Harbor
Harbor
文章目录
1. 概述
Harbor是VMware公司开源的企业级Docker Registry 项目,其目标是帮助用户迅速搭建一个 企业级的Docker Registry 服务。虽然Docker官方提供了公共的镜像仓库,但是从安全和效率等方面考虑,部署企业自己的私有镜像仓库也是非常必要的。
Harbor以docker公司开源的registry为基础,提供了管理UI,基于角色的访问控制(Role Based Access Control),AD/LDAP集成,以及审计日志(Auditlogging)等企业用户需求的功能,同时还原生支持中文。
Harbor的每个组件都是以Docker容器的形式构建的,使用docker-compose来对它进行部署;用于部署Harbor的docker-compose模板位于/usr/local/bin/harbor/docker-compose.yml(自定义);Docker harbor有可视化的web管理界面,可以方便管理Docker镜像,又提供了多个项目的镜像权限管理及控制功能。
1.1 harbor的优势:
(1)基于角色控制:有管理员与普通用户,可赋权普通用户,比如只能上传和下载,可根据项目来进行操作和管理。
(2)基于镜像的复制策略:镜像可以在多个Harbor实例之间进行复制(同步)。
(3)支持LDAP/AD:Harbor 可以集成企业内部有的AD/LDAP (类似数据库的一-张表),用于对已经存在的用户认证和管理。
(4)镜像删除和垃圾回收:镜像可以被删除,也可以回收镜像占用的空间。
(5)图形化用户界面:用户可以通过浏览器来浏览,搜索镜像仓库以及对项目进行管理。
(6)审计管理:所有针对镜像仓库的操作都可以被记录追溯,用于审计管理。
(7)支持RESTful API:RESTful API提供给管理员对于Harbor 更多的操控,使得与其它管理软件集成变得更容易。
(8)Harbor和docker registry的关系:Harbor实质上是对docker registry做了封装,扩展了自己的业务模板。
1.2 harbor的核心组件:
Harbor在架构上主要有Proxy、 Registry、 Core services、 Database ( Harbor-db)、Log collector ( Harbor-log)、Job services六个组件。
(1)Proxy:这是一个反向代理组件;Harbor 的Registry、UI、Token 服务等组件,都处在nginx 反向代理后边。该代理将来自浏览器、docker clients .的请求转发到后端不同的服务上。
(2)Registry:负责储存Docker 镜像,并处理Docker push/pull 命令;由于要对用户进行访问控制,即不同用户对Docker镜像有不同的读写权限,Registry 会指向一个Token 服务,强制用户的每次Docker pull/push 请求都要携带一个合法的Token,Registry会通过公钥对Token 进行解密验证。
(3)Core services: Harbor的核心功能,主要提供以下3个服务:
UI (harbor-ui) :提供图形化界面,帮助用户管理Registry. 上的镜像(image) ,并对用户进行授权。
WebHook:网站的一些服务功能,为了及时获取Registry.上 image状态变化的情况,在Registry上配置Webhook, 把状态变化传递给UI模块。
Token 服务:令牌,提供身份验证服务,负责根据用户权限给每个Docker push/pull 命令签发Token。 Docker 客户端向Registry 服务发起的请求,如果不包含Token, 会被重定向到Token 服务,获得Token 后再重新向Registry 进行请求。
(4)Database (harbor-db) :为core services提供数据库服务,负责储存用户权限、审计日志、Docker镜像分组信息等数据。
(5)Job services:主要用于镜像复制,本地镜像可以被同步到远程Harbor实例上。
(6)Log collector (harbor-log) :负责收集其他组件的日志到一个地方。
Harbor的每个组件都是以Docker 容器的形式构建的,因此,使用Docker Compose 来对它进行部署。通过在docker- compose . yml所在目录中执行docker-compose ps命令来查看。
1.3 harbor主要功能及优势
基于角色的访问控制
用户与Docker镜像仓库通过“项目”进行组织管理,一个用户可以对多个镜像仓库在同一命名空间(project)里有不同的权限。
基于镜像的复制策略
镜像可以在多个Registry实例中复制(可以将仓库中的镜像同步到远程的Harbor,类似于MySQL主从同步功能),尤其适合于负载均衡,高可用,混合云和多云的场景。
图形化用户界面
用户可以通过浏览器来浏览,检索当前Docker镜像仓库,管理项目和命名空间。
支持 AD/LDAP
Harbor可以集成企业内部已有的AD/LDAP,用于鉴权认证管理。
镜像删除和垃圾回收
Harbor支持在Web删除镜像,回收无用的镜像,释放磁盘空间。image可以被删除并且回收image占用的空间。
审计管理
所有针对镜像仓库的操作都可以被记录追溯,用于审计管理。
RESTful API
RESTful API 提供给管理员对于Harbor更多的操控, 使得与其它管理软件集成变得更容易。
部署简单
提供在线和离线两种安装工具, 也可以安装到vSphere平台(OVA方式)虚拟设备。
1.4 harbor的简易架构:
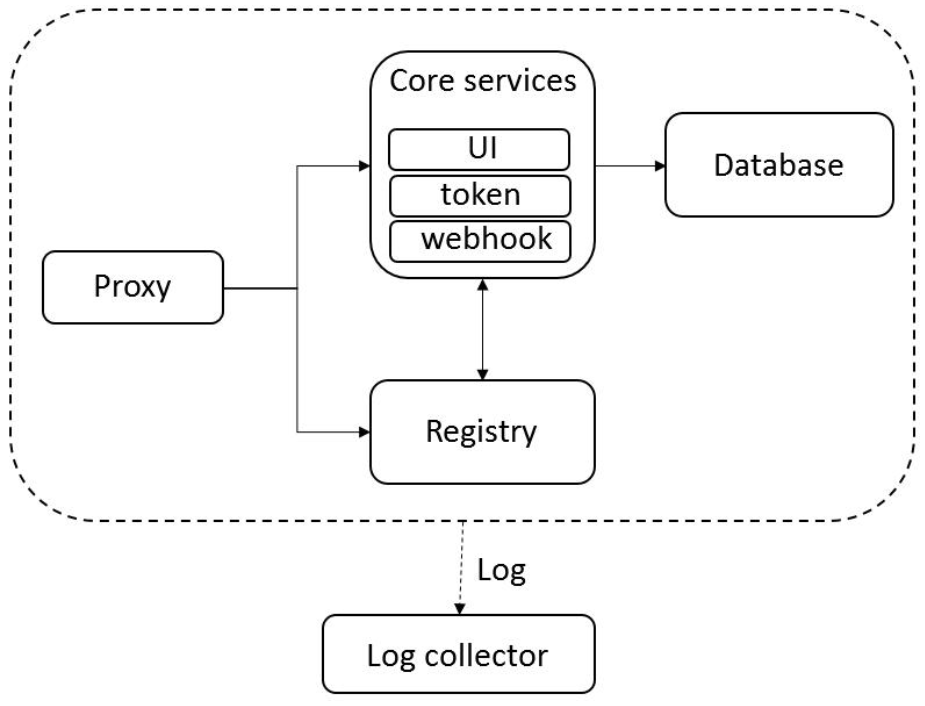
如图所示:
所有的请求都经过proxy代理,proxy代理转发给Core services和Registry,其中Core services包括UI界面、token令牌和webhook网页服务功能,Registry主要提供镜像存储功能。如果要进行下载上传镜像,要经过token令牌验证然后从Registry获取或上传镜像,每一次下载或上传都会生成日志记录,会记入Log collector,而用户身份权限及一些镜像语言信息会被存储在Database中。
2、部署
| os/ip | server | 备注 |
|---|---|---|
| centos8/192.168.207.13 | docker(24.0.5)、docker-compose(v2.23.2)、Harbor(v2.10.0) | 私有镜像仓库 |
| centos8/192.168.207.15 | docker(24.0.5) | 验证私有镜像仓库可用性 |
Harbor下载地址:https://github.com/docker/compose/releases/download/v2.23.2/docker-compose-linux-x86_64
docker-compose下载地址: https://github.com/goharbor/harbor/releases/download/v2.10.0/harbor-offline-installer-v2.10.0.tgz
2.1 docker部署
docker部署可查看 http://t.csdnimg.cn/mcLuB
2.2 Docker-Compose 部署
[root@docker opt]# ls
docker-compose-linux-x86_64
[root@docker opt]# ln -s /opt/docker-compose-linux-x86_64 /usr/local/bin/docker-compose # 将下载资源上传至服务器并做软连接
[root@docker opt]# chmod +x /opt/docker-compose-linux-x86_64 # 赋予 x 权限
[root@docker opt]# docker-compose -v # 查看版本
Docker Compose version v2.23.2
2.3 Harbor 部署
[root@docker opt]# tar -xf harbor-offline-installer-v2.10.0.tgz
[root@docker opt]# cd harbor
[root@docker harbor]# ll
total 631180
-rw-r--r--. 1 root root 3643 Dec 14 14:39 common.sh
-rw-r--r--. 1 root root 646285764 Dec 14 14:39 harbor.v2.10.0.tar.gz
-rw-r--r--. 1 root root 13761 Dec 14 14:39 harbor.yml.tmpl
-rwxr-xr-x. 1 root root 1975 Dec 14 14:39 install.sh
-rw-r--r--. 1 root root 11347 Dec 14 14:39 LICENSE
-rwxr-xr-x. 1 root root 1882 Dec 14 14:39 prepare
[root@docker harbor]# cp harbor.yml.tmpl harbor.yml
[root@docker harbor]# vi harbor.yml
hostname: 192.168.207.13 # 服务器IP或域名
# http related config
http:
# port for http, default is 80. If https enabled, this port will redirect to https port
port: 80
# 将下面https加上注释
# https related config
#https:
# https port for harbor, default is 443
# port: 443
# The path of cert and key files for nginx
# certificate: /your/certificate/path
# private_key: /your/private/key/path
database:
# The password for the root user of Harbor DB. Change this before any production use.
password: root123 # 数据存储密码
# The initial password of Harbor admin
# It only works in first time to install harbor
# Remember Change the admin password from UI after launching Harbor.
harbor_admin_password: zhurs@123 # 登录密码
# The default data volume
data_volume: /data/harbor/data # 数据存储路径(无需手动创建)
log:
# options are debug, info, warning, error, fatal
level: info
# configs for logs in local storage
local:
# Log files are rotated log_rotate_count times before being removed. If count is 0, old versions are removed rather than rotated.
rotate_count: 50
# Log files are rotated only if they grow bigger than log_rotate_size bytes. If size is followed by k, the size is assumed to be in kilobytes.
# If the M is used, the size is in megabytes, and if G is used, the size is in gigabytes. So size 100, size 100k, size 100M and size 100G
# are all valid.
rotate_size: 200M
# The directory on your host that store log
location: /data/harbor/logs # 日志路径(需手动创建,否则报错无法找打路径)
[root@docker harbor]# mkdir -pv /data/harbor/logs
mkdir: created directory '/data'
mkdir: created directory '/data/harbor'
mkdir: created directory '/data/harbor/logs'
[root@docker harbor]# ./prepare
prepare base dir is set to /opt/harbor
WARNING:root:WARNING: HTTP protocol is insecure. Harbor will deprecate http protocol in the future. Please make sure to upgrade to https
Generated configuration file: /config/portal/nginx.conf
Generated configuration file: /config/log/logrotate.conf
Generated configuration file: /config/log/rsyslog_docker.conf
Generated configuration file: /config/nginx/nginx.conf
Generated configuration file: /config/core/env
Generated configuration file: /config/core/app.conf
Generated configuration file: /config/registry/config.yml
Generated configuration file: /config/registryctl/env
Generated configuration file: /config/registryctl/config.yml
Generated configuration file: /config/db/env
Generated configuration file: /config/jobservice/env
Generated configuration file: /config/jobservice/config.yml
Generated and saved secret to file: /data/secret/keys/secretkey
Successfully called func: create_root_cert
Generated configuration file: /compose_location/docker-compose.yml
Clean up the input dir
[root@docker harbor]# ./install.sh
Note: stopping existing Harbor instance ...
[Step 5]: starting Harbor ...
[+] Running 10/10
? Network harbor_harbor Created 0.2s
? Container harbor-log Started 0.5s
? Container redis Started 1.3s
? Container registryctl Started 1.3s
? Container harbor-portal Started 1.4s
? Container registry Started 1.1s
? Container harbor-db Started 1.0s
? Container harbor-core Started 1.5s
? Container harbor-jobservice Started 1.8s
? Container nginx Started 1.8s
? ----Harbor has been installed and started successfully.----
[root@docker harbor]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
8d80c0118575 goharbor/harbor-jobservice:v2.10.0 "/harbor/entrypoint.…" 10 seconds ago Up 5 seconds (health: starting) harbor-jobservice
ec8e2cd37307 goharbor/nginx-photon:v2.10.0 "nginx -g 'daemon of…" 10 seconds ago Up 7 seconds (health: starting) 0.0.0.0:80->8080/tcp, :::80->8080/tcp nginx
64eb3a4b7bd3 goharbor/harbor-core:v2.10.0 "/harbor/entrypoint.…" 10 seconds ago Up 7 seconds (health: starting) harbor-core
b7a4a7266180 goharbor/registry-photon:v2.10.0 "/home/harbor/entryp…" 10 seconds ago Up 8 seconds (health: starting) registry
832b7c7ff807 goharbor/harbor-registryctl:v2.10.0 "/home/harbor/start.…" 10 seconds ago Up 8 seconds (health: starting) registryctl
a89dfbfaf94d goharbor/harbor-db:v2.10.0 "/docker-entrypoint.…" 10 seconds ago Up 8 seconds (health: starting) harbor-db
4a5e96c456c4 goharbor/harbor-portal:v2.10.0 "nginx -g 'daemon of…" 10 seconds ago Up 8 seconds (health: starting) harbor-portal
de4f0455f4d1 goharbor/redis-photon:v2.10.0 "redis-server /etc/r…" 10 seconds ago Up 8 seconds (health: starting) redis
75a3dc9f0154 goharbor/harbor-log:v2.10.0 "/bin/sh -c /usr/loc…" 10 seconds ago Up 8 seconds (health: starting) 127.0.0.1:1514->10514/tcp harbor-log
[root@docker harbor]# docker-compose ps
NAME IMAGE COMMAND SERVICE CREATED STATUS PORTS
harbor-core goharbor/harbor-core:v2.10.0 "/harbor/entrypoint.…" core 18 seconds ago Up 16 seconds (health: starting)
harbor-db goharbor/harbor-db:v2.10.0 "/docker-entrypoint.…" postgresql 18 seconds ago Up 16 seconds (health: starting)
harbor-jobservice goharbor/harbor-jobservice:v2.10.0 "/harbor/entrypoint.…" jobservice 18 seconds ago Up 13 seconds (health: starting)
harbor-log goharbor/harbor-log:v2.10.0 "/bin/sh -c /usr/loc…" log 18 seconds ago Up 17 seconds (health: starting) 127.0.0.1:1514->10514/tcp
harbor-portal goharbor/harbor-portal:v2.10.0 "nginx -g 'daemon of…" portal 18 seconds ago Up 16 seconds (health: starting)
nginx goharbor/nginx-photon:v2.10.0 "nginx -g 'daemon of…" proxy 18 seconds ago Up 16 seconds (health: starting) 0.0.0.0:80->8080/tcp, :::80->8080/tcp
redis goharbor/redis-photon:v2.10.0 "redis-server /etc/r…" redis 18 seconds ago Up 16 seconds (health: starting)
registry goharbor/registry-photon:v2.10.0 "/home/harbor/entryp…" registry 18 seconds ago Up 16 seconds (health: starting)
registryctl goharbor/harbor-registryctl:v2.10.0 "/home/harbor/start.…" registryctl 18 seconds ago Up 16 seconds (health: starting)
3 验证
3.1 可用性验证
浏览器输入http://162.14.76.192/
登录用户:admin
登录密码:zhurs@123

3.2 功能性验证
# Docker 客户端配置 Harbor 私服连接
[root@localhost ~]# cat > /etc/docker/daemon.json << EOF
> { "insecure-registries":["192.168.207.13"] }
> EOF
# 重启 Docker 客户端
[root@localhost ~]# systemctl daemon-reload
[root@localhost ~]# systemctl restart docker
# Docker 客户端登录 Harbor 私服
[root@localhost ~]# docker login -u admin -p zhurs@123 192.168.207.13
WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
# 任意 pull 一个测试镜像
[root@localhost ~]# docker pull busybox
Using default tag: latest
latest: Pulling from library/busybox
a307d6ecc620: Pull complete
Digest: sha256:ba76950ac9eaa407512c9d859cea48114eeff8a6f12ebaa5d32ce79d4a017dd8
Status: Downloaded newer image for busybox:latest
docker.io/library/busybox:latest
[root@localhost ~]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
busybox latest 9211bbaa0dbd 8 days ago 4.26MB
# 将该镜像打 tag 并 push 到 Harbor 镜像仓库
[root@localhost ~]# docker tag busybox:latest 192.168.207.13/library/busybox:v1.0
[root@localhost ~]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
192.168.207.13/library/busybox v1.0 9211bbaa0dbd 8 days ago 4.26MB
busybox latest 9211bbaa0dbd 8 days ago 4.26MB
[root@localhost ~]# docker push 192.168.207.13/library/busybox:v1.0
The push refers to repository [192.168.207.13/library/busybox]
82ae998286b2: Pushed
v1.0: digest: sha256:7de5fa822a9d1e507c36565ee0cf50c08faa64505461c844a3ce3944d23efa35 size: 527
在 Harbor web 界面看看 push 的镜像
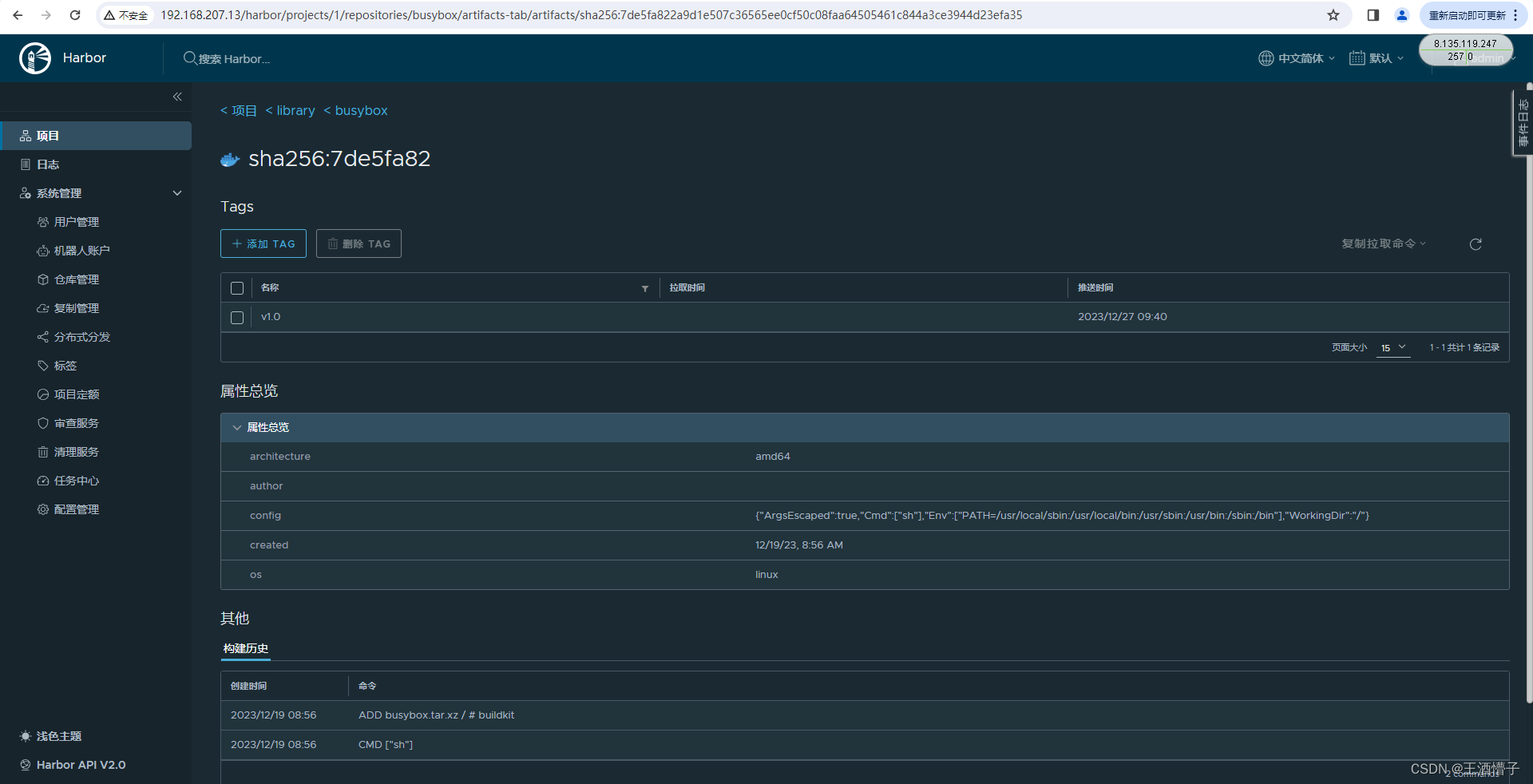
# 删除本地镜像,并 pull 远程 Harbor 仓库镜像
[root@localhost ~]# docker rmi busybox:latest
Untagged: busybox:latest
Untagged: busybox@sha256:ba76950ac9eaa407512c9d859cea48114eeff8a6f12ebaa5d32ce79d4a017dd8
[root@localhost ~]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
192.168.207.13/library/busybox v1.0 9211bbaa0dbd 8 days ago 4.26MB
[root@localhost ~]# docker rmi 192.168.207.13/library/busybox:v1.0
Untagged: 192.168.207.13/library/busybox:v1.0
Untagged: 192.168.207.13/library/busybox@sha256:7de5fa822a9d1e507c36565ee0cf50c08faa64505461c844a3ce3944d23efa35
Deleted: sha256:9211bbaa0dbd68fed073065eb9f0a6ed00a75090a9235eca2554c62d1e75c58f
Deleted: sha256:82ae998286b2bba64ce571578647adcabef93d53867748d6046cc844ff193a83
[root@localhost ~]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
[root@localhost ~]# docker pull 192.168.207.13/library/busybox:v1.0
v1.0: Pulling from library/busybox
a307d6ecc620: Pull complete
Digest: sha256:7de5fa822a9d1e507c36565ee0cf50c08faa64505461c844a3ce3944d23efa35
Status: Downloaded newer image for 192.168.207.13/library/busybox:v1.0
192.168.207.13/library/busybox:v1.0
[root@localhost ~]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
192.168.207.13/library/busybox v1.0 9211bbaa0dbd 8 days ago 4.26MB
可通过 web 界面看到我们的操作日志
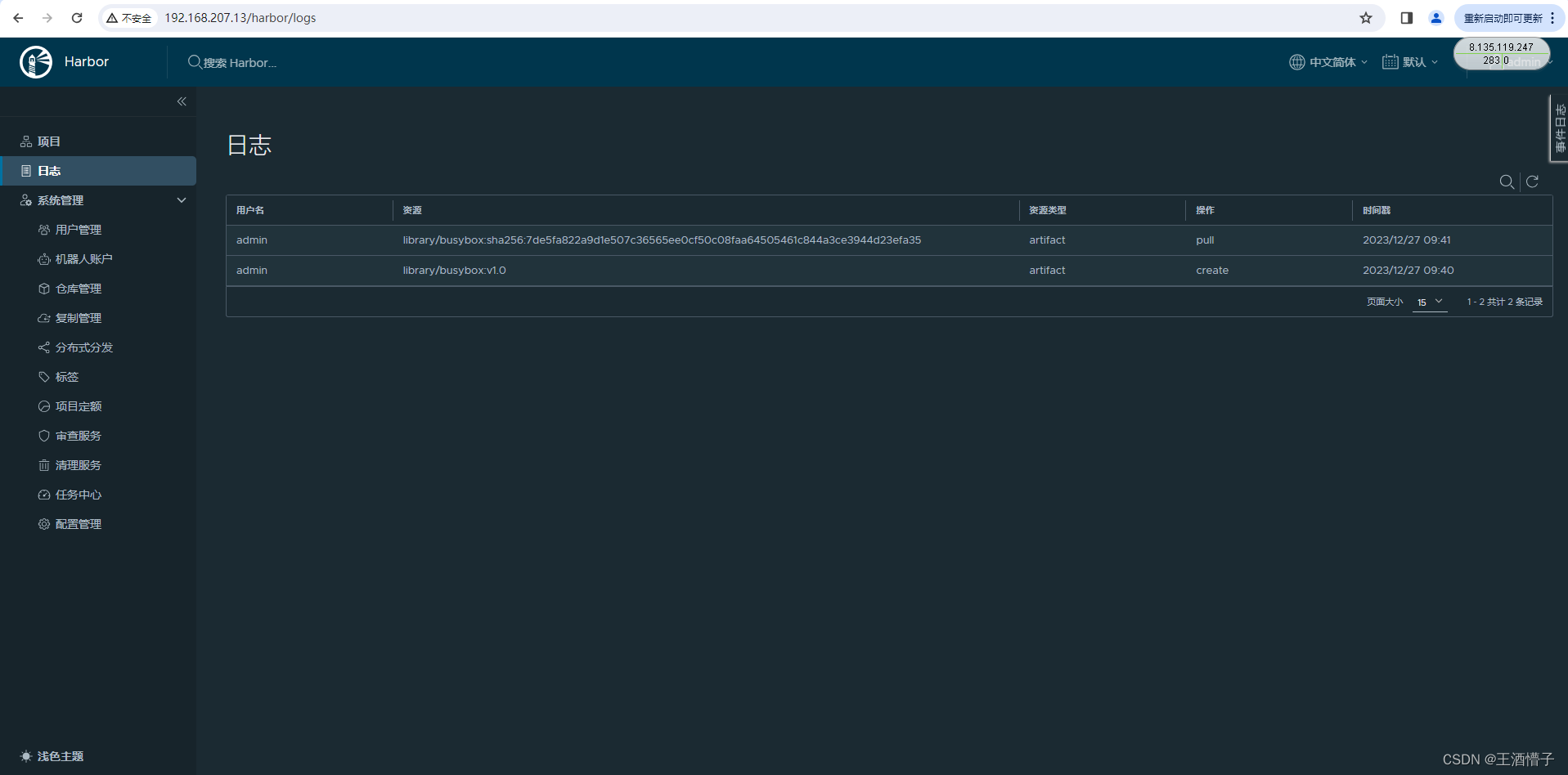
本文来自互联网用户投稿,该文观点仅代表作者本人,不代表本站立场。本站仅提供信息存储空间服务,不拥有所有权,不承担相关法律责任。 如若内容造成侵权/违法违规/事实不符,请联系我的编程经验分享网邮箱:veading@qq.com进行投诉反馈,一经查实,立即删除!