Tekton 构建容器镜像
2023-12-17 04:53:26
Tekton 构建容器镜像
介绍如何使用 Tektonhub 官方 kaniko task 构建docker镜像,并推送到远程dockerhub镜像仓库。

kaniko task yaml文件下载地址:https://hub.tekton.dev/tekton/task/kaniko
查看kaniko task yaml内容:

点击Install,选择一种方式创建 task
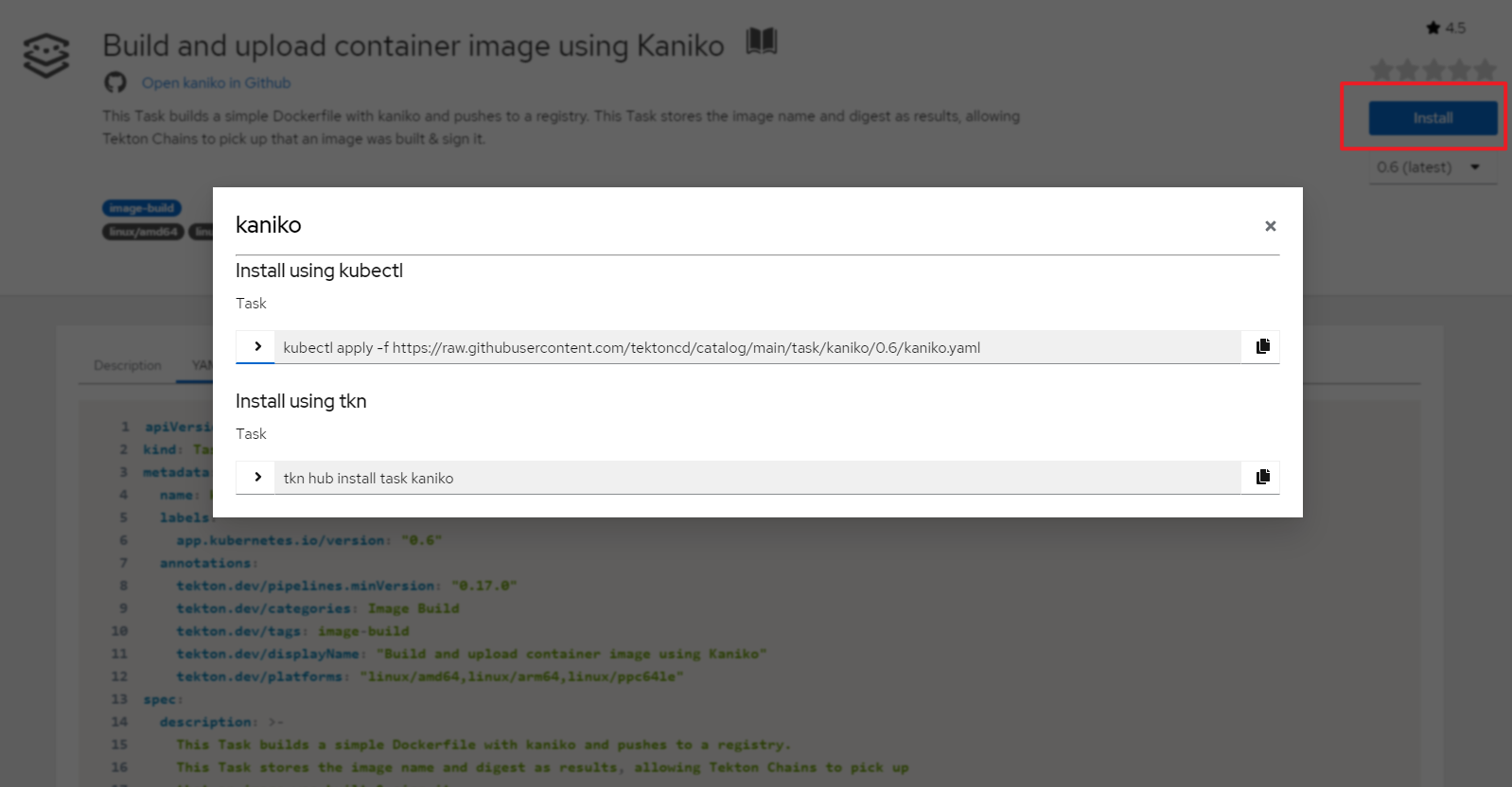
这里使用kubectl命令创建官方kaniko task
kubectl apply -f \
https://raw.githubusercontent.com/tektoncd/catalog/main/task/kaniko/0.6/kaniko.yaml
在执行镜像构建前Dockerfile存放在git仓库中,需要将代码克隆到本地,因此也需要安装git-clone task,安装方式类似。
kubectl apply -f \
https://raw.githubusercontent.com/tektoncd/catalog/main/task/git-clone/0.9/git-clone.yaml
查看创建的task
$ kubectl get task
NAME AGE
git-clone 25h
kaniko 13h
Task创建后,可以通过taskRun或pipelineRun进行调用。
配置dockerhub认证
镜像构建完成后自动推送到dockerhub,需要为dockerhub配置认证信息。
安装jq工具
apt install -y jq
生成config.json,替换docker-username和docker-password为您的值。
kubectl create secret docker-registry dockerhub \
--docker-server=https://index.docker.io/v1/ \
--docker-username=<your-docker-username> \
--docker-password=<your-docker-password> \
--dry-run=client -o json | jq -r '.data.".dockerconfigjson"' | base64 -d > /tmp/config.json
基于config.json创建secret
kubectl create secret generic docker-config --from-file=/tmp/config.json
创建serviceaccount,绑定到secret
$ cat serviceaccount.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: build-bot
secrets:
- name: docker-config
应用yaml文件
kubectl apply -f serviceaccount.yaml
创建pipeline和pipelinerun
官方示例pipeline:https://github.com/tektoncd/catalog/blob/main/task/kaniko/0.6/tests/run.yaml
该pipeline 首先运行git clone task,从https://github.com/kelseyhightower/nocode.git 克隆代码,然后运行kaniko task 基于根目录的Dockerfile文件构建镜像,并推送到dockerhub。
$ cat kaniko-run.yaml
apiVersion: tekton.dev/v1beta1
kind: Pipeline
metadata:
name: kaniko-test-pipeline
spec:
workspaces:
- name: shared-workspace
- name: docker-config
params:
- name: repo-url
type: string
description: The git repository URL to clone from.
- name: branch-name
type: string
description: The git branch to clone.
- name: gitInitImage
type: string
description: The gitInitImage params.
- name: httpProxy
type: string
description: The httpProxy params.
- name: httpsProxy
type: string
- name: dockerfile
type: string
description: reference of the image to build
- name: builder-image
type: string
description: reference of the image to build
- name: image
type: string
description: reference of the image to build
tasks:
- name: fetch-repository
taskRef:
name: git-clone
workspaces:
- name: output
workspace: shared-workspace
params:
- name: url
value: $(params.repo-url)
- name: revision
value: $(params.branch-name)
- name: gitInitImage
value: $(params.gitInitImage)
- name: httpProxy
value: $(params.httpProxy)
- name: httpsProxy
value: $(params.httpsProxy)
- name: kaniko
taskRef:
name: kaniko
runAfter:
- fetch-repository
workspaces:
- name: source
workspace: shared-workspace
- name: dockerconfig
workspace: docker-config
params:
- name: DOCKERFILE
value: $(params.dockerfile)
- name: IMAGE
value: $(params.image)
- name: BUILDER_IMAGE
value: $(params.builder-image)
- name: verify-digest
runAfter:
- kaniko
params:
- name: digest
value: $(tasks.kaniko.results.IMAGE_DIGEST)
taskSpec:
params:
- name: digest
steps:
- name: bash
image: ubuntu
script: |
echo $(params.digest)
case .$(params.digest) in
".sha"*) exit 0 ;;
*) echo "Digest value is not correct" && exit 1 ;;
esac
- name: verify-url
runAfter:
- kaniko
params:
- name: url
value: $(tasks.kaniko.results.IMAGE_URL)
taskSpec:
params:
- name: url
steps:
- name: bash
image: ubuntu
script: |
echo $(params.url)
case .$(params.url) in
*"/kaniko-nocode") exit 0 ;;
*) echo "URL value is not correct" && exit 1 ;;
esac
---
apiVersion: tekton.dev/v1beta1
kind: PipelineRun
metadata:
generateName: kaniko-test-pipeline-run-
spec:
serviceAccountName: build-bot
pipelineRef:
name: kaniko-test-pipeline
params:
- name: repo-url
value: https://github.com/kelseyhightower/nocode.git
- name: branch-name
value: master
- name: gitInitImage
#value: gcr.io/tekton-releases/github.com/tektoncd/pipeline/cmd/git-init:latest
value: dyrnq/tektoncd-pipeline-cmd-git-init:latest
- name: httpProxy
value: http://192.168.72.1:7890/
- name: httpsProxy
value: http://192.168.72.1:7890/
- name: dockerfile
value: ./Dockerfile
- name: image
value: docker.io/willdockerhub/kaniko-nocode
- name: builder-image
# value: gcr.io/kaniko-project/executor:v1.5.1@sha256:c6166717f7fe0b7da44908c986137ecfeab21f31ec3992f6e128fff8a94be8a5
value: docker.io/bitnami/kaniko:latest
workspaces:
- name: shared-workspace
volumeClaimTemplate:
spec:
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 1Gi
- name: docker-config
secret:
secretName: docker-config
参数说明:
- gitInitImage:执行git clone任务的镜像,官方镜像无法访问,推荐在docekrhub中查找替代镜像
- builder-image:执行kaniko 构建任务的镜像,官方镜像无法访问,推荐在docekrhub中查找替代镜像
- serviceAccountName:指定
serviceAccountName用于认证 - shared-workspace:用于在不同任务之间共享数据,PipelineRun中定义了
volumeClaimTemplate类型的workspaces,能够动态申请所需的持久卷,使用kubectl get storageclass命令,确认k8s集群有默认可用的storageclass资源可用,本示例输出为openebs-hostpath (default) - docker-config workspace:用于dockerhub认证的secret卷,将secret中的
config.json挂载到/kaniko/.docker下
应用yaml文件
kubectl create -f kaniko-run.yaml
查看pipelinerun执行结果
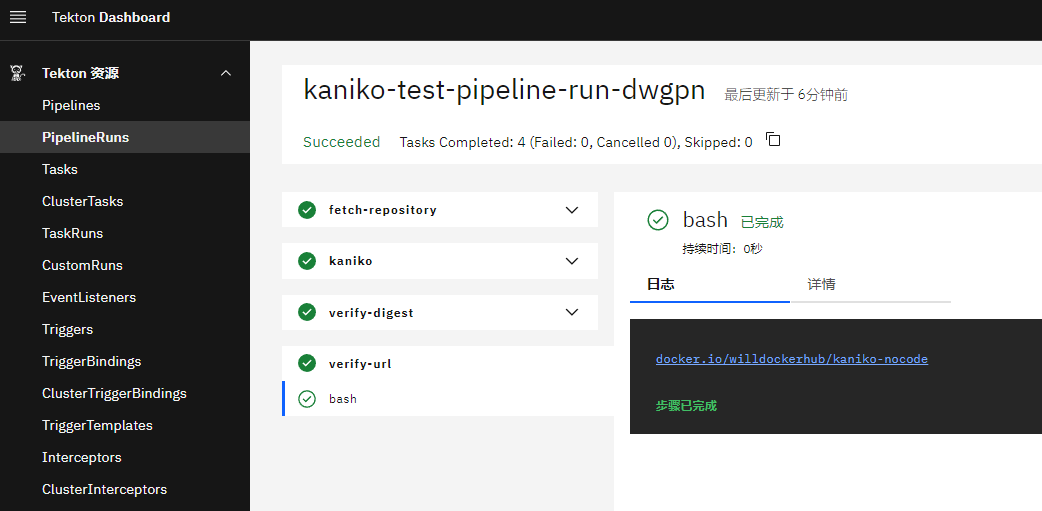
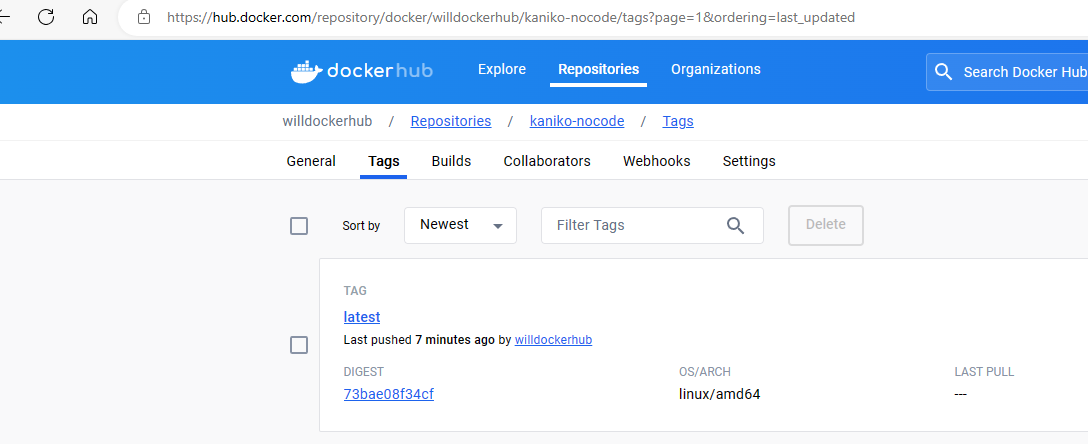
查看镜像构建结果
文章来源:https://blog.csdn.net/networken/article/details/135030018
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!