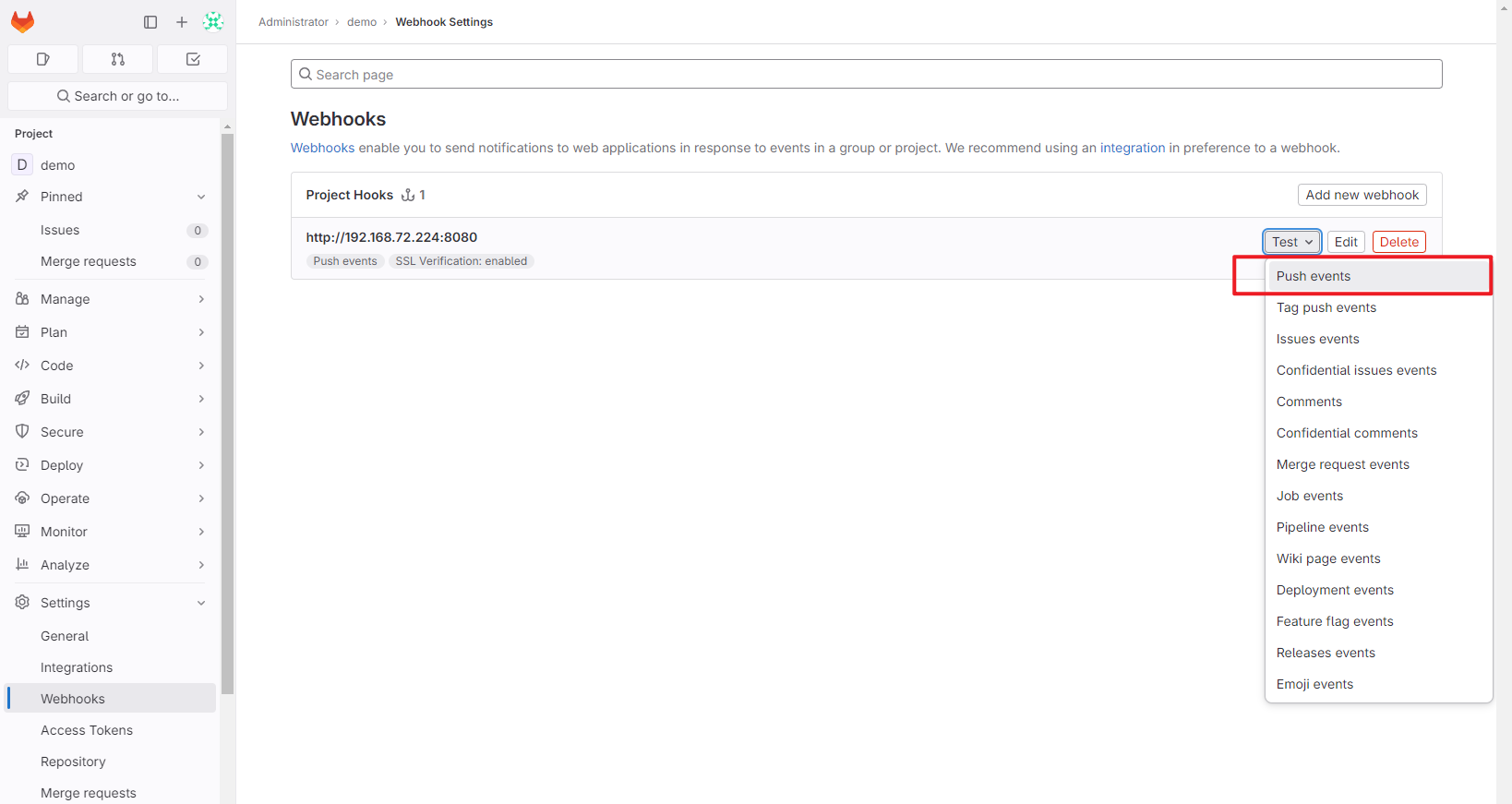
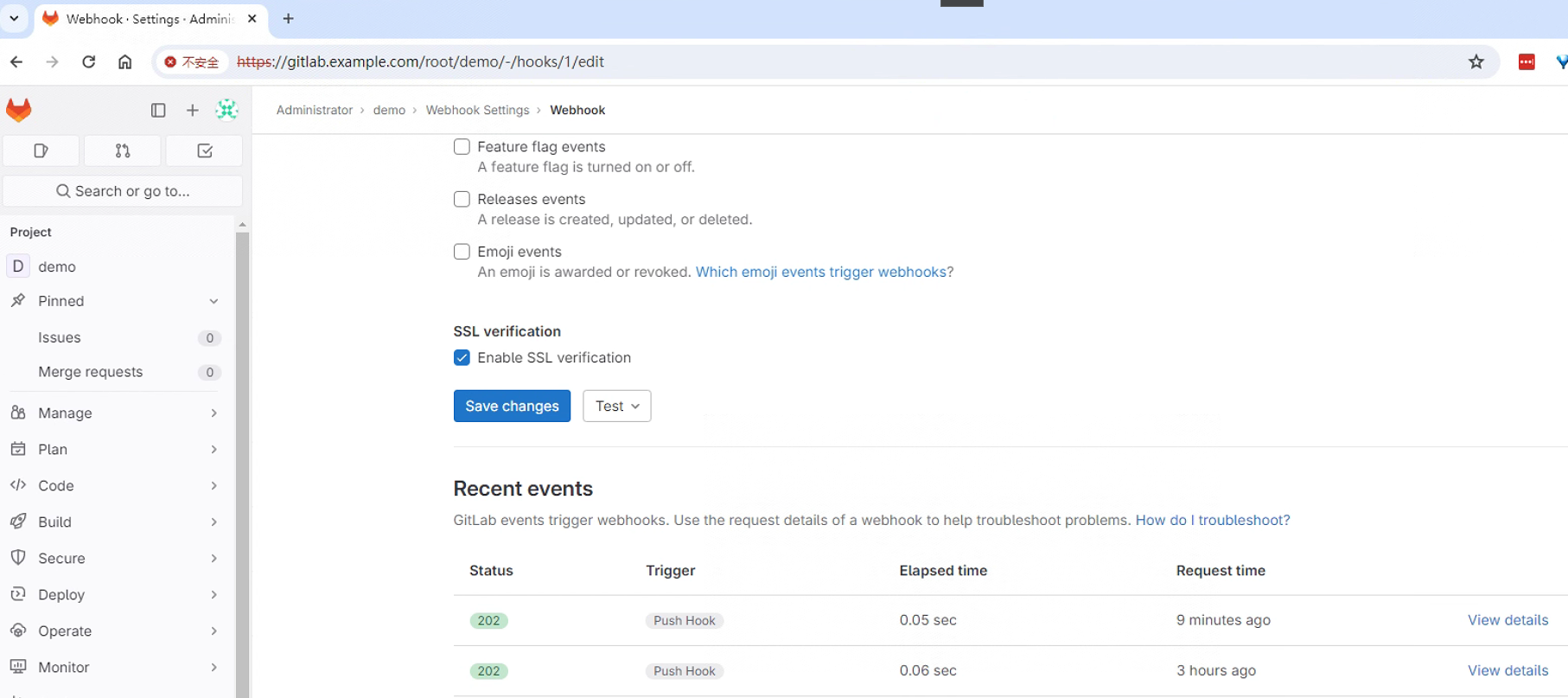
点击Edit查看测试结果
查看触发的pipeline任务
root@kube001:~# kubectl get pipelineruns | grep hello
hello-vrrs2 True Succeeded 4m42s 4m34s
查看运行完成的pods
root@kube001:~# kubectl get pods
NAME READY STATUS RESTARTS AGE
el-gitlab-pr-5f5749d48f-rqmlb 1/1 Running 0 12m
hello-vrrs2-hello-message-pod 0/1 Completed 0 5m49s
访问dashboard查看自动执行的pipelinerun
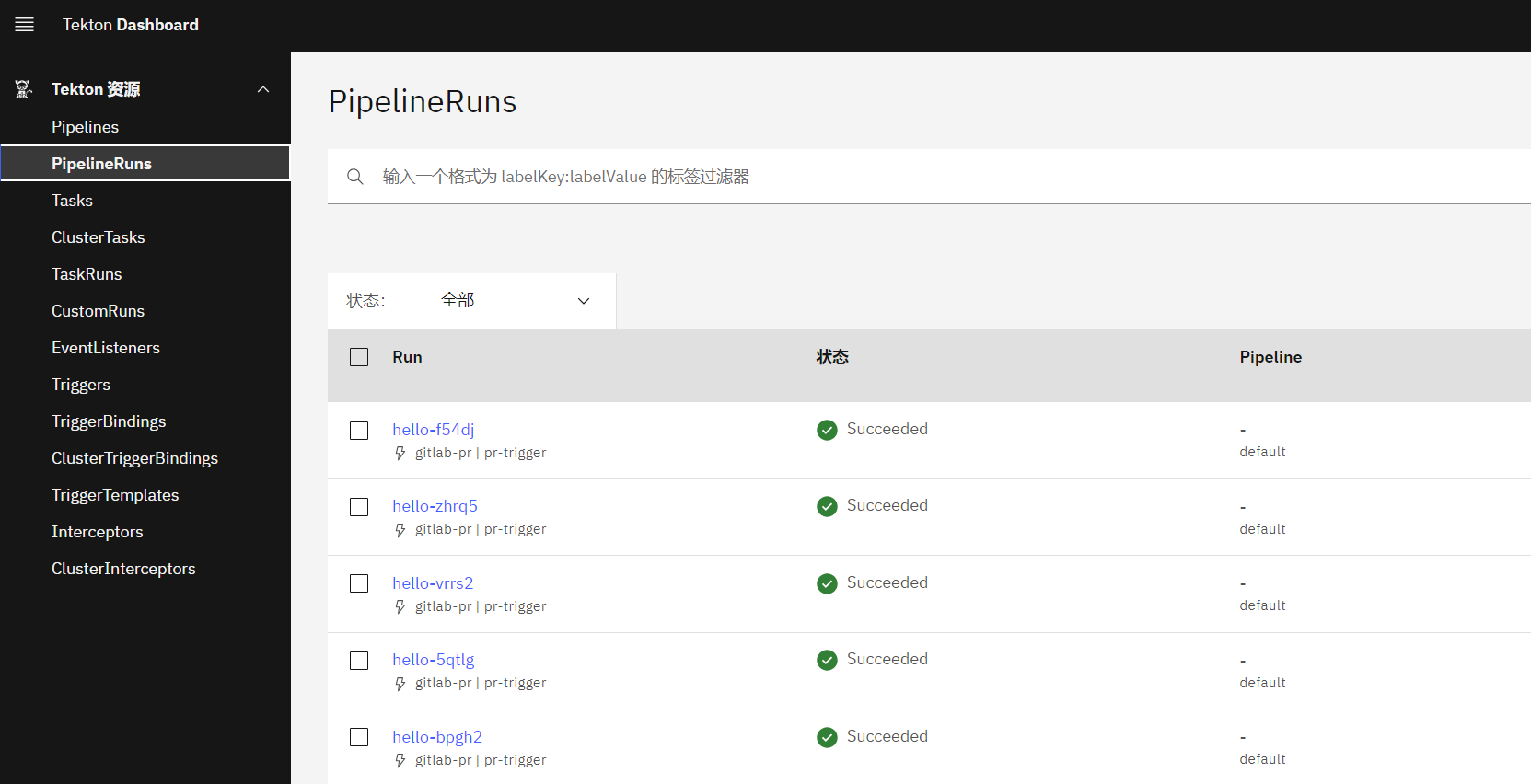
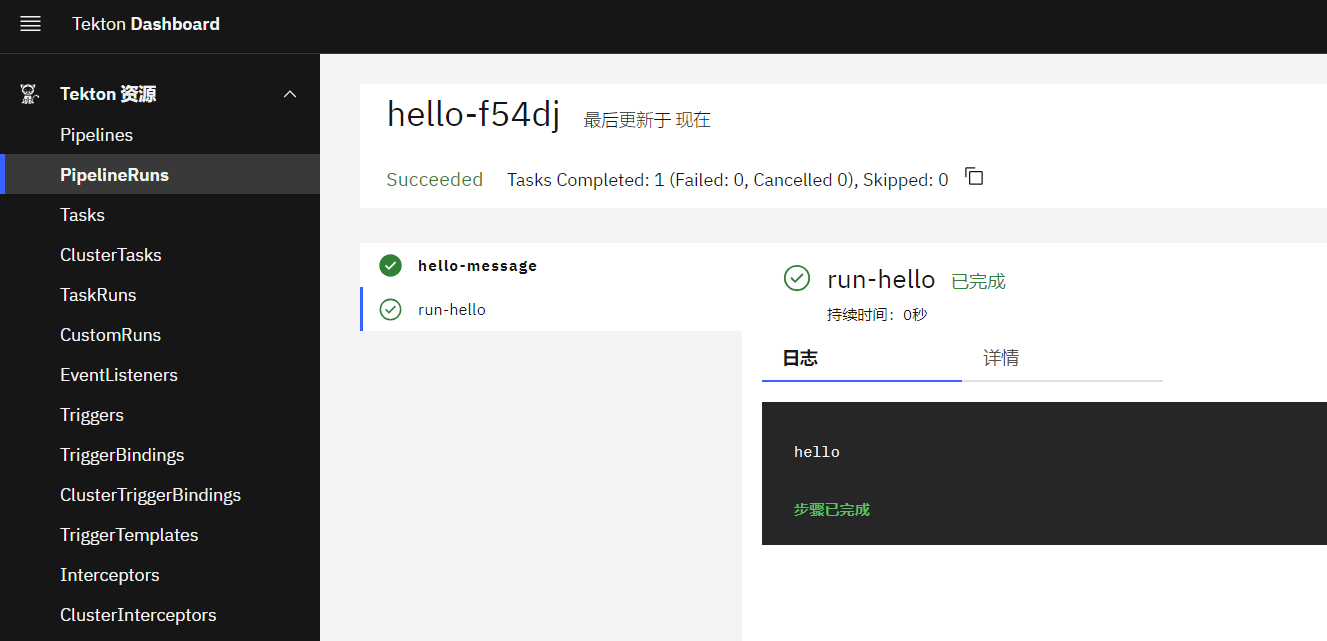
任务详情
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!